Phishing remains one of the most persistent and costly security challenges facing organizations today. According to the Verizon 2025 Data Breach Investigations Report, phishing accounts for nearly 15% of breaches where attackers gained access through deliberate tactics. Put plainly, it’s one of the top three ways adversaries break into companies.
Beyond the “urgent email from IT,” today’s phishing campaigns can involve deepfake audio convincing a CFO to approve a wire transfer, text-based scams (smishing) luring employees to fake login portals, or voice phishing (vishing) calls that imitate trusted individuals. Attackers also use AI to scale these campaigns faster, with personalized hooks that bypass traditional red flags.
Employees need to know how to recognize subtle phishing signals, IT teams must prepare layered defenses, and security trainers should align awareness with reducing risk. This guide provides definitions, real-world examples, attack types, and the latest phishing trends, so you can strengthen your organization against one of today’s most dangerous threats.
What is phishing?
Phishing is a form of social engineering where attackers impersonate trusted sources—such as colleagues, vendors, or well-known brands—to trick individuals into revealing sensitive information or taking unsafe actions. This can include entering login credentials, downloading malicious files, or authorizing fraudulent payments.
While the first phishing attacks in the 1990s relied on crude email spam and fake login pages, the landscape has changed dramatically. What began as generic “Nigerian prince” emails has evolved into targeted, multi-channel deception. Criminals are now exploiting email, text (smishing), phone calls (vishing), social media, and even deepfake audio and video.
Modern phishing is no longer about clumsy grammar or suspicious addresses. Instead, attackers craft convincing campaigns tailored to specific employees or departments, making them dangerous and more difficult to detect. Understanding the types of phishing attacks is the first step toward building an informed, resilient workforce.
The most common types of phishing attacks
Phishing is not a single tactic, but an adaptable playbook that cybercriminals use across multiple channels. Each variant preys on human trust in different ways. Employees, IT staff, and security trainers must understand how these threats show up in real-world scenarios.
Email phishing
The most recognized form of phishing, email phishing, relies on fraudulent messages that appear to come from legitimate organizations. These suspicious emails often include urgent requests, such as resetting a password or confirming an invoice, and direct the recipient to a malicious link or attachment.
Phishing emails typically signal themselves through red flags, such as requests for confidential information, a manufactured sense of urgency, or inconsistencies in sender addresses and links. For example, an attacker posing as “IT Support” might send an email instructing employees to log in to a fake portal and harvest credentials for later use.

Spear phishing
Unlike broad email blasts, spear phishing targets specific individuals or departments with tailored messaging. Criminals may research a target’s role, responsibilities, and even social media presence to craft highly convincing lures.
Advances in AI have made these attacks even more difficult to detect, with phishers now able to automate reconnaissance and craft nearly flawless emails. AI-driven spear phishing is becoming a leading concern for defenders, as outlined in our analysis of open-source intelligence (OSINT) detection in phishing.
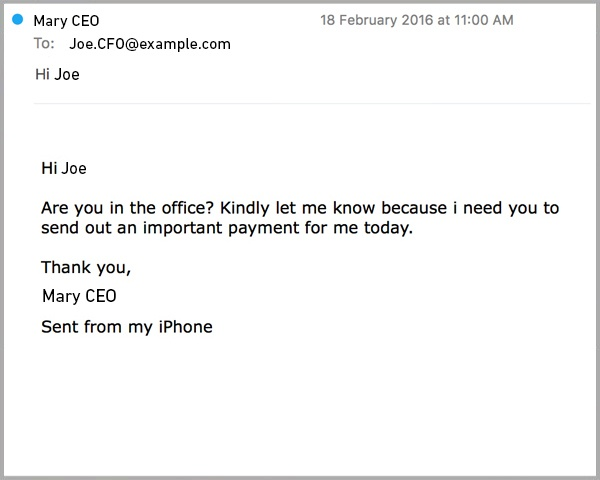
Smishing (SMS phishing)
Smishing uses text messages to trick victims into clicking on malicious links or disclosing personal information. These scams often impersonate delivery services, banks, or healthcare providers with messages like, “There’s been an issue delivering your package. Confirm details here.”
Employees may be more likely to trust SMS messages since they bypass corporate email filters, making mobile device training essential.

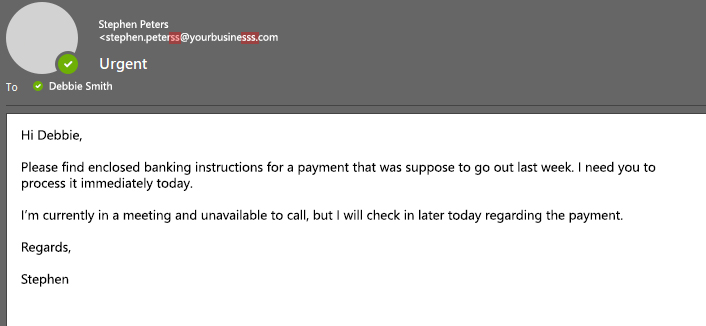
Vishing (voice phishing)
Vishing uses fraudulent phone calls to extract sensitive information or persuade employees to act. A common example is an attacker posing as a company’s help desk, convincing someone to reset their password or install remote access software.
With VoIP and caller ID spoofing, these calls can appear to come from legitimate internal numbers, dramatically increasing their success rate.
Deepfake phishing (AI-generated video/voice)
One of the newest and most dangerous evolutions, deepfake phishing uses synthetic audio or video to impersonate trusted leaders. Attackers might replicate a CFO’s voice to authorize a financial transfer or create a fake video message urging employees to open a malicious file.
As highlighted in our deepfake security awareness training tips, these scams bypass traditional “gut check” signals, requiring organizations to prepare employees for a future where seeing and hearing is no longer believing.

Whaling (CEO fraud)
Whaling is a specialized spear phishing attack aimed at executives and senior leaders. By impersonating high-ranking officials, often in finance or operations, attackers pressure staff into making wire transfers, sharing sensitive data, or approving fraudulent requests.
Due to the authority involved, whaling scams can cause significant financial and reputational damage before you discover them.
Quishing (QR code phishing)
Quishing takes advantage of the convenience of QR codes, embedding malicious links in codes placed on posters, emails, or fake websites. When scanned, the QR code directs employees to phishing pages designed to steal credentials or download malware.
As QR codes become more common in workplace communication and payments, they also create a new, often-overlooked attack surface.

Case study: How phishing looks in the real world
Phishing scams regularly test the resilience of even the most security-conscious companies. A recent incident at LastPass illustrates just how sophisticated these attacks have become.
In this case, scammers used AI-generated voice phishing to impersonate the company’s CEO in an attempt to pressure an employee into acting quickly on fraudulent instructions. This approach blended two of the fastest-growing trends: spear phishing and AI-driven deepfakes. By combining credible context with a familiar voice, the attackers sought to bypass both technical defenses and human intuition.
This wasn’t a generic spam email. It was a multi-channel, AI-powered spear phishing campaign that leveraged OSINT, like public events and executive details, to craft a believable pretext.
These types of attacks succeed not by brute force, but by exploiting trust, authority, and timing. Although spear phishing makes up fewer than 0.1% of all global emails, it accounts for more than 65% of breaches. Quality outweighs quantity when it comes to phishing success rates.
The LastPass example underscores two truths about phishing today:
- AI gives attackers an edge. With error-free grammar, cloned voices, and context-aware prompts, phishing attempts are harder to spot than ever.
- Behavior is the real signal. Phishing messages and calls often arrive at unusual times, request urgent action, or come from individuals who don’t typically contact the recipient directly.
Leading security teams need to use simulation-based training that mirrors real-world conditions. Whether it’s a deepfake video call, a spoofed onboarding email, or a text that appears to come from a trusted vendor, employees will learn not only how phishing works, but how it feels.
Adaptive Security integrates these scenarios into training programs, helping organizations build lasting pattern recognition and strengthen their human firewall before a real attack lands.
The takeaway is clear: technical controls alone can’t stop AI-powered spear phishing. What makes the difference is a workforce prepared to question anomalies, verify unusual requests, and recognize when a communication doesn’t align with established norms.
AI, deepfakes, and the future of phishing attacks
Artificial intelligence is reshaping phishing at a speed few defenders anticipated. Attackers no longer rely on clumsy emails riddled with typos. They now have access to chatbots, voice cloning tools, and large language models (LLMs) that generate convincing, context-aware content at scale.
According to CybelAngel’s 2025 External Threat Intelligence Report, 67.4% of all phishing attacks in 2024 incorporated some form of AI. This underscores how quickly these technologies have moved from emerging to mainstream.
Here’s how attackers are weaponizing AI:
- Chatbots and LLMs: Criminals use generative AI to craft messages that mimic corporate tone and bypass red flags that employees can easily spot (e.g., misspellings or awkward phrasing). LLMs can also customize content, creating convincing pretexts for HR, finance, or IT staff.
- Voice cloning: With just a few seconds of recorded audio, attackers can create realistic voice clones. They deploy these in vishing scams or paired with deepfake videos to impersonate executives for highly urgent requests.
- Zero-day phishing lures: Just as hackers can exploit software vulnerabilities before patches exist, phishing campaigns now exploit brand-new events and trends (e.g., regulatory updates and breaking news) before organizations can prepare employees with awareness messaging.
Why AI phishing is harder to detect
AI raises the bar for phishing techniques. Emails and calls now arrive polished, timely, and tailored. They often reference company-specific details scraped from social media, corporate websites, or press releases, making them feel authentic. Even seasoned security professionals admit that some AI-generated lures are almost indistinguishable from legitimate communication.
Protecting against the next generation of phishing
Technology alone can’t outpace AI-driven phishing. A layered defense strategy is essential and should include:
- Security awareness training: Employees need to be exposed to AI-crafted phishing in safe environments. Simulations that mirror voice cloning, deepfake video, and chatbot-driven lures can prepare teams to recognize subtle anomalies.
- Versatile technical controls: Email gateways, endpoint detection, and threat intelligence feeds must update in near real time to identify new attack patterns, since zero-day lures can evade static filters.
- Strong multi-factor authentication (MFA) implementation: Even when phishing succeeds, multi-factor authentication can prevent attackers from turning stolen credentials into a full compromise. However, gaps remain.
Cisco Talos (Cisco’s global threat intelligence team) reported that in Q2 2025, more than 40% of incident response engagements involved MFA-related issues. These included misconfigurations, lack of deployment, or bypass techniques. MFA is only effective when implemented comprehensively and monitored continuously.
As phishing continues to evolve, the line between human and machine-generated deception will blur. The future of resilience lies in preparing employees to spot behavioral anomalies, layering defenses against inevitable failures, and training against the very AI tools that adversaries now wield.
Why Adaptive Security is the best platform for phishing prevention
When it comes to modern phishing threats, legacy awareness tools aren’t enough. Organizations need phishing training and phishing simulation training tools that reflect how attacks unfold, not just static training slides. Adaptive Security was purpose-built for this challenge.
Our training platform prepares employees to defend their organizations against threats across every channel:
- AI deepfake simulations that mimic voice, video, and synthetic personas.
- Voice and SMS-based scenarios that extend beyond email alone.
- Behavioral triggers that adapt simulations based on employee actions and risk levels.
Customers consistently highlight Adaptive’s low-friction deployment and measurable results, from double-digit reductions in phishing click rates to more confident reporting of suspicious activity.
By tracking metrics such as click-through rate, report rate, and time-to-escalation, program owners can measure the impact of phishing simulations and prove the ROI of their awareness programs to leadership and auditors alike.
Phishing prevention isn’t just about stopping one risky action. It’s about creating a flexible defense program that strengthens every employee over time. Book a demo and see how Adaptive can help you close the gap between today’s phishing risks and tomorrow’s resilience.
Make people your strongest defense against phishing
Despite the sophistication of modern phishing tactics, people remain the frontline of defense. When you train employees to recognize behavioral red flags, report suspicious activity, and confirm urgent requests, your organization gains resilience that technology alone can’t deliver.
AI-driven phishing is only growing more convincing. Adaptive helps you stay three steps ahead with simulations and phishing prevention programs that reflect real threats your team is likely to face. Run a free phishing simulation with us today and see how easy it is to make your team your strongest defense.
Frequently asked questions about phishing
What industries are the biggest targets for phishing?
While every sector faces risk, industries handling sensitive financial information, such as banking, healthcare, and government, are top targets.
Hackers know these organizations store valuable data and often rely on high volumes of digital communication, making it easier to disguise phishing attempts. Retail, education, and technology companies are also frequently targeted as part of broader cybercrime campaigns.
How often should I run phishing simulations?
Experts recommend running phishing simulations at least quarterly, though high-risk industries often benefit from monthly campaigns. Frequency matters less than relevance.
Simulations should reflect evolving threats, such as smishing or AI-generated spear phishing. Adaptive Security tailors campaigns to roles and timing, helping security teams measure progress and build resilience across the workforce.
How can I spot a phishing email?
Phishing emails often contain urgent requests, unexpected attachments, or links from trusted domains.
Look for small discrepancies in sender details, such as a misspelled company name or unfamiliar phone number. Also be wary of messages requesting login credentials or payments. Training employees to recognize these subtle cues strengthens overall cybersecurity posture.
How can I prevent phishing?
Phishing prevention requires both technology and people. Email filters, endpoint protection, and strong authentication help, but the most effective defense is employee readiness.
Adaptive Security delivers phishing prevention tools that combine realistic simulations, behavioral feedback, and role-based training, building awareness and measurable risk reduction. Together, these steps reduce the likelihood of phishing turning into a costly breach.




As experts in cybersecurity insights and AI threat analysis, the Adaptive Security Team is sharing its expertise with organizations.
Contents










