AI phishing is a present-day crisis for organizations of all sizes, and the attacks are only getting more personalized, convincing, and dangerous.
The cost of a data breach is nearly $5 million, according to IBM’s latest report. It’s a staggering figure that should remind every IT and security team that they’re up against threats with vast sophistication and the ability to wipe out an entire organization if just one employee makes a mistake.
In this environment, a legacy solution for check-the-box training is a liability.
The threat landscape facing organizations demands a new approach, one rooted in psychology and data. Enter behavior-driven phishing training.
Instead of focusing on rote memorization, this model builds secure habits and reflexes, transforming employees from potential targets into a proactive human firewall. The goal is to measurably reduce the organization’s phish-prone percentage (PPP) and improve overall security posture.
But this isn’t just about better security. Phishing training is about smart investing, too. A common misconception is that robust security awareness training is a costly, complex endeavor with intangible benefits.
The opposite is true. When executed correctly, the return on investment (ROI) of security awareness training is one of the highest in cybersecurity.
Let’s go through a step-by-step roadmap to building a behavior-driven phishing training program that not only protects the organization but also pays for itself.
The Phishing Threat Landscape in 2025
Building an effective defense against all types of phishing attacks starts with understanding the scale of the offense. Threats aren’t static; they’re an accelerating, high-volume onslaught supercharged by artificial intelligence.
Setting the urgency with data is critical to gaining buy-in from executives and fostering engagement among employees.
Latest phishing statistics and trends
Even the most advanced technical filters can’t keep up with the sheer volume of emails associated with phishing.
The scale and its increasing sophistication define the threat landscape of 2025:
- Massive Scale: An estimated 3.4 billion phishing emails are sent daily. The impact is a constant, high-stakes battle for attention in every employee’s inbox.
- Accelerating Frequency: Organizations reported a 15% increase in the volume of phishing attempts, indicating that attackers are scaling their operations more quickly than defenses can keep pace.
- Rising Clicks: The average click rate within corporate environments rose to 33% in early 2025, up from 28% in the previous year. This suggests that, despite basic awareness, the success of malicious emails is on the rise.
But remember that phishing attacks aren’t limited to email alone. Cybercriminals employ various communication channels to target organizations and their employees, including voice, video, and SMS.
There’s also the most significant threat of all: deepfakes.
How AI is supercharging social engineering
Everything about social engineering has become significantly worse since the weaponization of artificial intelligence.
Generative AI — a type of AI that creates new content like text, images, audio, and even real-time video — is an integral part of cybercriminals’ tactics. It enables attackers to automate and personalize social engineering lures on a scale previously unimaginable, with open-source intelligence (OSINT) fueling this capability.
Examples of AI phishing include:
- Hyper-Personalized Emails: AI scans a target’s social media and professional profiles on the internet to craft emails that reference specific projects, colleagues, or recent events, making the lure almost indistinguishable from legitimate communication.
- AI Voice Cloning: Attackers clone a senior leader’s voice from just a few seconds of audio, then use it to make direct calls or leave urgent voicemails in what’s known as a vishing attack.
- Authentic-Sounding SMS: In smishing, generative AI eliminates the spelling and grammar errors that were once telltale signs of a scam, creating flawless and convincing text messages.
- Deepfake Video Calls: Cybercriminals use publicly available media of a trusted contact to develop manipulated media in which the person depicted says or does things to deceive the target(s) into completing a compromising action.
The efficacy of AI phishing is alarming, and the technology is outmaneuvering even the most experienced experts.
Cost of a data breach vs cost of training
The financial argument for phishing training is undeniable:
- Average Cost of a Data Breach: $4.88 million
- Average Cost of Phishing Training: Less than $25 per employee
It’s a stark contrast that highlights a huge opportunity for ROI. The payback period, the time it takes for the cost savings from prevented incidents to equal the training investment, is often measured in months, not years.
The takeaway is simple: Investing a small amount in building a resilient workforce prevents multi-million-dollar catastrophes.
Why Behavior-Driven Training Beats Legacy Awareness
Organizations treated security awareness training as an annual or twice-yearly run-through for decades, and they’re quickly realizing this approach is fundamentally flawed.
The perception of a classic checkbox compliance activity ignores human psychology and habit formation.
From compliance checklists to habit formation
Annual training sessions suffer from knowledge decay, with studies showing employees forget 90% of what they learn within a week. A once-a-year check-in doesn’t build skill. It only fulfills a requirement.
Behavior-driven training is a continuous, data-informed educational model that focuses on forming lasting secure habits. It operates on a simple, powerful psychological loop:
- Trigger: The arrival of a simulated phishing email in an employee’s inbox.
- Behavior: The employee’s action — clicking, ignoring, or reporting the email.
- Reward: Immediate feedback that reinforces the correct behavior or provides a teachable moment for an incorrect one.
Consider this continuous cycle as the engine of habit formation, but remember that its effectiveness depends on the quality of the simulations themselves.
Essential elements of behavior-driven simulations
Successful programs rely on phishing simulations that are realistic, responsive, and tailored.
Key elements include:
- Realistic Context: Simulations must accurately reflect the actual communications (such as emails or text messages) that employees receive daily, referencing internal projects, company events, and common workflows to be believable.
- Immediate Feedback Loops: When a user clicks a phishing link, a just-in-time training message should pop up, explaining the red flags they missed. It’s critical for reducing dwell time, training employees to identify threats faster.
- Adaptive Difficulty: The difficulty of the lures should be based on an employee’s performance. A user who consistently spots easy phishing attempts should receive more sophisticated threats, ensuring continuous learning.
While the elements above are foundational for all simulations, actual effectiveness comes from personalization.
Role-based risk scoring
Not all employees face the same threats. Role-based risk scoring involves tailoring phishing simulations to an individual’s job function and level of access to sensitive data.
A simple risk matrix helps ensure the training is relevant and addresses the most likely threat vectors for each person:
Building a Program That Pays for Itself
A successful, high-ROI program doesn’t happen by accident. It requires a clear, actionable plan.
Here’s a 30-60-90-day framework that provides a structured approach to launching a program that delivers measurable results quickly.
Step 1: Set baselines and objectives
You cannot improve what you do not measure, so the first step is to understand your current security posture.
Below are two key metrics worth measuring:
- Phish-Prone Percentage (PPP): The percentage of users who click a link or open a malicious attachment in a simulated phishing email. In some cases, this metric is referred to as click rate.
- Average Dwell Time: The average time between the delivery of a malicious email and when a user reports it.
IT and security teams should set SMART goals in alignment with the above baselines. For example, a goal might be to reduce company-wide PPP from an initial 33% to under 15% within 90 days.
Step 2: Design adaptive phishing simulations
Using role-based risk profiles, design and customize simulation campaigns.
A modern platform, such as Adaptive Security, enables an organization to leverage AI to create highly realistic lures tailored to different roles and teams.
- Go Mobile: Ensure at least 20% of phishing simulations are mobile-optimized to reflect modern work habits.
- Test & Refine: A/B test different areas of text to determine what is most effective at fooling users, then train them on specific tactics.
With a set of well-designed, role-specific simulations ready, the next step is to implement them thoughtfully.
Step 3: Launch 30-60-90-day rollout
A phased rollout prevents employee fatigue and allows IT and security teams to gather data systematically.
Communicate clearly with stakeholders at each stage:
Measuring Success & ROI
A behavior-driven program is a data-driven program. Success is measured not in course completions but in quantifiable changes in behavior and calculated financial savings.
Key metrics: Phish-prone percentage, dwell time, and reporting rate
Continuously track primary metrics. Remember, the goal is to see the phish-prone percentage and dwell time decrease while the reporting rate increases.
Imagine a line graph where, over 90 days, the red line (PPP) trends downward, the yellow line (dwell time) trends downward, and the green line (reporting rate) trends upward. This is the visual signature of a successful program.
Calculating payback period and hard dollar savings
Any metric improvements can be translated into a compelling financial case. In fact, there’s a four-step process to calculate the payback period for a phishing training program.
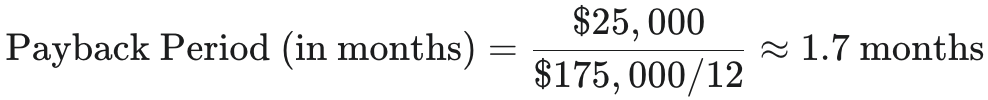
Example for a 1,000-employee organization:
- Estimate Avoided Incidents: If the program reduces PPP from 30% to 10% on a campaign of 1,000 emails, the organization prevented 200 potential clicks. Assume even 1% of those clicks would have resulted in a costly incident, meaning 2 incidents would have been avoided.
- Multiply by Average Incident Cost: Let’s use a conservative average cost of $100,000 for a minor phishing incident rather than a full data breach. 2 incidents x $100,000 = $200,000 in avoided costs.
- Subtract Program Spend: If the annual training program costs $25,000, net savings are $175,000.
- Calculate the Payback Period: Divide the total program cost by the monthly savings to determine the payback period. In this case, the savings are substantial and the payback period is just 1.7 months.
As calculating the payback period proves, the right training program doesn’t just reduce risk; it also delivers a quantifiable financial return in a remarkably short timeframe.
Integrating metrics with SIEM for rapid response
Feed phishing simulation data into a security information and event management (SIEM) platform for enhanced security operations. A SIEM is a system that collects and analyzes security data in real time.
By integrating all systems, organizations create automated workflows. For example, set an alert threshold to automatically create a high-priority ticket if three or more employees in the same department click the same simulated phishing attempt within a few minutes, indicating a potentially successful real-world attack.
Sustaining a Security-First Culture
A 90-day launch is only the beginning. Long-term success depends on creating a culture where security is a shared responsibility.
Gamification and incentive methods
Keep employees engaged by turning security into a positive, rewarding experience.
- Reward Types: Utilize a combination of digital leaderboard badges, micro-bonuses (like a $5 coffee card for the first person to report a simulated phishing attempt), and team-based competitions.
- Avoid Reward Fatigue: Rotate your incentive methods quarterly to keep them fresh and motivating.
Incentives are a powerful tool for engagement, and they’re part of a larger, ongoing cycle of program refinement.
Continuous Improvement Loops
Security is never ‘done.’ Implement a cycle of continuous improvement.
- Quarterly Reviews: Analyze metrics, gather employee feedback on simulations, and refresh training content to reflect the latest phishing trends.
- Incident Retrospectives: After a real phishing incident occurs, hold a brief, blameless 15-minute retrospective to discuss what happened, how the user spotted it (or why they didn’t), and how training can be improved.
By embedding these practices into the security workflow, the organization shifts its entire approach to phishing defense.
Phishing Training: From Cost Center to Strategic Asset
IT and security leaders recognize that the fight against phishing has evolved. An adversary armed with AI requires a defense force of intelligent, engaged employees, rather than just a set of technical tools.
Legacy awareness training is a cost center that offers a false sense of security. A modern, behavior-driven phishing training program is a strategic asset with a measurable, positive ROI.
Focus on habits, use data to measure what matters, and build a sustainable security culture to transform an organization’s greatest vulnerability — its people — into the most powerful line of defense.
The roadmap is clear, the financial case is compelling, and the AI-powered tools are available.
Ready to build your human firewall? See how Adaptive Security’s next-generation platform launches a behavior-driven phishing training program that pays for itself.




As experts in cybersecurity insights and AI threat analysis, the Adaptive Security Team is sharing its expertise with organizations.
Contents










