Phishing has evolved far beyond suspicious links in email inboxes. Today’s attackers exploit SMS, phone calls, collaboration tools, and even deepfake voice and video impersonations. The stakes are rising: according to IBM’s 2025 Cost of a Data Breach Report, phishing remains the most common initial attack vector, used in 16% of breaches in 2024.
Unfortunately, many organizations still rely on outdated phishing simulations that only test for basic awareness and don’t prepare employees for the real-world tactics hackers use. These include SMS phishing (smishing) targeting financial information, voice phishing (vishing), spoofing a trusted phone number, or deepfakes impersonating a senior executive. In fact, LastPass revealed that attackers used AI-powered voice phishing to impersonate its CEO, proving how advanced these tactics have already become in the real world.
Modern phishing simulations must mirror the sophistication of these threats, reducing click-through rates and building lasting behavioral resilience across your workforce. This guide will break down how to implement simulations that address today’s risks, highlight common myths that stall adoption, and scale programs that truly strengthen their human risk defenses.
What is a phishing simulation?
A phishing simulation is a controlled test that mimics real-world phishing attacks to train employees on how to respond. Unlike a live attack, simulations are safe exercises that security teams craft and deliver to expose users to deceptive emails, texts, calls, or other social engineering tactics without risk to the business.
The purpose of these simulations is to identify behavioral risk signals, such as who clicks suspicious links, downloads attachments, or shares sensitive data. They also create teachable moments that turn mistakes into learning opportunities. Analyzing these responses helps organizations gain visibility into patterns of human risk.
When integrated into broader security awareness training, phishing-specific training reduces employee susceptibility and strengthens your organization’s overall defense posture. Combined with human behavior analytics, they give you the data to tailor training, track progress, and close risk gaps far better than generic one-size-fits-all programs.
Common misconceptions about phishing simulations
Misconceptions about phishing simulations can cause security teams to underinvest, run outdated exercises, or miss the chance to build lasting behavioral resilience. Three of the most common myths include:
- “It’s just about clicking links.” Modern attackers don’t stick to email alone. They exploit smishing, vishing, QR code phishing (quishing), and AI-driven deepfakes.
Even email phishing campaigns are becoming more deceptive, such as recent Gmail phishing attacks using Google Sites to bypass users and security controls. Simulations only testing inbox clicks leave employees unprepared for more advanced tactics.
- “Annual training is enough.” Phishing tactics evolve weekly, not yearly. During their first three months, new hires are 44% more likely to click on malicious links and 71% more likely to fall for social engineering. This shows why infrequent training leaves critical gaps.
- “Our email filter already solves it.” Even the best filters can’t block every attack, especially those designed to exploit human trust. Sophisticated social engineering often bypasses technical defenses, which makes employee phishing awareness tests and adaptive training just as critical as your security stack.
Phishing simulations need to evolve as quickly as the threats themselves. By running regular, multi-channel simulations and pairing them with phishing training for employees, your organization can turn misconceptions into measurable resilience.
Anatomy of a realistic phishing simulation exercise
The most effective phishing simulations don’t just test for a single click—they recreate the layered tactics attackers use in the real world. Adaptive’s phishing simulation platform ensures every exercise reflects modern phishing threats and produces actionable insights.

The key elements of a realistic simulation include:
- Scenario crafting: Simulations should mirror the tone, urgency, and real attack design. From spoofed invoices to fake executive requests, well-crafted scenarios test not just technical savvy but human judgment under pressure.
- Payload diversity: Effective programs move beyond a single “bad link.” Testing with malicious attachments, credential harvesters, or QR codes ensures employees recognize a range of threat patterns.
- Behavioral tracking: Every action—opens, clicks, credential entry attempts—provides a behavioral risk signal. Tracking these patterns gives security leaders visibility into who needs reinforcement and how resilience improves over time.
Real attackers don’t limit themselves to email, making it equally important to cover the full range of phishing attack types in a phishing simulation. By simulating across channels, you can prepare your employees for the tactics most likely to bypass technical defenses.
Employees should start with simpler scenarios before facing complex, AI-enhanced lures, building pattern recognition over time. Adaptive strengthens this process with subtle real-time nudges and personalized retraining, turning risky actions into learning opportunities without eroding morale.
In practice, a realistic phishing simulation is an evolving program that grows with the threat landscape while steadily improving employee behavior.
How to design a simulated phishing campaign
An effective phishing test involves structuring campaigns thoughtfully, aligning them to business goals, tailoring them to your workforce, and evolving them alongside the threat landscape.
Adaptive helps you streamline this process with tools that mirror real-world attacks and deliver measurable outcomes.
1. Define your objectives
Every campaign should begin with clarity: Are you focused on cybersecurity awareness, reducing high-risk behaviors, or validating compliance with your risk management framework?
Establishing goals up front ensures that phishing tests generate data you can act on, whether that means lowering click-through rates, strengthening incident reporting, or benchmarking readiness for audits.
2. Segment your audience
Not every department faces the same risks. Cyber attacks may target finance teams with invoice fraud, while executives often face impersonation attempts.
By segmenting your workforce, you can tailor simulations to their real-world exposure. Adaptive enables targeted testing at the department or role level, giving you sharper visibility into where behavioral risks concentrate.
3. Vary your attack vectors
Attackers don’t limit themselves to one channel. Simulations should cover email, SMS, and voice, as well as modern tactics like QR-code phishing and AI-crafted deepfake lures.
Incorporating spear phishing and highly convincing suspicious emails helps employees learn to recognize attacks that exploit context and urgency rather than obvious red flags. With AI-powered simulation engines, your organization can generate more realistic messages at scale, reflecting the sophistication of today’s threat actors.
4. Schedule intelligently
Running one test per year won’t drive behavior change. Instead, campaigns should be ongoing but varied—delivered at different times of day, across different platforms, and without predictable patterns. This prevents employees from treating phishing tests as a “once-a-year drill” to help them build lasting vigilance.
5. Measure what matters
Click-through rates are useful, but they’re not the whole story. Strong programs also track reporting rates, response times, and follow-through on corrective nudges.
By analyzing these human risk signals, security leaders can demonstrate progress to stakeholders and refine training where it has the greatest impact. Adaptive provides dashboards and behavioral analytics to make these insights clear and actionable.
Top 5 phishing simulation tools for 2025 and beyond
Phishing remains the most expensive initial attack vector, with IBM’s Cost of a Data Breach Report showing an average breach cost of $4.91 million.
Investing in phishing simulators and broader training programs pays for itself by reducing employee-driven risk and helping organizations avoid costly downtime, regulatory fines, and reputational damage.
Here are five leading phishing simulator software options to consider and how they compare to one another.
1. Adaptive Security

Adaptive delivers the next generation of simulated phishing campaigns, using AI-enabled tools to mimic deepfake impersonations, smishing, and vishing. Unlike platforms limited to inbox-based training, Adaptive builds resilience across channels your employees actually use.
When LastPass faced an AI-powered voice phishing campaign, Adaptive’s methodology proved critical in demonstrating how simulated vishing attacks can prepare teams for the same tactics used in the wild. Beyond testing, Adaptive provides behavioral analytics and real-time nudges that convert risky clicks into measurable security improvements.
2. KnowBe4

KnowBe4 is one of the most widely recognized names in the space, offering simulated phishing training and a large library of pre-built templates. However, its model leans heavily on volume rather than innovation, with a focus on traditional email-based testing.
For organizations seeking coverage against more advanced threats like deepfake impersonation or multi-channel lures, KnowBe4 may lack the adaptability required to keep pace.
3. Proofpoint

Proofpoint includes simulated phishing attacks within its larger security awareness suite. Its strength lies in integration with email security products, but this also means simulations are tied closely to inbox activity.
While that’s valuable for basic awareness, it doesn’t provide the full behavioral visibility or cross-channel realism that Adaptive delivers with its multi-vector, AI-driven simulations.
4. Hoxhunt
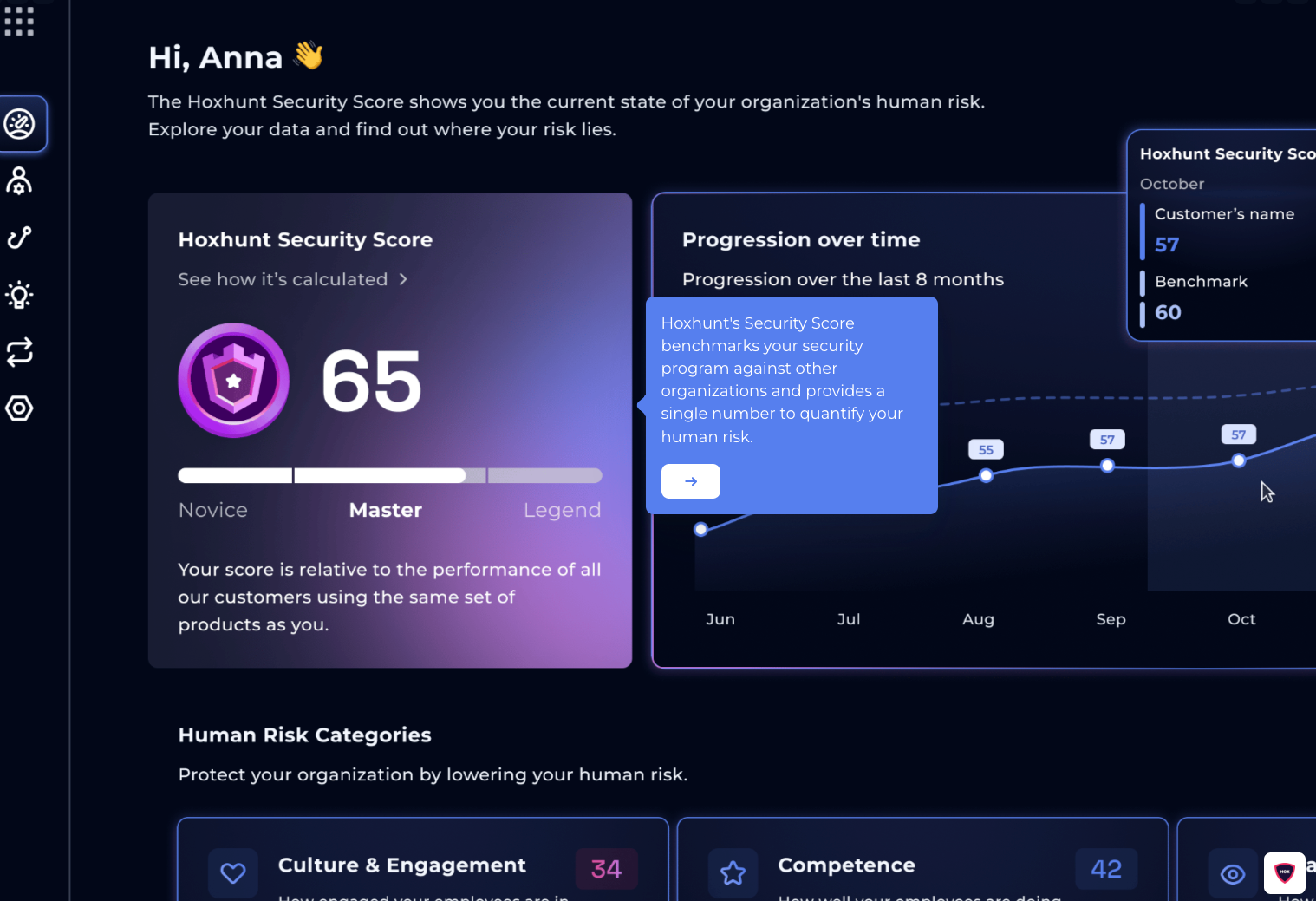
Hoxhunt takes a gamified approach to phishing exercises, sending frequent campaigns to employees and rewarding correct responses. While this can help reinforce awareness, it risks “alert fatigue” and doesn’t always align with enterprise risk management priorities.
Organizations needing strategic insights, such as department-level behavioral risk scoring, may find Hoxhunt less suited than Adaptive’s analytics-driven model.
5. SoSafe

SoSafe offers phishing simulator software aimed at building long-term awareness, with customizable templates and role-based exercises. Its strength is usability, but like others in the category, it emphasizes preset campaigns over adaptive, AI-enhanced threat modeling.
Compared to Adaptive’s evolving simulation engine, SoSafe’s scenarios may feel too static for enterprises facing advanced phishing campaigns.
From phishing simulations to systemic change
As cyber threats evolve across email, SMS, phone calls, and even deepfake impersonations, your organization needs more than a generic playbook. Realistic scenarios are essential for teaching employees to identify and stop real phishing attacks, building resilience before significant damage can occur.
By combining AI-powered attack simulation with behavioral analytics and personalized training modules, Adaptive moves phishing simulations beyond mere compliance into a cycle of learning and risk reduction. The result is not just stronger awareness, but measurable cultural change supported by scalable anti-phishing defenses.
Ready to test your team against real threats? Book a demo today and see how Adaptive’s AI-powered phishing simulation can uncover blind spots and reduce human risk in your organization.
FAQs about phishing simulations
What’s the goal of a phishing simulation?
The goal is to expose employees to realistic scams in a safe, controlled way and measure how they respond. These results provide benchmarks for risk reduction, helping security teams see who reports suspicious messages, who clicks, and where retraining is needed.
How often should I run phishing simulations?
Simulations should be run continuously, not annually. Quarterly is a minimum, but many organizations benefit from monthly or rolling campaigns. Varying timing and attack types helps keep employees vigilant and prevent tests from becoming predictable.
What happens if an employee fails a phishing simulation?
When someone clicks or shares information, it’s a learning opportunity. In a real-world attack, cybercriminals would exploit that moment. In a simulation, employees instead receive targeted retraining and constructive feedback to build stronger habits.
How do phishing simulations improve security posture?
By replicating real-world threats, simulations reduce human error, one of the leading causes of breaches. Over time, they build employee resilience, increase reporting rates, and provide data-driven insights that strengthen the organization’s overall security posture.
Want to see how phishing simulators actually work in practice? Take a self-guided tour of Adaptive’s platform to explore real phishing test examples, interactive training modules, and dashboards that track behavioral risk. It’s a quick way to experience how modern simulations build resilience before launching your own program.




As experts in cybersecurity insights and AI threat analysis, the Adaptive Security Team is sharing its expertise with organizations.
Contents




.avif)