End-user security awareness has never been harder or more important. A single AI-generated phishing email or a convincingly cloned voice on a phone call can move even a tech-savvy employee to make a costly mistake.
Firewalls don't falter, but people do, and attackers know exactly how to take advantage of that gap. The real challenge isn't teaching employees what a cyber threat is; it's helping them consistently make safer decisions when the pressure is on.
That's where the conversation needs to evolve. Security teams aren't looking for another set of generic modules or one-size-fits-all "best practices." They need a security awareness program that adapts to roles, risk profiles, and organizational maturity—and that actually shifts behavior.
This guide brings a practical lens to the problem of modern threats, real-world scenarios, and a clearer path to maturing your security awareness training program and achieving measurable human risk reduction.
What is end-user security awareness?
End-user security awareness is the practice of helping employees understand the specific cyber threats they face in their day-to-day work and how their decisions can either reduce or amplify risk. A modern security awareness training program goes beyond generic cybersecurity training, which often focuses on broad concepts like:
- Firewall defense
- Authentication
- Network defenses
End-user security awareness centers on the human layer, including the behaviors, habits, and split-second choices that influence an organization's overall security posture. Those choices matter. Year after year, breach reports from Verizon and IBM show that human error, social engineering, and misdelivery are among the most common root causes of security incidents. A single click, approval, or shortcut can bypass millions of dollars of cybersecurity controls in an instant.
Awareness alone doesn't create resilience. Knowing what phishing, malware, or social engineering looks like is only the starting point. That's why phishing awareness training, simulations, and ongoing reinforcement are critical.
The goal is measurable behavior change, where employees who recognize real-world threats respond correctly under pressure and consistently reduce human risk across the business. In a security awareness maturity model, this shift from knowledge to behavior is what distinguishes a basic, check-the-box training program from a mature, risk-driven one.
The new threat landscape: AI, deepfakes, and human risk

Here are a few ways attackers are using AI to amplify the impact of end-user security awareness gaps and expose weaknesses in your security awareness program:
- Generative AI phishing campaigns: Phishing emails now mirror internal communication styles, reference real projects, and use flawless language. Attackers can generate thousands of targeted phishing attacks in seconds, making even well-trained employees hesitate.
- Vishing and deepfake impersonations: Voice-cloning tools can replicate an executive's tone and cadence, enabling high-pressure phone scams that push employees to share sensitive information or approve fraudulent payments.
- CEO fraud and identity scams: Deepfake video, spoofed messages, and AI-crafted social engineering tactics make it harder than ever to verify who's who, especially in remote or hybrid environments.
The issue isn't that organizations lack cybersecurity defenses like firewalls or endpoint protection. It's that attackers are bypassing them entirely by targeting people. Legacy security awareness programs, especially those relying on annual training cycles, simply can't keep pace since threats evolve weekly, not yearly, and often stall at an early maturity stage.
Adaptive Security's simulations replicate real AI-driven attack vectors, from deepfake vishing attempts to advanced phishing campaigns. Employees learn to recognize and respond to threats they'll actually face. This turns phishing awareness training and your broader security awareness training program into real-world, role-based practice rather than generic modules.
Why traditional security awareness programs fail
Most organizations still rely on a security awareness training program that was designed for a very different threat landscape. Static modules, outdated examples, and annual refreshers don't prepare employees for modern social engineering, AI-generated phishing attacks, or fast-moving cyber threats, and they keep the organization stuck at a low maturity stage.
Here's where traditional programs fall short:
1. Over-reliance on static modules and canned videos
Content doesn't evolve with the threat landscape, so employees end up learning yesterday's attacks instead of today's tactics, especially when phishing awareness training templates don't reflect current, AI-enhanced threats.
2. Training frequency too low for real retention
A once-a-year security awareness training program, or a single phishing awareness training campaign, won't hold up against sophisticated phishing emails, ransomware lures, or social engineering attacks that employees encounter weekly.
3. One-size-fits-all content
Different roles face different risks. Finance teams deal with CEO fraud, developers handle sensitive data, and frontline staff face credential-harvesting scams. Generic modules don't address these variations or the behavior patterns behind them, keeping the security awareness program in a one-size-fits-all maturity stage.
4. Programs measure completion, not impact
Many security awareness training programs celebrate 100% training completion, yet can't answer key questions:
- Are risky behaviors decreasing?
- Are phishing simulations improving?
- Which teams are most vulnerable to cyberattacks?
- Is human risk actually going down?
End-user awareness must evolve from a series of "training events" into an ongoing behavioral intelligence system, one that continuously measures, reinforces, and adapts to how employees actually behave. This is how security teams move up the security awareness maturity model and build resilience, not just compliance.
Building role-based and risk-based awareness programs
Modern end-user security awareness programs can't succeed with one-size-fits-all training. Different teams face different threats, operate under different pressures, and engage with sensitive information in unique ways.
To build a security awareness program that truly reduces human risk and matures over time, security teams need to tailor both content and reinforcement based on role, risk level, and exposure to real-world cyber threats.
Here are two practical approaches that move organizations beyond generic modules and into adaptive, behavior-driven security awareness training.
1. Tailor by role
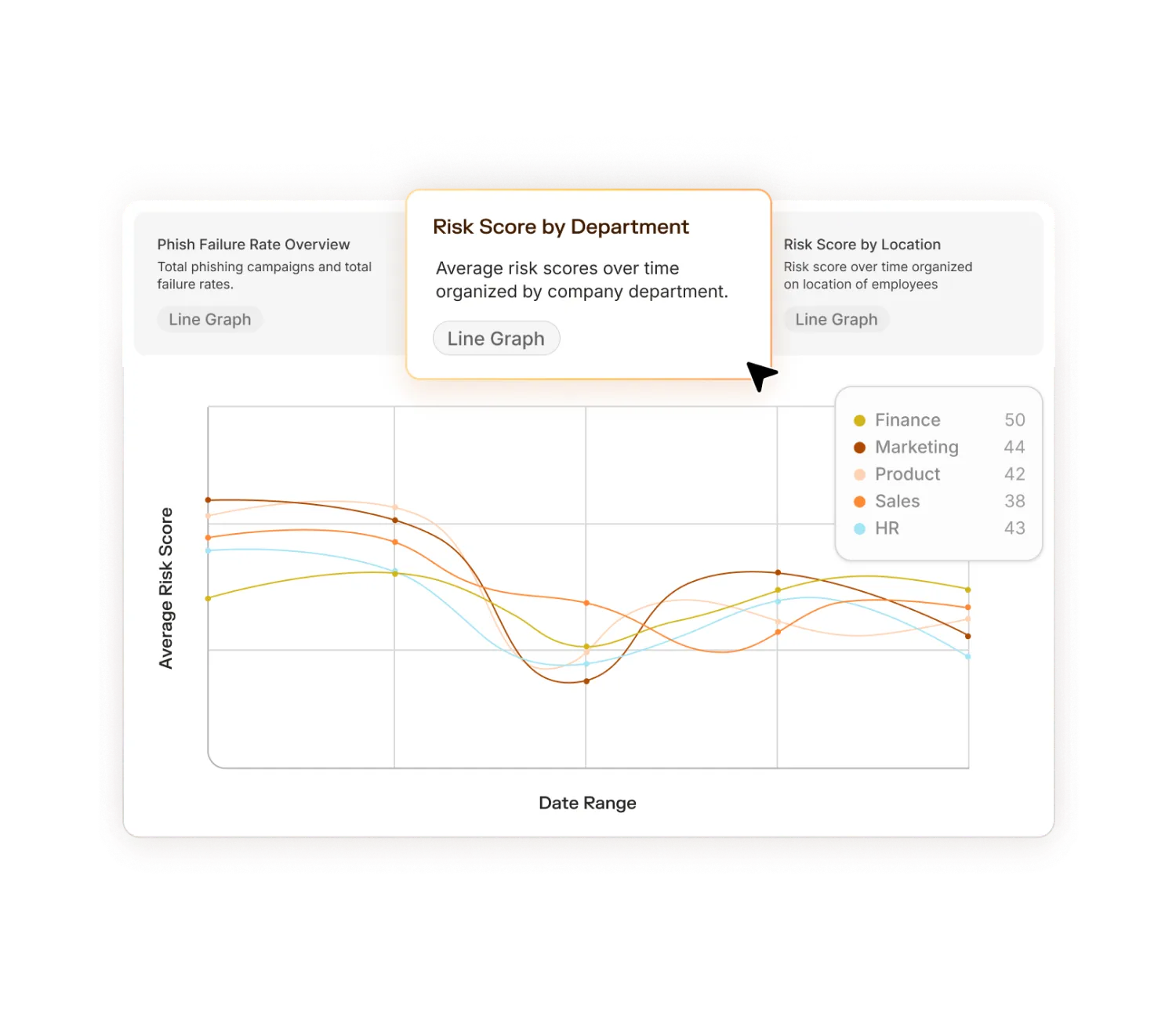
Every department interacts with cyber threats differently. Your security awareness program should reflect those realities instead of relying on broad cybersecurity concepts that apply to "everyone but no one in particular."
Role-based security awareness training ensures each learner sees realistic scenarios, not generic phishing examples, so behavior change sticks. For many organizations, this starts with targeted phishing awareness training and evolves into broader, multi-channel simulations as the program matures.
Here's how role-based training can elevate security posture and reduce vulnerabilities:
Finance teams
Finance is one of the highest-risk groups due to constant exposure to payment workflows and sensitive data. Some of the notable threats here include:
- Invoice and payment fraud
- CEO fraud and business email compromise (BEC)
- AI-generated spear phishing referencing deals, vendors, or open POs
- Deepfake voice requests impersonating executives
Why it matters: A single approval under pressure can trigger costly downtime, fraudulent transfers, and reportable data breaches. Phishing awareness training for finance teams should mirror real approval chains, vendor interactions, and executive escalations.
Developers & engineering
Developers often have elevated privileges, access to code repositories, and control over production environments. As a result, the following threats may arise:
- Code repo leaks (GitHub, GitLab, shadow IT tools)
- Credential harvesting and MFA fatigue attacks
- Insider-risk scenarios involving API keys or secrets
- Vulnerabilities introduced through third-party libraries
Why it matters: Attackers increasingly target developers because compromising one engineer can compromise the entire environment. A mature security awareness training program includes developer-specific simulations, covering code repositories, secrets management, and MFA fatigue, not just generic phishing tests.
Executives & senior leadership
Executives represent high-value targets due to their authority, visibility, and public-facing roles. This opens the possibilities of the following attacks:
- Deepfake impersonation (video and vishing)
- Social engineering leveraging board updates, mergers and acquisitions (M&A) projects, or investor communications
- Tailored phishing attacks with threat intelligence-level reconnaissance
Why it matters: A successful executive compromise can bypass every security control and trigger cascading business impact. Effective security awareness training for executives pairs realistic spear-phishing and vishing simulations with brief, high-impact coaching tailored to their communication style and time constraints.
2. Tailor by risk level
Role alone isn't enough. Two employees with the same title can have wildly different susceptibility levels depending on their habits, past behavior, and exposure to potential threats. That's where risk-based segmentation becomes essential, and where a basic security awareness training program begins to mature into a true human risk management capability.
Use behavioral analytics to identify high-risk users
Instead of treating every employee the same, security teams can segment learners based on:
- Phishing simulation performance
- Click rates and credential submission patterns
- Engagement with security measures (password hygiene, MFA, reporting behavior)
- Frequency of interacting with sensitive data or critical systems
This creates dynamic risk tiers, including low, medium, and high, that guide more precise interventions.
Reinforce learning for repeat offenders
Some employees demonstrate consistent risky behaviors, not because they don't understand cyber threats, but because habits are hard to break. Effective reinforcement includes:
- Immediate, contextual micro-training after risky actions
- More frequent phishing simulations with real-time coaching
- Role-specific scenarios that mirror the tasks they struggle with
- Positive reinforcement for improving over time
This approach transforms punitive models into supportive ones that drive measurable behavior change and marks a clear step up in your security awareness maturity model.
Adaptive example: Simulations that adjust automatically
Adaptive Security's platform uses real-time risk scoring to tailor training to each learner in the following ways:
- Employees who fall for CEO fraud see more executive impersonation scenarios.
- Developers who mishandle code secrets receive targeted modules on secure repo practices.
- High-risk users get more frequent, on-demand training sessions and phishing awareness training tailored to their weaknesses.
- Departments receive simulations reflective of their most common attack patterns.
The result is a security awareness training program that meets people where they are in the maturity model, improving decision-making and reducing human error across the organization.
Adaptive transforms end-user security awareness with department-specific, risk-driven simulations that reinforce learning and reduce real-world threats. See how it works.
Measuring human risk and behavior change
The success of an end-user security awareness program shouldn't be measured by training completion alone. Completion tells you who watched a module, not who can identify phishing emails, respond to social engineering attacks, or make safer decisions under pressure.
In most security awareness maturity models, moving up a level means shifting from activity metrics to behavior metrics.
To build a resilient security culture and a mature security awareness program, organizations need KPIs that reflect real behavior change and reduced human risk, not just activity.
Here are the KPIs that go beyond training completion alone:
- Click rate reduction: Fewer employees fall for simulated phishing attempts over time.
- Phishing report rate: Increased reporting shows proactive vigilance.
- Time-to-detect: See how quickly teams identify suspicious activity.
- Department risk scores: Track which groups require targeted intervention.
These indicators provide a more accurate view of your organization's security posture and highlight where targeted security measures are needed.
The human risk management framework
To turn awareness into resilience, organizations benefit from a structured loop that also serves as a roadmap for maturing their security awareness training program, including:
- Awareness: Educate employees on role-specific and risk-based threats.
- Measurement: Track behavioral KPIs and human risk scores.
- Intervention: Deliver adaptive retraining or coaching to at-risk employees.
- Resilience: Strengthen organizational security posture through measurable behavior change.
This continuous loop aligns training with actual behavior, closing the gap between cybersecurity knowledge and real-world decision-making and moving the program toward higher maturity stages.
How modern platforms track human risk
Advanced platforms, including Adaptive Security's real-time analytics, allow security teams to:
- Monitor individual and department risk scores
- Identify patterns in social engineering susceptibility
- See trends in phishing simulations and reporting
- Trigger automatic, contextual reinforcement for risky behavior
- Visualize improvements in human risk over time
This shift from static modules to dynamic human risk intelligence empowers security teams to design smarter interventions that actually reduce vulnerability and clearly demonstrate security awareness program maturity to stakeholders.
Real-world scenarios of effective end-user awareness training
Theory is powerful—but results speak louder. Effective end-user awareness programs deliver measurable outcomes:
1. Dallas Mavericks
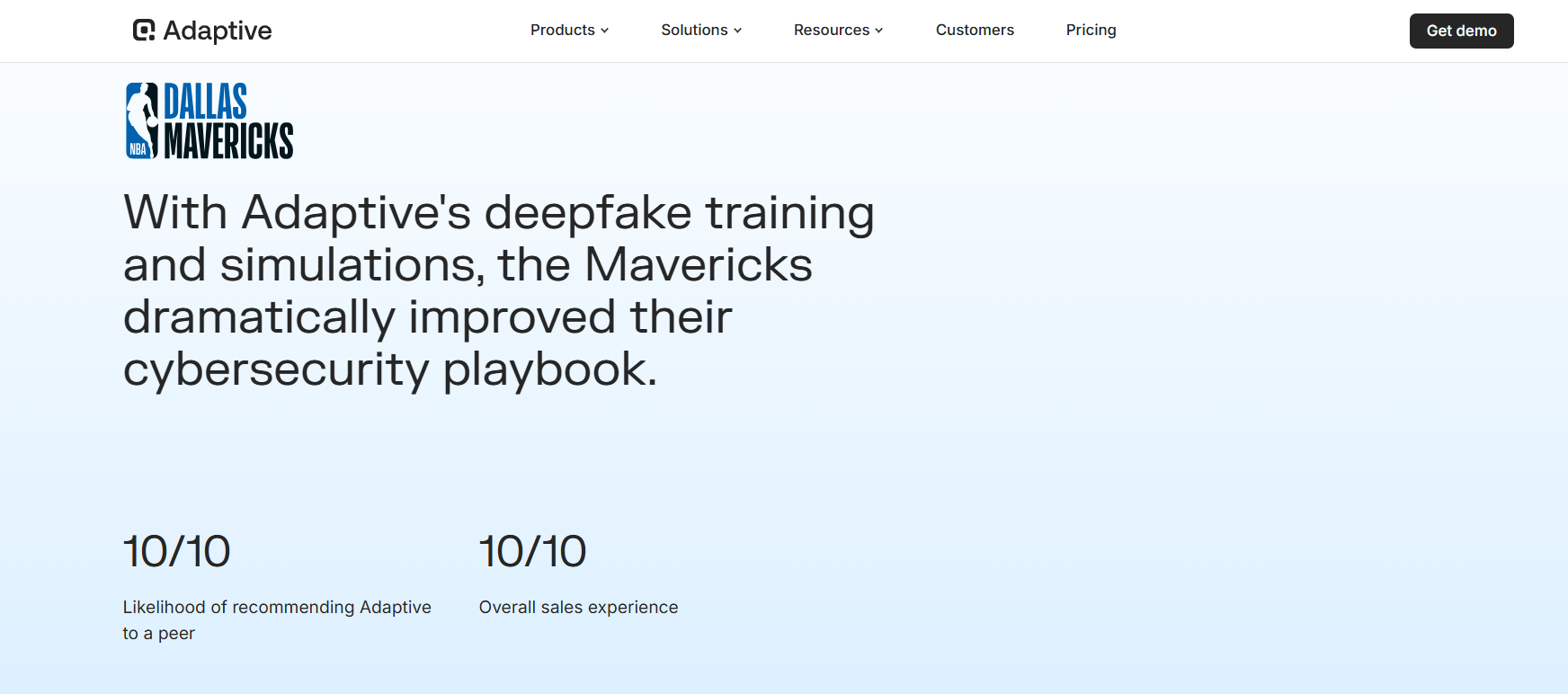
The Mavericks used Adaptive Security's deepfake video and voice simulations as part of their phishing awareness training to prepare staff for executive impersonation and AI-powered social engineering.
Result: Employees reported vishing attempts more quickly, and the organization significantly raised its phishing-report rate as awareness changed behavior.
2. First State Bank

First State Bank adopted Adaptive Security's AI-generated deepfake phishing and voice simulations to prepare employees for sophisticated, AI-driven threats as part of a broader security awareness training program.
Outcome: The bank gained detailed visibility into employee risk scores and training progress, enabling targeted interventions and a more mature, resilient security awareness program.
3. Mohonk Mountain House

Mohonk Mountain House leveraged Adaptive Security's deepfake and AI-driven simulations to train staff across all channels, including email, voice, and SMS, elevating their phishing awareness training and overall security awareness program.
Impact: The hotel achieved 100% training completion for the first time, reduced employee fail rates to 3%, and strengthened the organization's overall security posture.
The future of end-user security awareness
Human error continues to be the leading cause of security breaches and data loss. As cybercriminals adopt AI, automation, and increasingly sophisticated social engineering tactics, the gap between traditional training and real-world threats will only widen.
The future of end-user security awareness requires a human-centric security model driven by real-world simulations, behavioral analytics, and adaptive, risk-based interventions, all embedded in a continuously improving security awareness training program.
Here's where the industry is heading:
- Hyper-personalized simulations based on role, risk score, and exposure
- Real-time behavioral feedback loops that reinforce learning at the moment of risk
- AI-driven threat modeling that tailors security training to emerging attack patterns
- Organization-wide human risk dashboards that measure resilience, not just compliance
- Training sessions that mimic live cyberattacks, from deepfake vishing to cloud compromise scenarios
Adaptive Security is at the forefront of this shift. By simulating modern threats like AI-crafted phishing campaigns, deepfake impersonation, vishing attacks, and real-world social engineering tactics, Adaptive helps organizations evolve their phishing awareness training and broader security awareness program from basic compliance to a mature, behavior-driven model.
Request a demo to see how Adaptive helps teams turn risky actions into measurable improvements with role-specific simulations that power a modern security awareness program, not one-size-fits-all training.
FAQs about end-user security awareness
What's the difference between end-user awareness and security training?
The difference between end-user security awareness and security training is that awareness programs focus on everyday behaviors, while training focuses on cybersecurity knowledge and compliance requirements.
End-user security awareness helps employees recognize and respond to phishing, social engineering, and other real-world threats, making it behavior-driven. Security training, on the other hand, covers policies, controls, and general cybersecurity concepts, making it knowledge- and compliance-driven.
How do you measure improvement in end-user awareness?
You measure improvement in end-user security awareness by tracking behavior-based KPIs rather than just course completion.
Key metrics include:
- Reduced phishing click and credential-submission rates
- Higher phishing and suspicious-activity reporting rates
- Faster time-to-detect and respond to potential incidents
- Improved department and individual human risk scores
- Fewer security incidents tied to human error
Modern platforms use real-time analytics to monitor these signals and trigger targeted interventions.
What's an example of an effective end-user simulation?
An effective end-user security awareness simulation closely mimics a real cyber threat employees could actually face and tests how they respond under pressure. For example, an AI-generated phishing email referencing a real internal project or vendor, and a deepfake vishing call pretending to be an executive requesting an urgent payment or data access.
Strong simulations are role-based, adjust to each user's risk level, and provide contextual micro-training immediately after risky actions to drive long-term behavior change.




As experts in cybersecurity insights and AI threat analysis, the Adaptive Security Team is sharing its expertise with organizations.
Contents










