In early 2025, a multinational finance firm, Arup, suffered a $25 million breach after an AI-generated deepfake email, mimicking the CFO’s writing style and tone, tricked an employee into approving a wire transfer. The email was flawless, bypassing spam filters, using contextual business language, and arriving right before quarter-end close.
This wasn’t a spray-and-pray attack; it was behaviorally engineered. Yet, most phishing simulations today still test basic email lures from a decade ago. They don’t mimic attacker timing, sophistication, or channel diversity. They don’t teach teams what today’s threats actually look like.
In this guide, you’ll learn how to run phishing simulations that reflect real-world attacks—multi-channel, behavior-based, measurable—and how to implement them regardless of your tech stack. Whether you’re starting from scratch or optimizing an existing program, this walkthrough will give you a complete framework to simulate modern threats.
Why phishing simulations matter more than ever
According to the Verizon 2024 Data Breach Investigations Report, 68% of data breaches involve the human element, including mistakes, credential theft, and social engineering.
Modern phishing isn’t limited to sloppy emails or generic lures. Attackers have evolved:
- AI-generated phishing emails now mimic tone, context, and sender behavior with alarming accuracy.
- Cyber threats use voice cloning tools in real-time to impersonate executives during vishing calls.
- SMS spoofing and Slack-based attacks bypass traditional filters and reach employees through less-monitored channels.
Static, schedule-driven training can’t keep pace with this sophistication. Phishing simulations close that gap by transforming risk into measurable insight. Each simulated attack reveals how employees react under pressure—who recognizes deception, who reports it, and where vulnerabilities persist. These behavioral data points feed into broader risk management frameworks, giving security leaders the visibility to prioritize interventions that actually reduce exposure.
Effective programs don’t just test awareness. They mirror the complexity of authentic phishing attacks to strengthen the organization’s overall human risk posture and build a culture of active defense.
Planning your simulation program: pre-work to set you up for success
Effective simulated phishing starts long before the first test email is sent. Building a program that actually reduces breach risk requires aligning with real attack patterns, user behavior, and your organization's threat surface. Here’s how to architect a security-first simulation plan that drives results.
Define goals aligned with risk, not vanity metrics
Too often, phishing programs measure success by vanity metrics like click rates or email open rates. These tell you little about actual organizational risk. Instead, define your program objectives around breach reduction, behavior change, and audit readiness. Examples include:
- Reducing credential submission rates
- Increasing reporting accuracy over time
- Identifying high-risk roles or departments for targeted interventions
- Meeting SOC 2, ISO 27001, or GDPR requirements for awareness testing
Set KPIs that reflect these goals. For instance, track risk scores by role, not just raw click volume.
Map personas and roles
Not all employees face the same phishing risks. Finance and procurement teams are frequent targets for invoice fraud. IT admins might receive credential-harvesting emails. Executives are at risk of deepfake impersonation. Segment your user base by:
- Access level (e.g., system admins, HR, payroll)
- Attack likelihood (e.g., executive team, public-facing roles)
- Departmental workflows (e.g., finance teams processing payments)
Simulating targeted attacks against these groups makes training more realistic and reveals hidden risk exposure.
Choose threat types based on real attack trends
Modern phishing simulations must reflect the tactics cybercriminals actually use—not outdated Nigerian prince emails. Phishing scenario types to consider include:
- Credential phishing: Fake Microsoft 365 or Google login pages
- Business email compromise (BEC): Impersonation of a vendor, finance contact, or committing CEO fraud
- Smishing: SMS-based scams with fake links or urgent requests.
- Vishing: Voicemail or phone-based scams, including voice clones
- Deepfake phishing: AI-generated video or audio messages impersonating a trusted leader
- Quishing: QR code-based phishing, often used in physical environments
Use threat intelligence sources like Security Operations Center (SOC) alerts or industry threat reports to prioritize simulation types by likelihood and impact.
Select and segment your audience strategically
Start with a pilot group before scaling organization-wide. Ideal initial segments include:
- Departments with elevated access (e.g., finance, HR, IT)
- Locations or business units recently targeted by attacks
- Teams with historically low training completion or high click rates
Stagger campaigns to avoid overwhelming detection systems and anonymize initial reports to encourage buy-in without shame.
Integrate cybersecurity stakeholders early
Include your SOC team, governance, risk, and compliance (GRC) leads, and compliance officers from the start. They can help ensure:
- Alerts from simulations don’t create noise or false positives
- Simulation timing avoids peak incident response hours
- Results align with broader risk metrics and reporting needs
Cross-functional alignment turns simulations into a force multiplier, not a siloed initiative.
Set up baseline measurements and track change
Before launching your first test, capture a behavioral baseline. This might include:
- Current employee-reported phishing rate
- Known click-through rates from prior tests
- Number of phishing incidents in the past year
After each campaign, track key metrics to assess effectiveness, such as risk reduction over time, changes in response latency, repeat offenders vs. first-time clickers, and correlation with actual phishing incident volume.
Visualize this data to support quarterly business reviews or board reporting.
Step-by-step: how to run effective phishing simulations
Phishing simulations work best when you treat them as a behavioral risk program, not a one-off test. This section walks through a practical framework any security team can follow—regardless of your tech stack—to drive measurable results.
1. Craft or choose simulation templates
Start by selecting phishing templates that reflect current threat tactics, and avoid generic lures. Instead, tailor scenarios based on your industry, department workflows, and common attacker patterns. Use real examples like credential theft, invoice fraud, and executive impersonation.
Effective simulations use context grafting, the process of embedding believable organizational or role-specific details (like project names, tools, or internal phrasing), to make each phishing message feel authentic. A generic “password alert” might raise suspicion, but a spoofed message referencing a recent vendor payment or HR update is far more convincing.
Adaptive’s phishing simulation engine includes AI-generated phishing scenarios that mimic attacker language, formatting, and urgency. It automates context grafting by analyzing communication tone, workflow tools, and user roles to craft scenarios that replicate genuine business context. You can simulate advanced threats—like fake password resets or deepfake-generated messages—without writing a single line of HTML. You can also auto-personalize templates based on recipient role or recent tool usage.
2. Schedule smartly
Attackers don’t operate on a 9-to-5 schedule. Launch simulations during realistic windows such as:
- End-of-quarter finance cycles
- After-hours or early mornings
- Right before public holidays or events
- Following a known vendor or internal update
To maintain engagement and avoid fatigue, use a layered cadence: run light monthly phishing tests to reinforce awareness and pattern recognition, and follow up with comprehensive quarterly simulations that introduce new attack vectors and measure deeper behavioral change.
Consider incorporating deepfake voicemail or video messages to simulate urgency from an executive. This heightens realism and tests how employees respond under pressure. By mixing timing and complexity throughout the year, organizations build vigilance that mirrors the unpredictability of real attackers—without making testing feel repetitive or punitive.
3. Deliver through realistic channels
Limitations to email-only tests will skew your results. Everyday phishing often uses multi-channel social engineering to gain trust. Run simulations through:
- Email: Still a primary vector, especially for link- and attachment-based lures
- Smishing (SMS phishing): Useful for urgent messages or MFA-related scams
- Slack or Teams: Growing surface for impersonation and quick-response abuse
- Vishing (voicemail phishing): Especially effective when attackers use spoofed numbers or AI voice cloning
Use multiple channels across campaigns to evaluate full-spectrum risk exposure.
4. Monitor results
Collect meaningful behavioral signals, not just clicks. Focus on:
- Who clicked on malicious links
- Who submitted credentials or sensitive data
- Who reported the message using built-in tools or escalation channels
- Who ignored the email altogether
- How quickly employees reported suspicious messages—your average “time to report” (TTR)
TTR is one of the strongest indicators of organizational readiness. A fast response window means employees are both alert and confident in escalation procedures; longer delays highlight where communication or training may need reinforcement.
Adaptive’s dashboard tracks these behaviors with precision, offering granular metrics and heatmaps by role, team, and region. Built-in TTR analytics help security leaders visualize how awareness translates into action, identify high-performing departments, and trigger targeted follow-ups that close response gaps over time.
5. Automate follow-up
Don’t waste teachable moments. Automatically deliver short, contextual training based on user actions. If someone clicks a link, send them a 90-second module on verifying sender authenticity. If they report it correctly, reinforce the behavior with praise or recognition.
Adaptive includes behavior-based micro-training and nudges that deploy immediately after test completion. This reinforces learning in the moment, which improves long-term retention and risk reduction.
6. Loop in metrics that matter
Look beyond surface-level KPIs. Effective phishing programs measure:
- Click-through trends over time, not per campaign
- Reporting rate increases among repeat users
- High-risk roles or departments with frequent failures
- Improvement cycles after tailored interventions
Simulated phishing attacks provide behavioral insights that go far beyond static training modules. Organizations that run consistent, role-based tests see higher security posture scores, lower breach likelihood, and improved audit readiness.
Track program ROI by comparing simulation results with incident response logs, risk audit performance, or compliance milestones.
Measuring simulation success: What to track
Phishing simulation training only creates value when it’s tied to measurable business outcomes. Security leaders and boards need to see evidence of risk reduction, not just activity reports. Adaptive’s analytics framework aligns behavioral metrics with organizational resilience, helping teams quantify progress quarter over quarter.
Key performance indicators include:
- Report Rate (RR): Percentage of users who report simulated phishing within 24 hours
- Target: +10 points QoQ.
- A higher rate indicates faster threat recognition and stronger reporting culture.
- Time-to-Report (TTR): Median minutes from message delivery to first report
- Target: −25% QoQ.
- Faster TTR means employees are identifying threats in real time, limiting exposure windows.
- High-Risk Clicks (HRC): Clicks or data submissions from privileged or high-access roles
- Target: −40% within two campaigns.
- A decline demonstrates progress in protecting critical accounts.
- Repeat Offender Rate (ROR): Users who fail simulations more than twice in two quarters
- Target: −50% YoY.
- Tracking this highlights the effectiveness of targeted coaching.
- Verification Uptake (VU): Percentage of users who validate requests through approved callback or dual-approval channels
- Target: +20 points QoQ.
- This reflects adoption of anti-phishing behaviors that extend beyond simulations.
By connecting these indicators to broader risk-management metrics, such as reduced incident volume, improved audit scores, and stronger cyber resilience, security teams can demonstrate tangible ROI from phishing simulation programs.
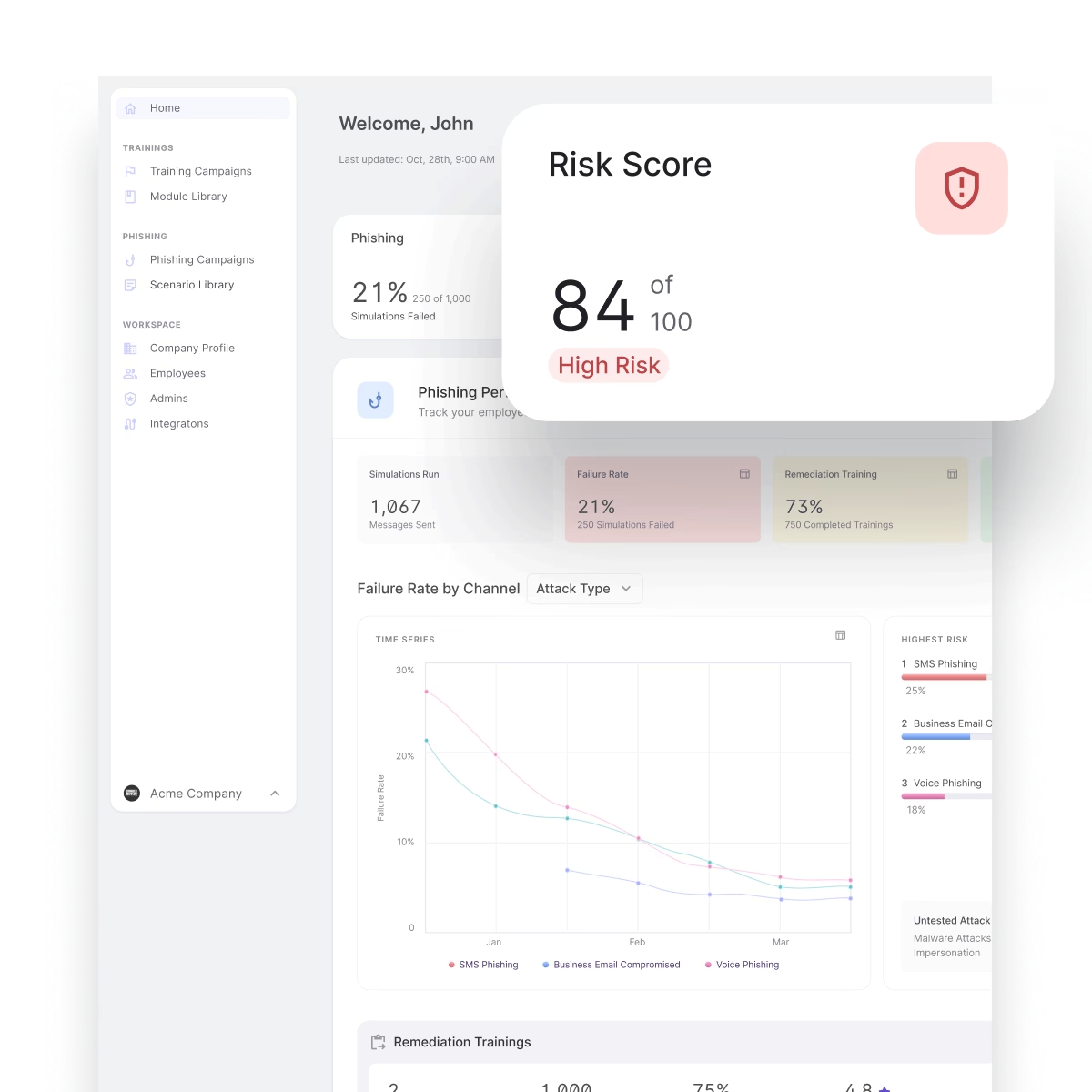
Adaptive’s reporting suite makes these metrics actionable, visualizing behavioral trends over time and surfacing where intervention drives the greatest impact. The result: data you can take to the boardroom to prove measurable progress against human-driven threats.
Reduce human risk with phishing simulations that drive measurable results
Teams using Adaptive’s phishing simulations see faster reporting times, fewer privileged-role clicks, and measurable drops in repeat errors—all critical indicators of improved security posture.
Running phishing simulations that actually reduce breach risk requires more than just sending test emails. You need actual scenarios, behavior-driven insights, and a platform that keeps pace with how attackers operate.
Adaptive’s phishing simulation software helps security teams:
- Launch AI-crafted lures, including deepfake scam videos and voice messages.
- Deliver multi-channel tests across email, SMS, Slack, and voicemail.
- Target users based on role, risk exposure, and behavior history.
- Automate follow-up with contextual micro-training.
- Track performance trends and behavior change, not just clicks.
Whether you're testing your CFO’s response to a CEO impersonation scam or assessing your help desk’s handling of vendor fraud, Adaptive’s simulation tool gives you the clarity and control you need.
Make your next phishing simulation count. Book a custom demo today and see how Adaptive can help you prepare for modern threats.
FAQs about running phishing simulations
How often should my organization run phishing simulations?
Run phishing simulations at least once per quarter to stay ahead of evolving cyber-attacks. Many teams benefit from monthly or bi-monthly campaigns, especially when onboarding new hires.
Frequent testing helps benchmark your organization's resilience against phishing attempts and supports continuous behavior improvement. Use the results to refine training and identify high-risk roles.
What should I do if an employee fails a phishing simulation?
Treat it as a teachable moment. Deliver immediate, targeted feedback explaining why the simulation email was suspicious. Follow up with security awareness training that reinforces recognition of similar threats.
Avoid public shaming. Instead, track repeat behavior and support improvement with personalized guidance.
What are some common mistakes to avoid when running phishing simulations?
Teams often make phishing simulations too predictable or unrealistic. Avoid testing only through email or using outdated templates. Don’t skip follow-up training, and never rely solely on click-through rates. You should also align simulations with real attack trends and integrate results with your broader cybersecurity metrics.
How can I simulate deepfake phishing?
Use Adaptive Security’s platform to run AI executive impersonation attacks that mimic real-world malicious emails, video voicemails, or deepfaked audio from trusted leaders.
These advanced phishing campaigns test your team’s ability to detect high-stakes deception and build readiness against emerging AI-powered threats. Adaptive makes these simulations seamless, realistic, and scalable.




As experts in cybersecurity insights and AI threat analysis, the Adaptive Security Team is sharing its expertise with organizations.
Contents




%20(1).avif)