Social engineering ranks among the top three causes of data breaches in 13 of 16 industries, according to Verizon’s 2025 Data Breach Investigations Report. This serves as a clear reminder that the most drastic vulnerabilities in cybersecurity aren’t technical, they’re human.
Cybercriminals exploit trust, urgency, and routine to manipulate people into divulging sensitive data, transferring funds, or clicking on a malicious link. Firewalls and AI tools can filter traffic, but they can’t read intention or judgment. That’s where the human firewall comes in—a workforce trained to recognize manipulation and respond thoughtfully.
This guide provides a step-by-step approach to building a firewall, from assessing behavioral risk and implementing targeted training to tracking measurable improvements.
What is a human firewall?
A human firewall is created when your workforce acts consistently and purposefully to prevent, detect, and report cyber threats that technology alone can miss. Every employee is an active control, able to spot suspicious requests, handle data correctly, and escalate anything that feels “off.” A human firewall contains incidents early and strengthens your organization’s security posture.
The precursors of human firewall programs were limited to pushing password memorization rules and forcing employees to attend annual cybersecurity training sessions. Today’s programs, however, are behavior-driven with regular lessons, realistic simulations, role-based guidance, and real-time feedback. The result is cybersecurity awareness that’s instinctive and fosters a culture of security.
This evolution matters because attackers have adapted faster than most security measures. Their new playbook targets people first by manipulating trust, urgency, and curiosity through malicious emails, fake links, and impersonation attempts.
In one notable case, Toyota Boshoku, a major auto-parts supplier, lost $37 million after an attacker posed as a senior executive via email. This shows how even routine communication can bypass advanced defenses if employees aren’t trained in proper verification.
Here are the most common people-targeted security threats you could face:
- AI-phishing & deepfakes: convincing emails, voice clones of executives, synthetic videos
- SMS fraud (smishing) & messaging-app lures: urgent payment or OTP requests
- MFA fatigue & push-bombing: repeated prompts that trick users into approving logins
- QR-based and drive-by payloads: malicious QR codes and fake download prompts
- Business Email Compromise (BEC): convincing, legitimate-looking emails that often come from real accounts or trusted contacts, with no malicious links or attachments, designed to exploit trust and timing
The 4 pillars of a strong human firewall
An organization needs a step-by-step approach to identify new-age cybersecurity human errors trends and build a resilient human firewall. These four pillars form the foundation for lasting security awareness and measurable behavior change.
1. Role-based training that reflects real risk
Generic security training treats everyone the same; attackers don’t. A finance employee is a bigger target for invoice scams than a developer because they routinely authorize vendor payments. Similarly, a customer support representative faces more social-engineering attempts than a system administrator since they interact with outsiders all day.
New-gen security awareness training platforms like Adaptive Security design lessons and simulations that cater to each department’s responsibilities. Finance teams practice identifying fraudulent invoices, IT teams learn to manage privilege escalation attempts, and executives train to verify requests that appear urgent or confidential.
2. Simulation depth: beyond phishing emails
“Simulation depth” means going beyond simple phishing tests to recreate the full range of real-world attack tactics employees face every day. Attackers exploit every communication touchpoint, from fake IT calls and spoofed Slack messages to malicious QR codes. A strong human firewall recognizes these social engineering attacks, regardless of their format.
Modern simulation programs need to test how employees respond across multiple channels and contexts, not just email inboxes, but also texts, calls, chats, and collaboration platforms. Research supports this multi-layered approach.
In a 2024 study by Thai researchers on a critical infrastructure organization, 10.9% of employees fell for a simulated phishing email the first time. After targeted awareness training, that number dropped to just 1.4% in a follow-up test with different content. This demonstrates how repeated, varied simulations build stronger instincts against social engineering.
That’s exactly the kind of reinforcement Adaptive Security delivers. Its multi-channel simulations mirror real-world attack patterns, allowing employees to practice identifying threats in safe and realistic conditions.
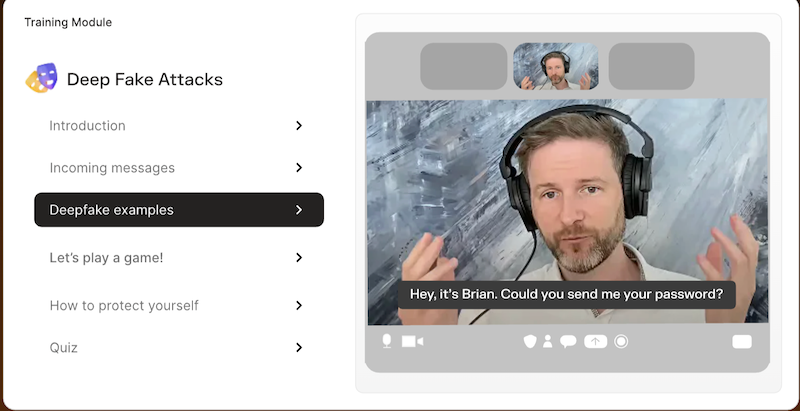
Imagine your finance team receives a simulated Slack message from a “CFO” requesting an urgent vendor payment. Adaptive tracks responses, delivers instant coaching, and helps employees learn to identify such a cyberattack and report it before a real attacker ever tries the same trick.
3. Company culture: security is everyone’s job
Technology and phishing training only work when the company culture supports it. Security should feel like part of daily behavior, not merely a compliance exercise.
Strong organizations build a culture where:
- Leaders model secure habits and prioritize awareness.
- Employees report suspicious activity quickly and without fear of blame.
- The company celebrates the wins, from catching phishing attempts to improving team metrics.
4. Measurable behavioral change
Your security program is just a checkbox if it can’t show improvement. The fourth pillar of a strong human firewall involves measuring real behavior shifts to determine if the phishing risks are actually being lowered.
Effective metrics include phishing simulation click rates, reporting rates, time-to-report real incidents, training completion, and more. Real change is about reducing risk, not just lowering click rates. Over time, those behavioral indicators should align with fewer security incidents, faster containment, and lower remediation costs.
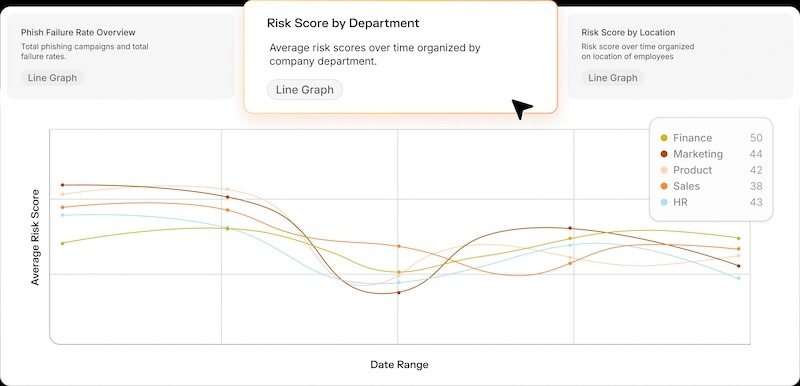
Adaptive Security tracks and benchmarks user behavior across departments, locations, and roles, assigning each group a dynamic risk score based on performance in training, simulations, and reporting activity.
The platform lets you compare scores before and after targeted awareness campaigns to determine whether risky behaviors are declining and which teams require additional support.
Building your human firewall: a step-by-step framework
This framework helps you build a sustainable human firewall that evolves in tandem with your organization, adapting to different types of phishing cyberattacks as they emerge over time.
1. Assess behavioral risk by department
Before you can strengthen your human firewall, you need to identify the gaps. Every organization has departments with varying levels of exposure and threat profiles—finance teams face invoice fraud and payment scams, HR handles sensitive personal data, and IT or executives are frequent targets of phishing and credential theft.
Start by mapping where human risk is highest, not just where technical controls are weakest. This will help you focus training and simulations where they’ll have the greatest impact.
Here are some quick ways to assess behavioral risk effectively:
- Review incident and simulation data: Identify which teams historically click or fail to report simulated attacks most often. Adaptive’s reporting of risk scores can help here.
- Consider role and access level: The more sensitive the data or permissions a team holds, the higher the human risk.
- Consider the volume and type of communication: Departments handling external contacts (such as sales, HR, and support) are more susceptible to phishing and social engineering attempts.
- Factor in turnover and new hires: New employees are statistically more likely to fall victim to phishing scams during their first few months of employment.
Don’t overlook direct employee feedback. Surveys and interviews can help identify areas of confusion or overconfidence in handling suspicious messages.
2. Define KPIs beyond completion rates
Completion rates are a starting metric, but they don’t tell you whether behavior changed. Track metrics such as:
- Phishing-simulation click/failure rates and miss rates (people who neither clicked nor reported)
- Reporting rates (the number of employees who report suspicious emails)
- Time to report real or simulated incidents
- Quiz or assessment scores (knowledge retention)
- Trend of actual security incidents or policy violations linked to human error
Together, these metrics help identify which teams are improving fastest and where more reinforcement is needed. You can then set clear departmental KPIs (e.g., aiming for a click rate under 5% or a report rate above 60% within 24 hours).
Adaptive lets you measure the platform’s risk score alongside these indicators to see whether each department’s overall risk level is trending downward. If click rates drop and reporting improves, your score will reflect that progress, helping you prove measurable behavior change.
3. Roll out role-based training modules
Generic modules may raise awareness, but they rarely change daily habits because each team faces different types of social engineering.
The most effective programs focus on real situations employees encounter in their specific roles, such as:
- Finance staff learning to spot invoice fraud, vendor-payment spoofing, and urgent CRO impersonation frauds requesting wire transfers
- HR teams recognizing social-engineering attempts hidden in job applications or fake candidate outreach
- IT and development teams strengthening habits around software-supply-chain risks, privileged access, and credential hygiene
4. Layer in simulations and just-in-time learning
Run realistic simulations across multiple channels after training, including emails, SMS, phone, messaging apps, QR scans, and collaboration tools. Vary the scenario content and mix formats, tone, and senders to keep employees alert and ensure their reactions come from awareness, not familiarity.
For example, if every phishing test mimics a delivery notification, employees will easily spot that email, but might still fall for a fake HR request or a deepfake video message that tries to steal sensitive information.
When someone fails or makes an error, deliver just-in-time learning, including concise, contextual feedback that appears immediately after the action. If an employee clicks a simulated phishing link, the platform can display a short message explaining the cues they missed and what to look out for next time.
Providing feedback at the moment of risk helps reinforce awareness and turn a mistake into a lasting lesson, reducing the chance of future security breaches or unauthorized access attempts.
5. Monitor, iterate, and celebrate secure behaviors
Start by regularly checking your metrics, including click rates on phishing tests, the speed at which employees report suspicious emails, and whether everyone completes their training on time. Compare these numbers to your starting point to see what’s actually improving.
If one department continues to make progress, acknowledge it by sharing quick wins in team meetings or sending a short internal message to thank them. When people see their efforts being noticed, they stay motivated to maintain those habits.
If another group is falling behind, don’t scold them. Instead, look for patterns. Maybe they’re busier than most or missing reminders. Run a smaller round of focused training for that team or resend a simulation with a clearer setup.
Continue to connect what you see in the data to what’s happening day-to-day. For example, if employees are reporting suspicious emails more quickly than before, that should also be reflected in fewer actual phishing incidents. If not, examine the reports more closely to see if they’re reaching the intended recipients and if the follow-up process requires adjustment.
Measuring the strength of a human firewall
To gauge the effectiveness of your efforts to build a robust human firewall and to identify areas for continuous improvement, it’s essential to track relevant metrics.
Key performance indicators (KPIs) for a human firewall might include:
- Phishing simulation click rates: Strive for a decreasing trend in the percentage of users who click on links, open attachments, or complete another incorrect action in a phishing simulation.
- Incident reporting rates: An increase in employees reporting suspicious activity, even if they turn out to be false positives, can signal heightened awareness and engagement.
- Training completion and assessment scores: Track participation in training modules and performance on knowledge checks to determine engagement and success.
- Time to report real incidents: Employees act more quickly to report actual cyber incidents.
- Observed behavioral changes: While more qualitative, noting tangible improvements in secure practices across the organization indicates success.
Tracking metrics consistently provides actionable insights into the efficacy of the human firewall and pinpoints areas for improvement.
Common challenges with a human firewall (and how to fix them)
Human elements still introduce vulnerabilities, despite the efforts of IT and security teams to build a human firewall. Therefore, it’s critical to recognize common challenges and know how to address them.
“It won’t happen to me” is an attitude that poses a considerable threat. Overconfidence or a belief that an individual is not an attractive target can lead employees to let their guard down. The solution lies in continuous awareness initiatives that use relatable, real-world examples and consistently highlight that everyone, regardless of role, is a potential target.
Information overload and alert fatigue are also legitimate concerns. Constant warnings or overly complex security procedures can result in employees becoming desensitized or seeking risky workarounds. To counter this, streamline communications and focus on actionable advice.
A fear of reporting errors can also undermine security efforts. If employees anticipate negative consequences for reporting a mistake or admitting they fell for a phishing attack, they’re far less likely to come forward quickly (or at all). Nurture a no-blame culture for reporting, instead emphasizing early detection and swift reporting to minimize potential impact.
Outdated knowledge also weakens the human firewall. The threat landscape changes at an incredible speed, and training content that doesn’t keep pace with new attack methods inevitably leaves employees unprepared. The solution is to invest in a partner like Adaptive Security, which continuously updates content and simulations that reflect current threats.
Poor password hygiene and the neglect of multi-factor authentication remain significant and easily exploitable entry points for attackers. Your organization should enforce robust password policies, thoroughly educate employees on the critical importance of MFA, and actively promote the adoption of reputable password managers.
How Adaptive Security can help you build and sustain a human firewall
Building a human firewall isn’t about one training session or an annual awareness week, but rather a continuous cycle of learning, testing, and improvement. When people know what to look for, have space to practice safely, and receive real-time feedback, secure behavior becomes automatic, creating a more holistic and resilient security posture.
Adaptive Security brings together every part of this framework in one place, including role-based training, multi-channel simulations, and behavioral analytics. You can see which departments are improving, which need support, and exactly how risk is changing over time.
If you’re ready to turn security awareness into measurable resilience, schedule a demo to see how your organization can build and sustain an optimized human firewall.
FAQs about human firewalls
Why are human firewalls so crucial for security?
Most breaches still start with people, not code. Technology can block known threats, but attackers continually invent new tricks to fool even cautious employees, like deepfake videos of executives, fake MFA prompts, QR code scams, and realistic Slack or Teams messages.
A strong human firewall builds everyday habits that catch these subtler manipulations. Employees learn to pause before acting on an unusual request, verify its source, and use company channels to confirm its authenticity. Those small, consistent actions stop social engineering attacks before they cause damage.
Is security awareness training enough to build a human firewall?
Not on its own. Training builds knowledge, but behavior only changes with practice, feedback, and reinforcement. A true human firewall comes from combining ongoing education, realistic simulations, and a supportive culture where everyone feels responsible for security.
Training transforms awareness into a daily habit when it’s continuous, role-based, and supported by leadership. Tools like Adaptive Security help maintain this training with short, frequent learning and instant feedback after simulations.
How do you measure the strength of a human firewall?
Start with clear metrics, such as phishing click rates, report rates, and time-to-report suspicious activity. Over time, you’ll see whether these numbers improve and align with a decrease in actual incidents.
You can also measure qualitative shifts, like employees asking more questions, flagging unusual requests, or sharing security tips. Adaptive Security makes this easier by assigning risk scores by department or role, so you can see which areas are improving and where to focus next.




As experts in cybersecurity insights and AI threat analysis, the Adaptive Security Team is sharing its expertise with organizations.
Contents




%20(1).avif)





