Phishing has never been more effective—or more sophisticated. According to Verizon’s 2025 Data Breach Investigations Report, 68% of breaches involve the human element, showing how attackers continue to exploit people rather than systems. They move faster, automate campaigns, and use convincing messages that blend seamlessly into normal communication.
These emails slip past filters because they look and sound legitimate. Some reach thousands of inboxes, while others focus on a single person in targeted attacks, using details from social media, press releases, or internal directories to sound credible. Both succeed by exploiting human trust.
In this article, you’ll learn how phishing and spear phishing actually work, how AI is reshaping their tactics, and how training can help close the gap. You’ll also see how phishing simulation platforms like Adaptive give teams practical experience with modern threats so they can spot and stop deception before it spreads.
Phishing 101: What it is and why it still works
Phishing is a mass email scam that aims to trick large groups of people into clicking a link, downloading a file, or handing over login credentials and other sensitive information. Instead of targeting one person, attackers send out waves of messages, hoping someone will take the bait.
The messages often mimic familiar scenarios, such as:
- Fake invoices requesting immediate payment or credit card numbers
- Password reset prompts that look like they came from your email provider and redirect to a fake website
- Bank or delivery updates urging you to “confirm” details through a link
- Lookalike domains or compromised infrastructure that host phishing sites on real servers or mimic trusted brands, making malicious links appear safe
Picture an email from a courier saying your package couldn’t be delivered. It includes a link to “reschedule delivery.” The page looks authentic—with logos and tracking details—but it’s a fake site designed to steal your login information.
That mix of familiarity and urgency is what makes phishing effective. Verizon’s 2024 Data Breach Investigations Report found phishing was a factor in 31% of global breaches, often acting as the first step in larger attacks. Automated tools make it easy for cybercriminals to send millions of messages in minutes, knowing only a few need to succeed.
For employees, this scale makes vigilance harder. Many training programs still focus on obvious clues like bad spelling or strange email addresses. Modern phishing, however, looks professional. Without training that builds context awareness and decision-making skills, even cautious employees can miss the signs of a scam.
Spear phishing: the personalized threat you’ll never see coming
Spear phishing focuses on a specific individual or group, using social engineering tactics and personalization to increase credibility. Unlike broad phishing campaigns, spear phishing relies on preparation. Attackers study their target, craft messages that match the person’s role, and deliver them through the channels the target already trusts.
Common spear phishing attack tactics include:
- LinkedIn scraping to gather job titles, reporting lines, and professional details
- Open-source intelligence (OSINT) from social media or press releases to learn about recent projects or company news
- Personalized language that reflects the target’s work style, colleagues, or current priorities
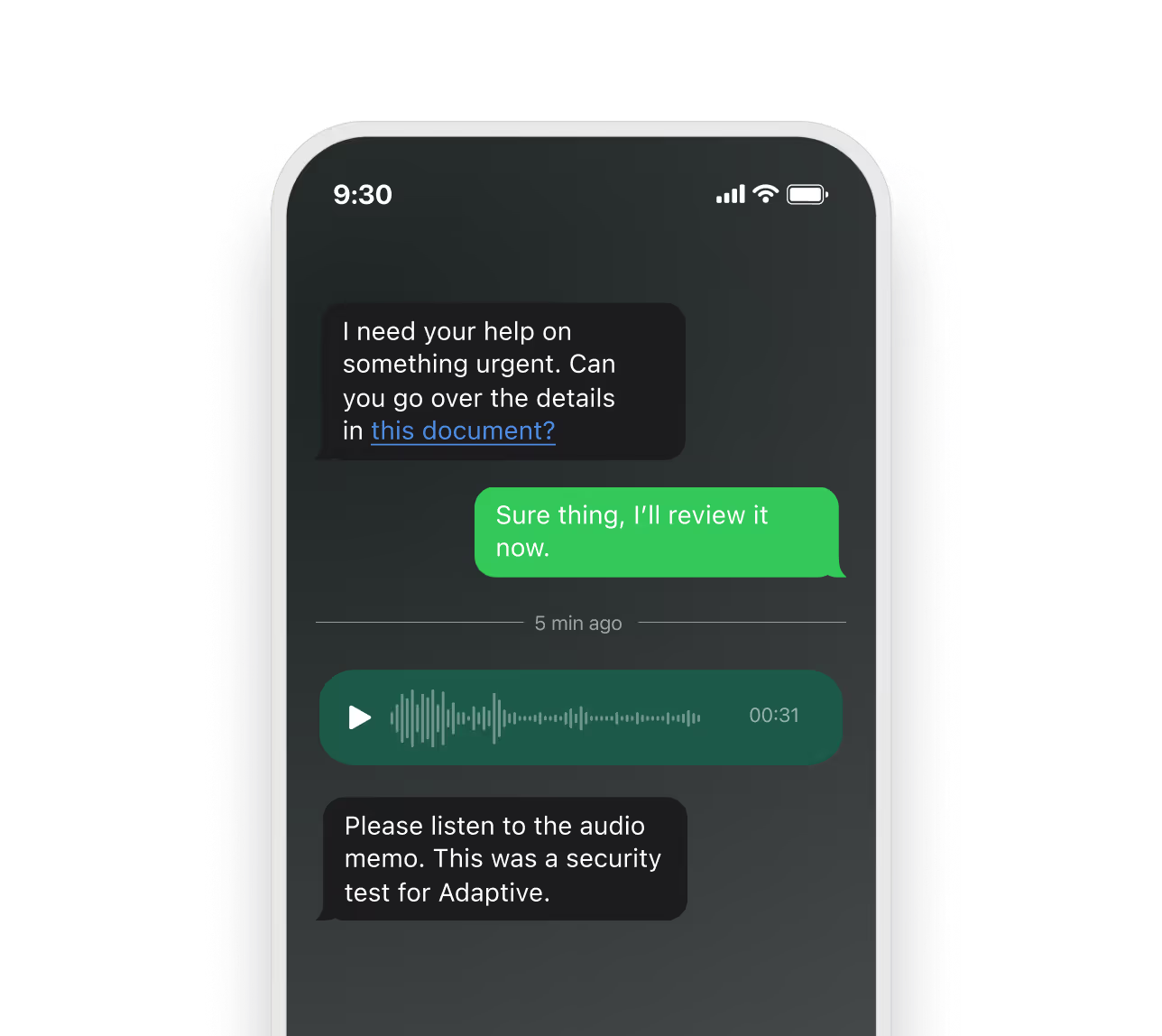
These methods help hackers build trust, but the threat is expanding further with AI. Generative AI now creates flawless messages, clones executive voices, and even produces deepfake videos.
The World Economic Forum reported a case where a finance executive approved a $25 million transfer after hearing what he thought was his CEO’s voice during a conference call. The call turned out to be AI-generated—a striking example of CEO fraud, where cybercriminals impersonate senior leaders to authorize payments or extract sensitive data.
The rise of these advanced techniques is why traditional awareness training falls short. Teaching employees to spot poor grammar or suspicious links no longer works when every message looks authentic. They need hands-on experience that builds instinct, not just knowledge.
Platforms like Adaptive create dynamic simulations that reflect how real spear phishing campaigns unfold. Each exercise adapts to the learner’s choices, revealing how small moments of hesitation or misplaced trust can open the door to compromise. This turns awareness into action and helps teams respond with confidence when genuine threats targeting confidential information appear.
AI and the future of phishing: from generic spam to deepfake persuasion
Artificial intelligence is transforming phishing from clumsy spam into sophisticated persuasion. Attackers no longer rely on poor grammar or recycled templates. Instead, they use generative tools to create personalized lures at scale:
- Voice cloning replicates an executive’s voice with near-perfect accuracy. Criminals use cloned voices to request wire transfers and approve fraudulent deals.
- Voice spoofing manipulates caller identity or plays recorded audio to impersonate trusted contacts and trick employees during live calls.
- Automated phish generators craft convincing emails in seconds, tailored to industry jargon or company-specific language.
- Fake video calls led by deepfake avatars impersonating leaders, make fraudulent requests appear genuine.
These capabilities change the equation for cybersecurity defenders. Attacks that once took hours to plan can now be launched in minutes. A single tool can produce thousands of unique, highly polished messages, each customized for a different employee. The scale makes it harder to rely on old training models, antivirus software, or technical filters alone.
The implications are clear: speed, believability, and reach are all increasing. Employees face scams that sound like their manager, look like their client, or even appear as a live video call. Without preparation, many will trust what they see and hear.
This is where training must adapt. Adaptive’s simulation engine mirrors these AI-driven scenarios so your workforce learns to detect subtle cues before they cause harm. By practicing with realistic lures—whether in email, voice, or video—teams build the instincts needed to keep pace with attackers who move faster every day.
How to tell the difference between phishing and spear phishing
Phishing and spear phishing share the same goal—deception that leads to stolen data or funds—but the methods differ. A quick way to see the contrast is through side-by-side features:
Language patterns and personalization depth
Phishing messages often use vague greetings such as “Dear customer” and language designed to fit a wide audience. Spear phishing emails and messages read differently. Attackers reference actual projects, colleagues, or recent events to sound authentic.
For example, an attacker may mention a quarterly report or a vendor by name, creating a sense of familiarity that lowers defenses.
Channel context (SMS, email, voice)
Most phishing attempts arrive as email, but spear phishing expands across multiple channels. A fraudster might send a follow-up text message after a spoofed email to increase credibility, or use a phone call to impersonate a supplier. In some cases, attackers combine channels—such as emailing a fake contract and then calling to urge immediate approval.
Urgency cues and authority mimicry
Phishing usually relies on simple threats like account suspension or missed delivery. Spear phishing raises the stakes by imitating authority figures.
For example, an employee may receive a voicemail that sounds like the CFO, asking for urgent action on a transfer. This combination of authority and urgency makes the request harder to ignore. This pushes people to act quickly without verification, allowing attackers to gain access or approval.
The difference matters because employees who might dismiss a generic phishing scam like a “reset your password” email could still fall for a carefully crafted message that feels relevant to their daily work. Recognizing these patterns is the first step to reducing risk.
Why it’s time to rethink your approach to phishing training
Most awareness programs still treat phishing as a problem of spotting suspicious links. Employees are shown examples of poorly written emails and asked to click “report” when they notice obvious mistakes. Since modern phishing and spear phishing are evolving cyber threats that bypass these cues, that narrow focus leaves major blind spots.
Traditional training fails when attackers use tactics that look legitimate. Many modern scams involve phone calls, chat messages, or video requests that never include malicious attachments or links. Employees unprepared for those situations, even with traditional security tools in place, often share information or approve actions that seem routine.
Attackers are also expanding across new channels:
- Deepfake audio convincing enough to trick finance teams into wiring millions of dollars
- AI-generated video calls impersonating executives to pressure employees into urgent approvals
- SMS and chat lures disguised as vendor updates or payroll notifications
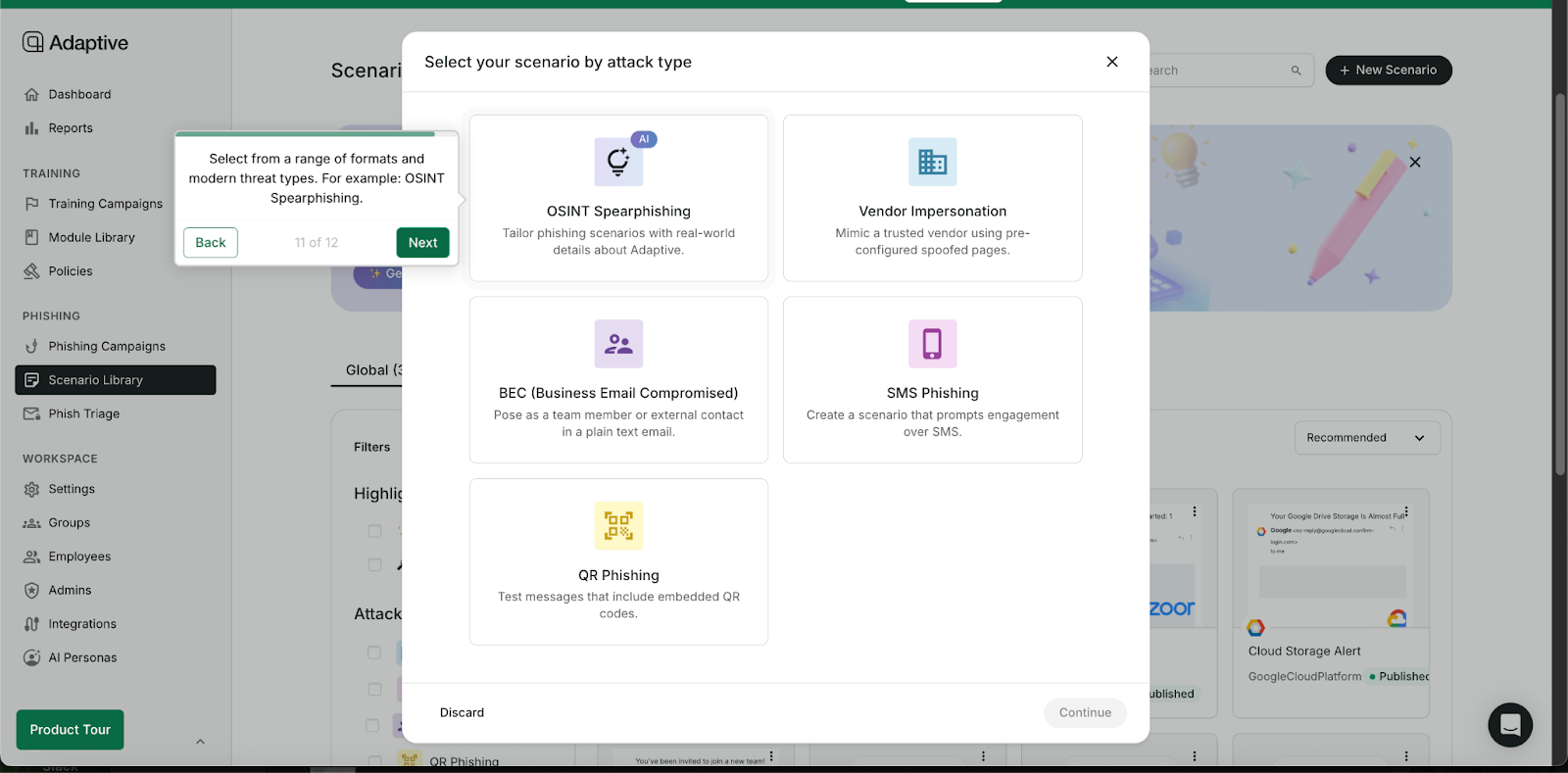
These methods succeed because they feel authentic, not because they contain obvious errors. This is where next-gen anti phishing simulation and SAT platforms like Adaptive change outcomes.
Adaptive prepares employees for modern threats with:
- Multi-channel simulations that extend beyond email to cover SMS (smishing), phone (vishing), and video-based threats
- AI-enhanced scenarios that mirror deepfake voices, cloned emails, and hyper-personalized lures
- OSINT-powered campaigns that use publicly available details—such as LinkedIn job titles, company announcements, or press mentions—to craft realistic spear phishing attempts
- Behavioral risk scoring that enhances threat detection by tracking not only clicks, but also hesitation, verification steps, and reporting habits
- Role-based training paths tailored for executives, finance teams, and frontline staff who face different risks
- Analytics dashboards that highlight concentrated areas of risk and provide real-time, measurable progress over time
By practicing with realistic simulations, employees build the habits that hold up under real pressure: verifying authority, questioning context across channels, and escalating when something feels off. That shift from surface-level awareness to behavior-driven readiness is what keeps organizations ahead of attackers.
➜ For practical ways to train employees against deepfake-based manipulation, see our guide on deepfake security awareness training.
Final thoughts: human risk is the real target
Phishing and spear phishing share the same goal, but they differ in scale and precision. Phishing casts a wide net with generic lures, while spear phishing zeroes in on individuals with carefully researched details. The latter is spreading fast as attackers turn to AI, deepfakes, and OSINT to make their messages and calls more convincing.
Teaching employees to hover over links or spot poor grammar no longer covers the reality of modern attacks. The real risk lies in how people respond when a request for social security numbers, personal or bank account access, or financial transfers looks authentic, sounds urgent, and seems to come from someone they trust.
Adaptive provides organizations with simulations that reflect advanced phishing tactics, from AI-generated voices to OSINT-powered personalization. Employees practice with realistic scenarios across email, SMS, voice, and video, building habits that protect them in real incidents. Security teams gain insight into where risk is concentrated and how behaviors improve over time.
Want to see what realistic spear phishing looks like? Book a demo today.
FAQs about spear phishing vs. phishing
What’s the main difference between spear phishing and phishing?
Phishing targets large groups with generic messages that push quick action, such as clicking a link or resetting a password. Spear phishing focuses on one person or a small group. Attackers use research to personalize the message, reference real projects, or mimic trusted contacts. This added precision makes spear phishing harder to detect and far more dangerous for organizations.
What role does AI play in spear phishing?
AI makes spear phishing faster and more convincing. AI tools generate professional emails that bypass red flags people used to look out for. Attackers also use AI for voice cloning or deepfake video calls to create messages that look and sound authentic.
In short, AI allows criminals to scale highly targeted campaigns while reducing the chance that an employee will notice something unusual.
What’s the best way to protect against personalized phishing?
Protection requires more than teaching staff to spot obvious signs of fraud or implementing multi-factor authentication alone. The most effective defense is realistic training that mirrors the tactics attackers use today.
Simulations across email, text, phone, and video help employees practice verifying requests, pausing under pressure, and reporting suspicious activity. Continuous training and behavioral risk tracking ensure defenses improve as attacker methods evolve.




As experts in cybersecurity insights and AI threat analysis, the Adaptive Security Team is sharing its expertise with organizations.
Contents










