An employee receives an email from someone who appears to be a vendor contact: “Just checking in, hope your week is going well.” She responds, thinking it’s a routine follow-up. The next day, a second message arrives: “Forgot to attach the updated invoice, here’s the link.” She clicks, and within seconds, the attacker gains access to the company’s financial systems.
This is barrel phishing—a calculated, two-step attack where criminals build trust before delivering the blow. Unlike standard phishing, which relies on urgency or fear, barrel phishing exploits familiarity. The first message feels normal. The second weaponizes that trust to bypass even cautious employees.
Barrel phishing exposes a critical blind spot in organizational defense: human connection. Understanding how these attacks unfold, what psychological triggers they exploit, and how to recognize them early can help teams respond faster and reduce risk across every inbox.
What is barrel phishing?
Barrel phishing—also known as double-barrel phishing or two-stage phishing—is a social engineering tactic that unfolds in two steps. The first message is harmless, designed to build familiarity or rapport. The second delivers the malicious payload, often through a fake link, infected attachment, or credential request.
Unlike standard phishing, which relies on mass emails and emotional triggers, like fear or a sense of urgency, barrel phishing attacks feel conversational. Attackers mimic the tone, timing, and context of real business exchanges, making their outreach harder to flag as suspicious. This shift represents the evolution of phishing from one-off scams to multi-stage, relationship-driven deception.
The rise of generative AI in phishing has made these attacks even more convincing. AI-powered tools can craft fluent, personalized messages that mirror a company’s communication style or even a specific leader’s tone, fueling a surge in AI executive impersonation attacks. As a result, traditional red flags, such as spelling errors, awkward phrasing, or generic greetings, no longer stand out.
Barrel phishing thrives in this new environment of automated authenticity, where trust is easier to fake and harder to verify.
The psychology that makes barrel phishing so effective
Barrel phishing succeeds compared to other types of phishing attacks because it mirrors how people naturally build trust and respond to workplace dynamics. Each stage of the attack taps into different psychological levers that influence behavior.
Trust-building: The first email feels routine, like something a coworker or vendor might send. It lowers defenses by creating familiarity before they make any request.
Urgency layering: The second message introduces mild pressure, such as a payment deadline or a missing file. That shift in tone triggers compliance and reduces critical thinking.
Authority and social engineering: Many campaigns impersonate internal departments like IT, HR, or legal. Employees instinctively defer to authority, especially when the message aligns with their job responsibilities.
Some roles face higher risk than others. Finance, HR, and legal teams are frequent targets because they handle sensitive information, wire transfers, and employee records. Yet, anyone with an inbox can fall for a message that feels both personal and legitimate.
Replicating these psychological cues is central to how Adaptive builds its phishing simulation scenario engine. The platform trains employees to recognize subtle manipulations before they escalate into costly breaches.
Real-world examples of barrel phishing in action
In 2025, threat actors tied to the ShinyHunters collective (also tracked under cluster UNC6040) launched a large-scale campaign targeting organizations’ Salesforce environments. Rather than exploiting a technical flaw in Salesforce itself, they leaned on social engineering to gain access. Their methods mirrored key traits of barrel phishing.
Phase 1: The disarming outreach
The attackers began with benign touchpoints, either via voice calls impersonating internal IT staff or vendor contacts, or emails that seemed routine, such as “Could you verify your Salesforce connector settings?” Their goal was simple: appear helpful, not threatening.
Because these messages fit expected roles and tone—IT, support, integrations—they didn’t arouse suspicion. Some targets may have even considered them administrative follow-ups and ignored them.
Phase 2: Escalation and access
After the initial outreach softened the environment, attackers delivered the real request: install or authorize a version of Salesforce’s Data Loader or a connected app, granting OAuth permissions. Behind the scenes, the malicious tool gave them API access to pull data from CRM tables.
In many cases, vishing (voice phishing) played a role. The attacker would call, pretending to be IT support, saying the user needed to complete an authorization step to restore service or fix an integration. That added pressure and rationale for the user to comply.
Outcome and fallout
Once the malicious app or connection was in place, the attackers extracted mass volumes of data from Salesforce customer records, including contacts, accounts, cases, user fields, and more. They later threatened extortion or public release.
Major names emerged among the victims. Google confirmed that the hackers compromised one of its Salesforce environments.
KrebsOnSecurity documented how ShinyHunters operated via voice-based social engineering to steal and extort data from dozens of organizations.
This breach illustrates a true barrel-style framework: warm the target with a false sense of legitimacy, deliver the “helpful” tool, then strike via trusted access rather than brute force.
How to spot a barrel phishing attack before it escalates
Barrel phishing hides in plain sight. The first message looks harmless, sometimes even helpful, so the warning signs only emerge when you know what to look for.
- Watch for subtle shifts in tone. The first email may sound conversational, while the follow-up adds urgency or formality. That change in tone is a hallmark of social engineering, signaling the attacker’s pivot from rapport-building to exploitation.
- Check sender details every time. Cybercriminals often spoof or slightly alter domains (for example, “finance-dept.co” instead of “finance-dept.com”). Small deviations in sender address or reply-to fields reveal when a message isn’t coming from who it claims to be.
- Notice timing and context. In a typical barrel phishing sequence, the follow-up arrives within hours or a day of the first message. If a sender suddenly follows up with an attachment, a link, or a request outside your normal workflow, treat it as a red flag.
- Question out-of-band requests. You should verify any message that asks for password resets, data exports, or approvals outside of standard channels in person or through official platforms, not via reply.
Continuous phishing awareness training helps teams recognize these escalation cues before they lead to compromise. Adaptive’s phishing simulations teach users to detect these patterns over time, combining repetition and behavioral feedback to strengthen intuition.
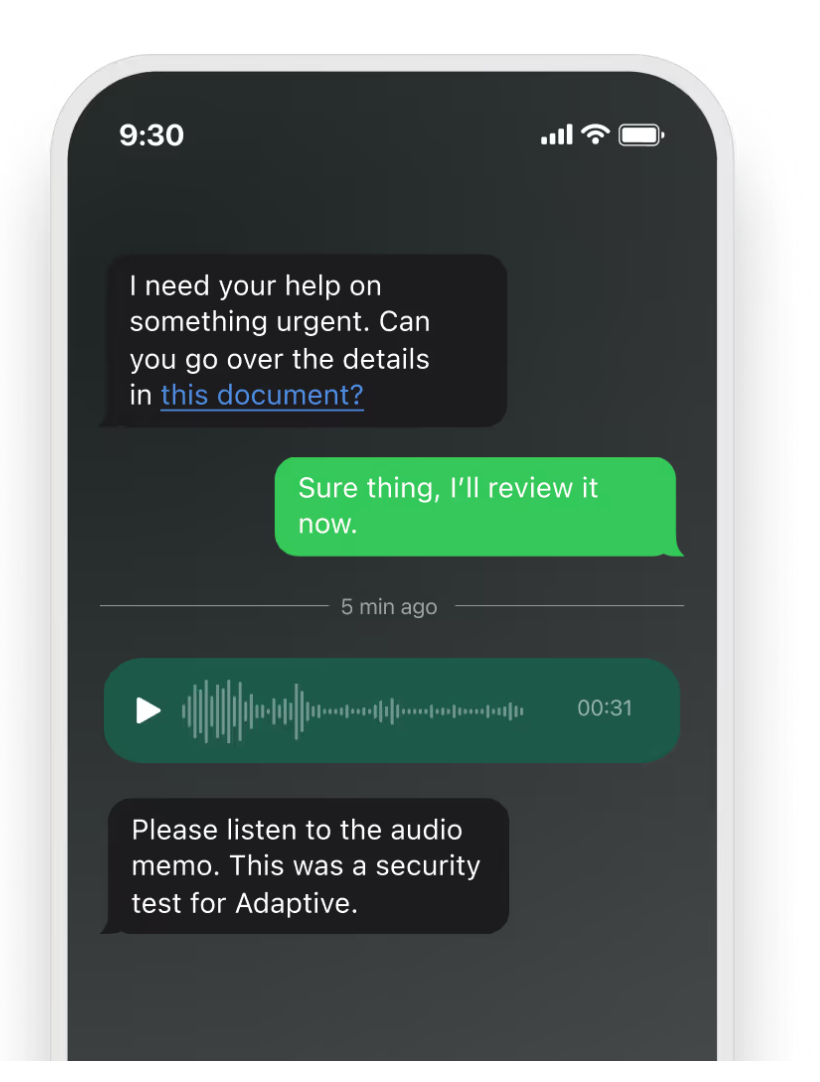
The ROI of a mature phishing training program extends far beyond lower click-through rates. Organizations see measurable reductions in incident response time, improved reporting rates, and quantifiable drops in real-world breaches. Adaptive Security advances this model by mirroring the psychological realism of modern attacks: multi-stage, trust-based, and conversational.
By simulating follow-up lures, tone shifts, and authentic-looking correspondence, Adaptive enables security leaders to measure user behavior across roles and departments. The result is a more reliable indicator of organizational readiness—and a proactive defense against attackers who weaponize trust.
Why legacy training falls short for modern barrel phishing threats (and what to do instead)
Traditional phishing training caters to a different era of cybersecurity—one dominated by single-click scams, obvious red flags, and static “don’t click the link” modules. However, like spear phishing and other advanced types of attacks, barrel phishing doesn’t follow that script. It evolves, personalizes, and unfolds over multiple touchpoints.
Static modules can’t keep pace with dynamic threats. Legacy programs often rely on one-off videos or quizzes that fail to mirror how modern attacks actually happen. Real attackers don’t strike once; they follow up, shift tone, and adapt their approach based on how the target responds. Without a multi-stage context, employees never get to practice recognizing those shifts.
Attackers personalize—your training should, too
Most platforms ignore role-specific escalation. In real campaigns, attackers tailor messages to the recipient’s function. For example, finance teams see invoice requests, HR receives benefits updates, and executives get partner outreach. True cybersecurity readiness requires understanding who attackers are most likely to target and which workflows they can exploit.
Adaptive Security closes the gap through prevention strategies that mirror real-world escalation. Its simulations follow up, shift tone, and build rapport before delivering the malicious cue—just like live attackers. These behavioral insights reveal how different teams react under evolving pressure and where retraining will have the greatest impact.
Organizations replacing KnowBe4 and Proofpoint tell us Adaptive’s simulations drive real behavior change. Instead of checking a compliance box, they create measurable risk reduction, training employees to detect subtle cues that legacy programs overlook.
By replicating the cadence and psychology of modern phishing, Adaptive turns training into true readiness and transforms awareness from a static exercise into a living defense.
Equipping your organization against today’s barrel phishing threats
Barrel phishing proves that not all phishing emails look dangerous. Some feel friendly until it’s too late. As attackers evolve their playbooks, organizations must move beyond checkbox anti-phishing programs and embrace real-time detection, behavioral analytics, and continuous learning.
Adaptive’s AI phishing simulations help teams recognize trust-building patterns before they escalate into full cyber attacks. By mirroring real-world follow-ups and tone shifts, they turn training into measurable defense, helping you shift from reactive to proactive security readiness.
Want to see how your team handles a real barrel phishing attempt? Book a custom demo of Adaptive’s Security Awareness Training today.
FAQs about barrel phishing
What’s the difference between barrel phishing and trap phishing?
Barrel phishing builds credibility first, often appearing to come from a trusted source, then delivers malicious links in a follow-up. Trap phishing skips the rapport-building stage and goes straight to manipulation.
Both rely on deception. However, barrel phishing uses trust to set up its attack, while trap phishing uses bait to lure victims immediately. Each reflects the growing sophistication of modern phishing tactics.
Who’s most likely to be the target of barrel phishing attacks?
Executives, finance, HR, and legal staff are frequent targets of email attacks that appear legitimate or contextually relevant. However, attackers can exploit any employee with system access or a vendor relationship if they gain the recipient’s trust.
How can organizations defend against barrel phishing?
Strong technical controls help, but awareness is essential. Employees should verify unusual requests, avoid sharing login credentials, and report suspicious or malicious content.
Adaptive Security’s simulations teach teams to detect tone shifts, layered urgency, and other behavioral cues that signal evolving phishing threats.
What’s the best platform for trap phishing prevention and awareness?
Leading phishing awareness and prevention solutions include:
- Adaptive Security: dynamic, AI-driven phishing simulations that replicate multi-stage attacks and measure real behavior change
- Cofense: focused on phishing response and reporting workflows
- Hoxhunt: gamified awareness training for enterprise teams
- Mimecast: comprehensive email protection with integrated filtering tools




As experts in cybersecurity insights and AI threat analysis, the Adaptive Security Team is sharing its expertise with organizations.
Contents




.avif)





