Imagine receiving a message from the postal service stating that your package needs to be rescheduled. You tap the link, fill in your details, and move on. But the text wasn’t from them. It was from a scammer, and now your information is at risk.
This type of attack is called smishing attack, and it’s one of the fastest-growing forms of social engineering being deployed today. It’s effective because text messages often feel personal and trustworthy—we use them constantly with friends, colleagues, and brands we rely on.
In fact, according to Robokiller, Americans received over 19 billion spam text messages in February 2025 alone. Even if only a small fraction of those messages succeed, the impact could be huge.
This guide will show you how smishing works, how to recognize it, and how to protect your organization and employees against it.
What is smishing?
Smishing, a portmanteau of SMS (for short message service) and phishing, is a type of social engineering attack that utilizes deceptive text messages to deceive recipients into disclosing personal or financial information, downloading malware, or visiting fake websites.
Cybercriminals use smishing or SMS phishing to exploit trust and urgency through text messaging, impersonating legitimate organizations or individuals to manipulate victims into taking immediate action.
Here are the risks typically associated with a smishing attack:
- Data breaches: Exposure of sensitive personal, financial, or corporate data
- Financial loss: Unauthorized transactions, identity theft, and ransomware payments
- Reputation damage: Loss of customer trust and negative publicity
- Compliance violations: Potential fines and penalties for failing to protect sensitive data
- Malware infections: Compromised devices throughout the network, creating further damage
As with all types of deepfake phishing attacks, smishing needs to be taken seriously and included as an integral part of security awareness training.
Why smishing is so effective and dangerous
Smishing succeeds because it leverages the intersection of human behavior, technology, and psychology. Text messages have open rates above 90%, which is significantly higher than email, allowing attackers to almost guarantee visibility.
People tend to trust texts from recognized phone numbers or short codes and act quickly on urgent messages, such as “Your package delivery failed—click here to reschedule.” Attackers also use generative AI to craft convincing, personalized texts that mimic real language and tone, making them even harder to detect.
Combined with the fact that anyone can send hundreds or thousands of messages at minimal cost and low user awareness of mobile-specific threats, smishing remains one of the most effective attack vectors for credential theft and fraud.
Smishing examples: real-world SMS phishing scenarios
Attackers employ a variety of tactics to execute SMS phishing attacks, ranging from impersonating colleagues to falsely claiming that a bank account has been suspended.
In every smishing scenario, the attacker attempts to deceive the target into believing the text message and completing the desired action.
Here are common smishing examples you may encounter.
Urgent request from the employer
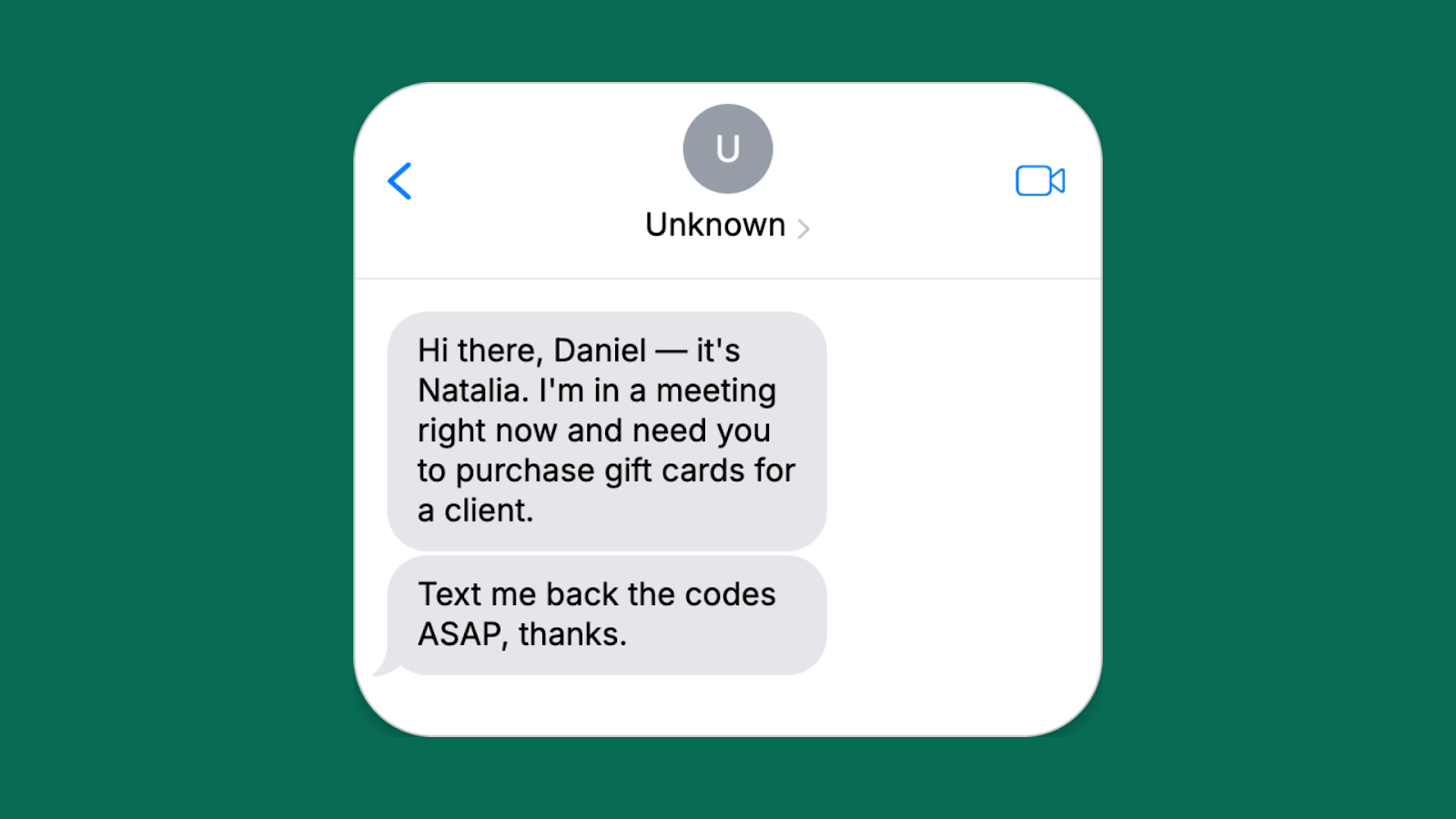
- Attacker’s goal: Trick the employee into spending personal or company money on gift cards and revealing the codes
- Red flags: Unusual request, pressure for immediate action, and bypassing company procedures
Fake package delivery notification
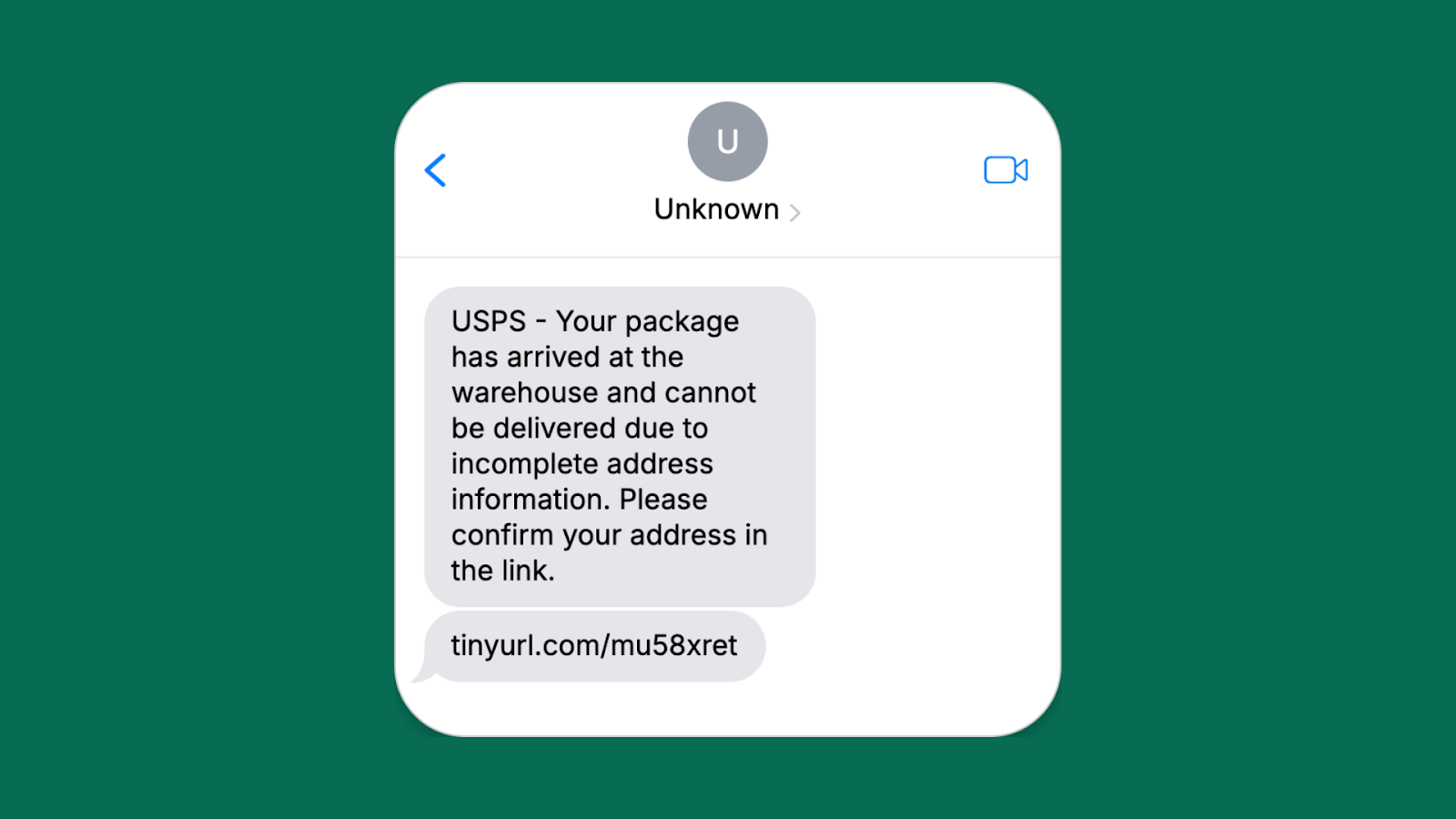
- Attacker’s goal: Steal login credentials or install malware on the device
- Red flags: Unexpected message, generic greeting, suspicious link, and not actively using the delivery service
Bank account alert
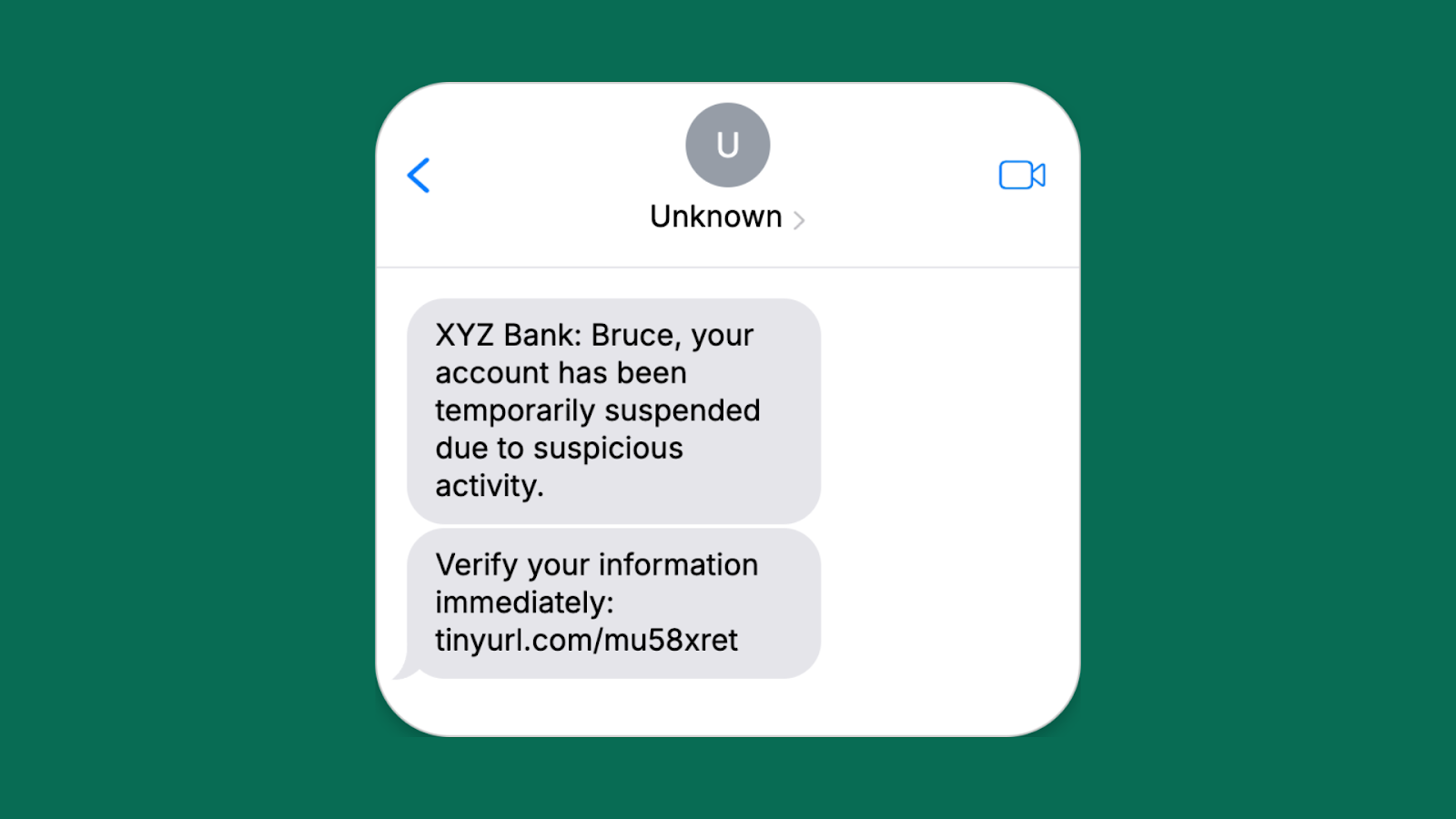
- Attacker’s goal: Steal bank account login details to gain access to personal information and financial assets
- Red flags: Urgent request, threat of account suspension, and a link to a website that does not belong to the bank
Tech support notification
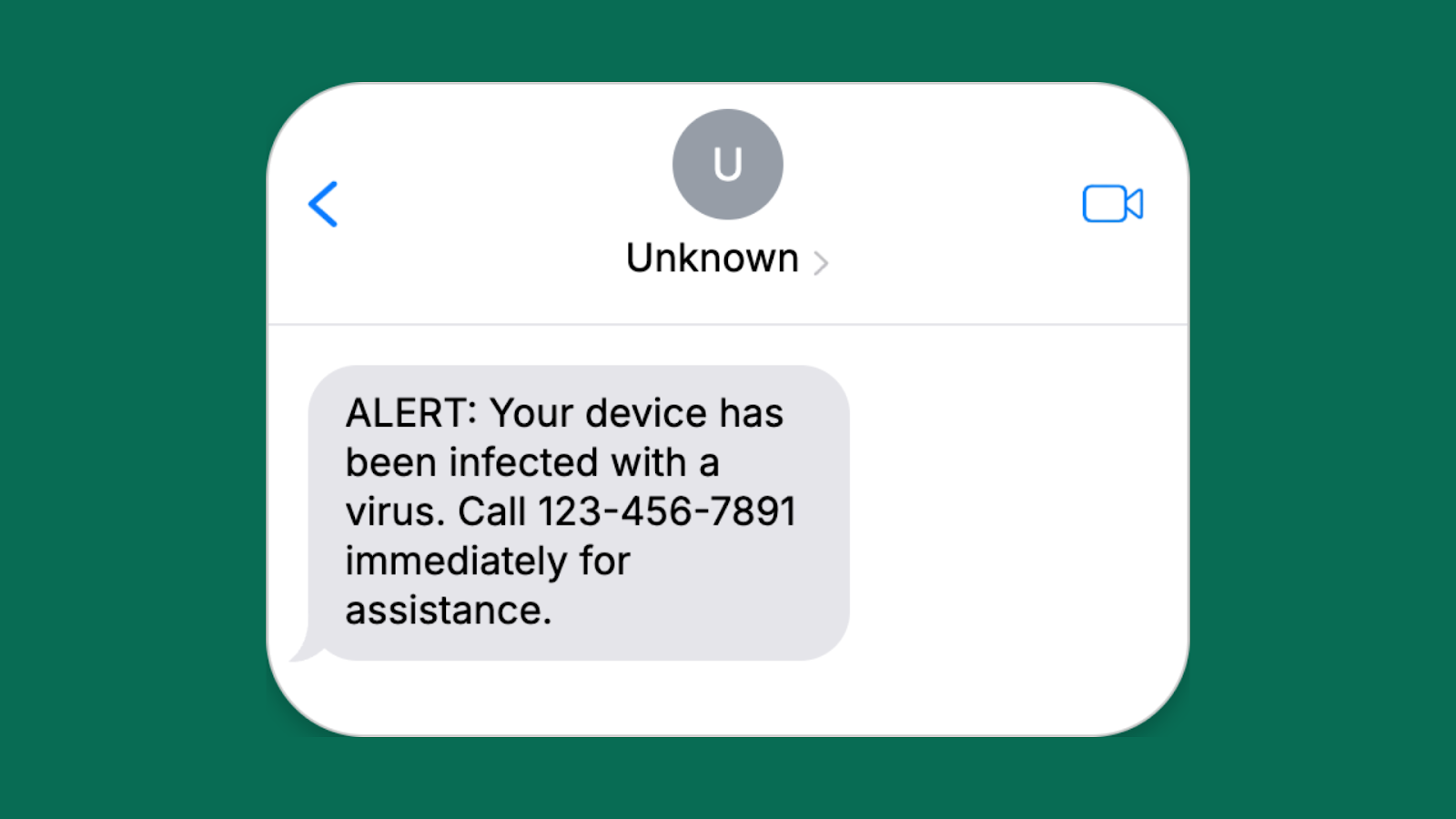
- Attacker’s goal: To gain remote access to the victim’s device, steal personal data, or charge for nonexistent services
- Red flags: Unsolicited message, alarming claim, and pressure to call a specific number
Fake contest winnings
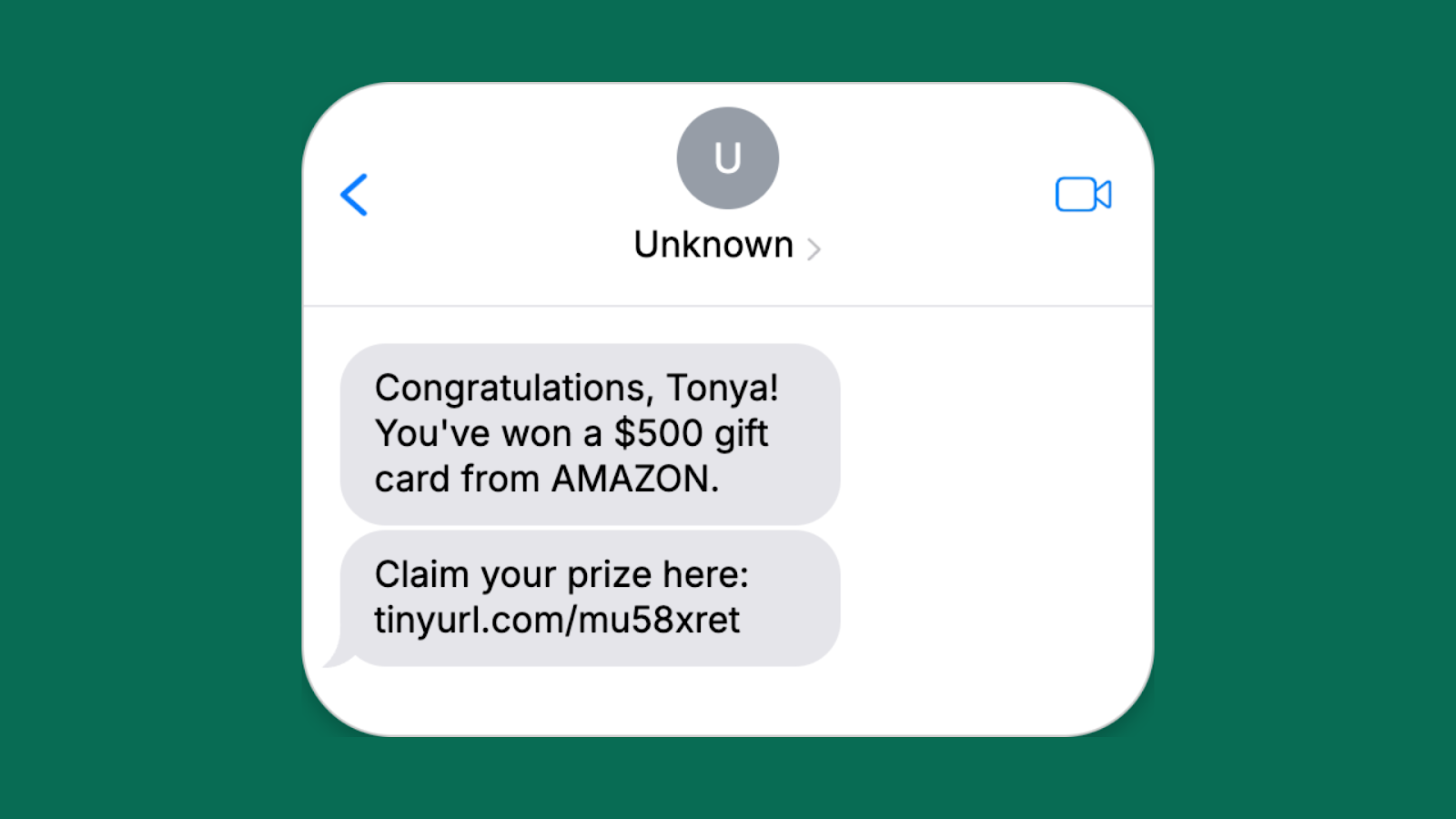
- Attacker’s goal: Collect personal information or install malware
- Red flags: Generic greeting and unsolicited offer that seems too good to be true
Why most security awareness programs fail to cover smishing
Despite the rising risk of SMS-based phishing, many security awareness and training (SAT) programs still leave it as an afterthought. Here’s what tends to go wrong.
Over-focus on email phishing
Training modules frequently center on email-based phishing to monitor suspicious attachments, spoofed sender domains, and malicious links in inboxes. That makes sense, since email has historically been the dominant channel. But it creates a blind spot.
Research shows that 75% of organizations experienced smishing attacks in 2023, and yet fewer training programs emphasize mobile-text threats. In other words, you may be teaching employees to spot phishing emails, but you might not be teaching them to spot scam texts.
Annual or static training cadence
Many organizations schedule SAT once a year or rely on static e-learning modules that barely change. A systematic review found that training formats haven’t always kept pace with evolving threat channels, such as mobile.
When training is low-frequency and static, employees may still recognize an email scam, but they may not recognize a text message that mimics a bank alert or courier notification.
Lack of mobile-first thinking in legacy SAT platforms
Many SAT platforms were designed for desktops and email workflows, rather than mobile usage. Yet, mobile devices have different cues and user behaviors, including truncated URLs, smaller screens, “short code” senders, and a deeper reliance on SMS for everyday communication.
In fact, a 2024 study of mobile phishing found that traditional email-based research does not directly translate to SMS contexts. If you don’t tailor your training to SMS behaviours, you risk the “other end” of the attack surface being exposed.
This is where it becomes crucial to transition to modern-day security awareness training platforms, such as Adaptive Security.
Rather than treating smishing as a “bonus topic” or completely overlooking it, the training program simulates how attacks occur on mobile devices, including shortened links, link preview truncation, fake sender names, an urgent tone, and mobile-specific UI quirks.
How to design an effective smishing simulation program
Designing an effective smishing simulation program doesn’t stop at teaching people what smishing is. It needs to provide them with real-world experience, track their behavior, and close the loop with constructive feedback.
Here are three core phases for a smishing simulation program:
Craft realistic SMS scenarios
Your simulations must be indistinguishable from real-world smishing scams. That means thinking mobile-first, using short, conversational messages, realistic sender names or short codes, and subtle psychological triggers like urgency, authority, and curiosity.
Your simulated smishing attempts should reflect your employees' real-world environment as well. Here are some examples:
- For a financial services team, simulate a fake bank alert (“Suspicious login detected—verify now”).
- For HR or admin roles, use internal-style notifications (“Update to leave policy—view here”).
- For operations or logistics, mimic courier updates (“Your FedEx delivery failed—reschedule now”).
- For executives, test impersonation (e.g., CEO fraud messages, such as confirming payment approval).
When the scenario mirrors an employee’s actual workflow, it triggers a natural reaction instead of a “training mode” mindset. And that’s the point.
This is where Adaptive Security’s approach becomes useful in practice. The SAT platform supports SMS-based phishing simulations, alongside email and voice, with templates that can be adapted to different roles and departments.
Adaptive is also built for mobile delivery, so teams can test realistic text-message attacks (think short messages, shortened links, or urgent tones) and then track how employees respond.

While Adaptive provides the tools, the realism still depends on how you design the scenarios. Ensure that you choose messages that align with your team’s daily context, send them at realistic times, and vary the tone and sender.
Track behavioral signals
To move beyond determining whether employees clicked or not, your smishing simulation program needs to track how people behave and use that insight to enhance the training.
Start by tracking the basics, like who clicked the link, who reported the message, and how quickly they did. These minor data points tell a bigger story about awareness, judgment, and hesitation.
For example, someone who reports a suspicious SMS within a minute shows strong instinct, while someone who clicks right away might need targeted follow-up. These metrics reveal your organization’s behavioral patterns and where training should focus next.
Here’s where Adaptive Security can help. Beyond counting clicks, it captures full behavioral data around each simulation, including reporting rates, time-to-report, and repeat offenders. You can further segment the results by department, role, or even risk profile to see each department’s performance.
Set up post-simulation feedback loops
The real learning happens after the test, when employees understand why they reacted the way they did and how to handle it differently next time. Every smishing simulation should trigger an immediate follow-up.
If someone clicks a link, they should instantly see a short, contextual lesson explaining what signs they missed, such as the sender’s number, an urgent tone, or a shortened URL. If they spotted and reported the message correctly, reinforce that behaviour with positive feedback.
New-gen phishing simulation tools like Adaptive Security deliver instant, behavior-based micro-training the moment someone falls for a smishing simulation. If an employee clicks a simulated smishing link, Adaptive automatically redirects them to a brief, contextual lesson explaining what they missed and how to identify similar future attacks.
These immediate “teachable moments” help people retain what they learn far better than annual refreshers or delayed feedback.
How to recognize a smishing attack: red flags and warning signs
Spotting a smishing attempt isn’t always easy, especially now that attackers use AI tools to craft highly realistic messages. But developing strong awareness and slowing down before you react can prevent serious damage.
Here are the most common red flags to watch for:
- Unexpected messages from unknown numbers: Be wary of texts from numbers you don’t recognize, especially if they contain links or requests. Even if a brand uses a short code or a new number, be suspicious of an unprompted message.
- Requests for personal or financial information: Legitimate banks, government agencies, and companies will never ask for sensitive information (passwords, OTPs, credit card numbers, account numbers) via text.
- Urgency or threats: Smishing messages warning of account suspension, overdue payments, or legal action are classic manipulation tactics. Real organizations provide advance notice and use multiple channels, not just SMS.
- Suspicious or shortened links: Avoid clicking on shortened URLs (like bit.ly or tinyurl.com). These hide the true website and are often used to trick users into visiting malicious sites.
- Offers that seem too good to be true: If a message claims you’ve won a prize or can get a huge discount for free, it’s almost certainly a scam, especially if it asks for personal details to claim it.
- Inconsistencies with known communications: Watch for mismatches in tone and style. If your bank normally uses your full name but suddenly sends a generic greeting or adopts an informal tone, it’s a red flag.
- Requests to bypass normal procedures: Be alert if a message instructs you to skip company policies, such as approving payments or sharing credentials outside official channels.
- Poor grammar or awkward phrasing: While modern AI is making messages sound more polished, grammatical mistakes or strange word choices can still signal a scam.
Preventing smishing: tips for employees and security teams
Protecting against smishing starts with staying alert, both as an individual and as part of a company. Tools and filters can help, but what really stops an attack is when people know what to look for and how to respond.
For employees
Here are tips for employees to protect themselves from smishing:
- Don’t click unknown links: Avoid opening links in unsolicited texts, especially shortened URLs.
- Verify through official channels: If a text claims to be from your bank, courier, or employer, contact them directly using information from their official website or app rather than the number or link in the message.
- Don’t respond to suspicious texts: Don’t reply to a suspicious text message, even to say “stop” or “unsubscribe.”
- Slow down when messages feel urgent: Smishing relies on panic and impulse. Take a moment to think before acting on a message that pressures you to “verify now” in order to “avoid suspension.”
- Keep your device updated: Install software and security updates promptly since they patch vulnerabilities that attackers often exploit.
- Report suspicious messages: In the U.S., forward smishing texts to 7726 (SPAM) or report them to the FTC. Many messaging apps also have built-in reporting features.
For security teams
Employees are the front line, but it’s the security team’s job to equip and support them.
- Build mobile-first awareness training: Ensure your security awareness program covers smishing, not just email phishing. Teach employees what real SMS lures look like, including AI-crafted ones that seem legitimate.
- Run regular smishing simulations: Include SMS phishing in your simulation cycles to build real-world recognition. Adaptive Security supports multi-channel simulations (email, SMS, voice) with post-click micro-lessons, so employees learn immediately from mistakes.
- Set clear internal reporting protocols: Establish one simple process for reporting suspicious texts—ideally, through your existing security or IT helpdesk tool—and make sure employees know it.
- Enforce multi-factor authentication (MFA): Even if credentials are stolen, MFA helps block access attempts from unauthorized devices.
- Use mobile device management (MDM): For company-issued smartphones, apply MDM policies to control app installs, enforce updates, and wipe data remotely if a device is compromised.
- Monitor for targeted attacks: Utilize threat intelligence or mobile security tools to detect large-scale smishing campaigns or spoofed senders targeting your domain or brand.
Organizations are limited in their ability to address smishing from a technological standpoint, so it’s critical to utilize security awareness training and equip employees with the necessary knowledge.
Why Adaptive Security is the best platform to combat smishing
Smishing is evolving rapidly, especially with the rise of generative AI which makes fake texts appear authentic and urgent. The only real defense is consistent, realistic training that helps people recognize and react to these cyberattacks in the moment, rather than falling for the false sense of urgency in those fraudulent SMS messages.
Adaptive Security goes beyond traditional phishing tests by including mobile-first simulations, behavior tracking, and post-click micro-learning that turns every mistake into an instant lesson. Security teams can also segment results by department or risk level, helping them see exactly where awareness gaps exist and how they’re improving over time.
See how Adaptive helps teams spot and stop smishing attacks. Book a demo today.
FAQs about smishing
What is smishing in cybersecurity?
Smishing is a type of phishing attack carried out through text messages (SMS). Attackers send fake messages that appear to be from trusted sources, such as banks, delivery services, or company accounts. The goal is to trick you into clicking malicious links, downloading harmful apps, or revealing personal information such as passwords or payment details. Because texts feel personal and urgent, smishing often has a higher success rate than email scams.
How can you tell if a text is smishing?
Look for red flags, such as messages from unknown numbers, urgent requests, shortened or unexpected links, urgent or threatening language, or tone and wording that don’t match the sender's usual communication style. If something feels suspicious, don’t tap the link. Instead, verify through the company’s official website, app, or customer support number.
What should you do if you clicked a smishing link?
If you accidentally clicked a smishing link, immediately turn off mobile data or Wi-Fi, so the page can’t load further. Don’t enter any personal details. Next, run a security scan on your phone to check for malware, and change any passwords that might have been exposed. If this happened on a work device, let your IT or security team know right away so they can check for broader risks.
Is smishing more dangerous than email phishing?
Smishing can sometimes be more dangerous than email phishing because texts feel more personal and urgent, making people trust them more. Mobile devices also display fewer details, like full URLs or sender addresses, making it harder to spot scams. Since people respond quickly to text messages, attackers often have a better chance of getting someone to click or share sensitive information.
How can organizations train for smishing threats?
The best training is hands-on. Run smishing simulations that mirror real-world messages and follow them with quick feedback or micro-lessons. Platforms like Adaptive Security make this simple by allowing teams to create mobile-first simulations, track who clicks or reports messages, and automatically deliver short lessons immediately after an employee falls for a simulation. This turns every simulation into a learning moment and steadily builds awareness across the company.




As a technology reporter-turned-marketer, Justin's natural curiosity to explore unique industries allows him to uncover how next-generation security awareness training and phishing simulations protect organizations against evolving AI-powered cybersecurity threats.
Contents