Human error remains the costliest problem in cybersecurity; a 2024 Verizon report shows that the human element is involved in roughly two-thirds of all breaches. With the average cost of a phishing-origin breach now estimated at nearly $4.9 million, even small behavioral improvements, such as reducing phishing click rates by 5%, can save hundreds of thousands of dollars for large enterprises.
Technical defenses are stronger than ever, and attackers know it. That’s why they’re now targeting the weakest link in the chain: human behavior. Whether it’s a phishing email designed to steal credentials, a multi-factor authentication (MFA) fatigue attack bombarding employees with push notifications until they approve one, or a deepfake voice request mimicking an executive’s voice to authorize a wire transfer, attackers know people are easier to trick than systems.
That’s why more security leaders are turning to Human Risk Management (HRM). Rather than relying solely on technical defenses or one-off compliance training, HRM turns human vulnerability into a controllable variable, transforming people from the biggest attack surface into the organization’s strongest security control.
In this article, we’ll define human risk management, explain why people are the largest attack surface, and share a phased framework. We’ll also show how new-generation security awareness training platforms, such as Adaptive Security, turn behavioral data into measurable risk reduction.
What is human risk management?
Human risk management (HRM) is the practice of identifying, measuring, and mitigating cybersecurity risks resulting from human behavior. It examines whether employees click on a phishing link, report suspicious activity, or follow security policies, and it uses that information to guide training and support.
The goal isn’t to point fingers but to help people make safer choices in the moments that matter. Unlike traditional security awareness training (SAT), which often stops at delivering generic content, HRM relies on concrete behavioral data to guide action.
HRM looks at signals like:
- Results from phishing or smishing (SMS phishing) simulations (who clicked, who reported, etc.)
- Training engagement (who completed modules, who dropped off)
- Policy habits (password reuse, MFA adoption, shadow IT)
- Real-world incidents (e.g., repeated helpdesk tickets or misdelivery of sensitive data)
A common misconception is that HRM creates a “blame culture.” In fact, the opposite is true. It shifts the focus away from punishing mistakes and toward building resilience.
While most breaches involve human error (68%, according to Verizon’s 2024 DBIR), it’s not because people don’t care. Attackers are constantly inventing smarter tricks—such as deepfake audio calls or AI-crafted spear-phishing—that exploit psychological vulnerabilities. HRM helps organizations level the playing field by giving employees the tools, practice, and feedback to respond effectively.
Why human behavior is your organization’s largest attack surface
Threat actors know that one of the fastest ways into an organization is through its employees, meaning that human error is just one more attack surface when it comes to protecting important data. That’s why it’s important to determine which methods cybercriminals rely on when they target an organization’s employees.
Common entry points include:
- Phishing emails that trick someone into clicking a link or sharing credentials
- MFA fatigue attacks, where employees accept fraudulent login prompts just to make the notifications stop
- AI-driven impersonation, such as deepfake CEO calls or realistic payroll scams that create pressure to act quickly without verifying
Most traditional training doesn’t change behavior in high-pressure moments. Watching a video about phishing once a year doesn’t prepare an employee for a convincing spear-phishing attack that appears to come from their manager at 4:59 p.m. on a Friday. Human risk management, however, measures how people actually respond to these scenarios (e.g., who reports, who ignores, and who clicks), which helps organizations see where the real risks are and intervene with targeted support.
Next-generation security awareness training platforms, such as Adaptive Security, consider employee behavior to assign risk scores, helping security teams identify which individuals or groups pose the greatest risk and why. That makes it easier to act where it counts.
For instance, if a department reports phishing attacks too slowly, SAT software can run quick drills until faster reporting becomes the norm. If employees fall for voice-based scams, they can practice with realistic AI call simulations and learn how to verify before acting.
The APTT framework for human risk management
The best way to put human risk management into action is to take it step by step. Assess, Prioritize, Tailor, and Track—that’s the APTT Framework. Start by measuring how people behave, then focus on the riskiest areas, adjust training to fit those behaviors, and keep track of progress over time.
This phased approach makes it easier to build a program that actually reduces risk instead of just checking the box on training.
1. Assess behavioral risk
The first step in human risk management is understanding where your people stand today. That means gathering data on how employees actually behave in real-world or simulated scenarios, not just how they perform on annual training quizzes.
Some of the most useful indicators include:
- Phishing simulation results: who clicks, who reports, and how quickly
- Engagement levels: whether employees complete training modules or drop off midway
- Click behavior and response patterns: who repeats risky actions and how they react under pressure
These insights don’t come from one place. To get a complete picture of human risk, security leaders need to connect data across systems that capture both training behavior and real-world activity. Common sources include:
- SIEM tools and security logs that track actual security events such as credential misuse, suspicious logins, or repeated policy violations
- Training platforms and LMS logs that show how employees engage with awareness content, including who completes modules, who skips them, and where drop-offs happen
- HRIS data that link behaviors to job roles, departments, or access levels, helping you see if high-risk behaviors are concentrated in areas with sensitive privileges
When you combine these signals, a clearer picture emerges of where your human attack surface is most exposed.
For example, people fall for phishing attacks fast. According to the 2024 Verizon DBIR, the median time from opening a phishing email to clicking the link is 21 seconds; it takes an additional 28 seconds to enter data. This shows how small mistakes or snap judgments can lead to serious breaches.
This is where a platform like Adaptive Security can handle some of the heavy lifting. The platform combines reports from your SIEM, training logs, and HR systems automatically so you don’t have to. You get a clear risk score for each person or department, allowing you to identify at a glance who requires the most attention and why.
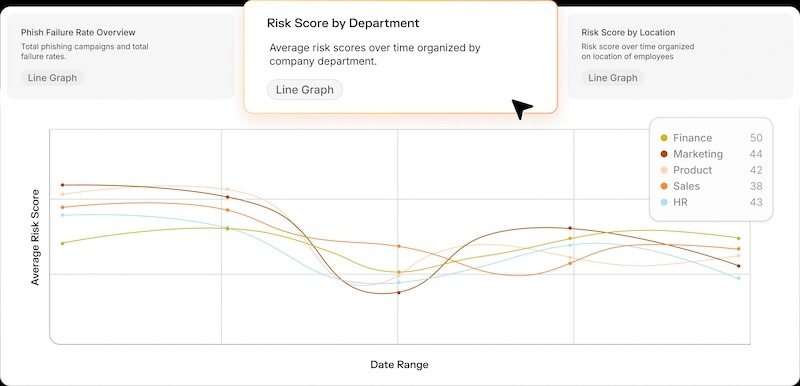
2. Prioritize by risk concentration
Not all users carry the same level of risk. A single mistake from someone in finance, an executive with wide access, or an engineer with production credentials can have a far greater impact than the same slip in a lower-risk role. That’s where role-based, behavior-driven risk scoring comes in.
Business email compromise (BEC) scams, which often target executives and finance teams, accounted for more than $2.9 billion in adjusted losses in 2023, according to the FBI’s IC3 report. Attackers know who holds the keys, and they concentrate their efforts there.
By focusing on these high-impact roles, you avoid spreading resources too thin. For example:
- Finance teams may require additional training and AI phishing simulations on wire fraud and invoice scams.
- Executives may need coaching on spotting deepfake calls or AI-crafted impersonation attempts.
- Engineering teams may require reinforcement in areas such as code repository access, MFA adoption, and shadow IT.
Where most programs stop at job titles, Adaptive Security goes further. Beyond clicks, it correlates behavior across phishing response, MFA fatigue, and policy adherence to generate a multidimensional risk score for every team. This behavioral intelligence gives CISOs a real-time view of which human behaviors are most likely to lead to a breach and where to intervene first.
With this insight, security leaders can immediately see whether their highest-risk group is the C-suite, finance, or engineering and prioritize interventions where a single error could cause the most damage.
3. Tailor interventions
Once you see who is at risk and why, you don’t need to send everyone the same training. You’ll want to deliver the right training to the right people at the right time.
This means going beyond roles, adjusting training based on actual behavior, and simulating attacks that are most risky to a person or team.
Effective tailoring can look like:
- Sending follow-up nudges after someone fails a phishing test, paired with a short micro-learning session that corrects that one mistake
- Running a deepfake CEO fraud voice request simulation for managers, so they can practice verifying unusual requests in a safe environment
- Using spear-phishing templates that mimic a department’s real vendors or jargon, rather than generic phishing emails
- Triggering adaptive lessons for employees who repeatedly ignore MFA prompts, teaching them why “MFA fatigue approvals” are risky and how to handle them correctly
- Delivering short, scenario-based refreshers to teams that handle sensitive data (like Finance or HR) when policy violations occur (for example: a 2-minute interactive walkthrough that reenacts the same file-sharing mistake and guides the employee through the correct, secure workflow step by step)
Adaptive Security supports such tailored interventions by linking training directly to behavior. If someone fails a phishing simulation, the new-generation security awareness training platform delivers a short micro-lesson immediately, turning the failure into a learning opportunity.
Adaptive also supports multi-channel simulations, including email, SMS, voice, and even deepfake scenarios, allowing employees to practice against the types of attacks they’re most likely to encounter.
4. Track change over time
The only way to know if your HRM efforts are working is to track how behavior changes over time. Instead of measuring success by training completions, focus on metrics that actually show risk reduction and a stronger compliance posture:
- Lower click rates on phishing and smishing simulations
- Faster reporting of suspicious messages or incidents (shorter response latency)
- Higher engagement with micro-learnings and simulations over time
- Shrinking high-risk user groups over time
These metrics show whether employees are developing stronger habits or if they still need additional support. For example, if your phishing click rate drops from 18% to 6% over six months, that’s a clear indicator of progress.
Boards and CISOs don’t want to hear how many employees completed training. They want to know how human risk is trending, whether overall exposure is declining, compliance posture is improving, and human-layer risk is being brought under control.
AI safety tools, like those offered by Adaptive Security, make this measurable. The platform automatically aggregates behavioral signals, from phishing, MFA, and training data, into monthly risk scores that clearly show where risk is rising or falling. These metrics integrate seamlessly with Power BI, Tableau, and GRC dashboards, making it easy to turn behavioral data into board-level insights.
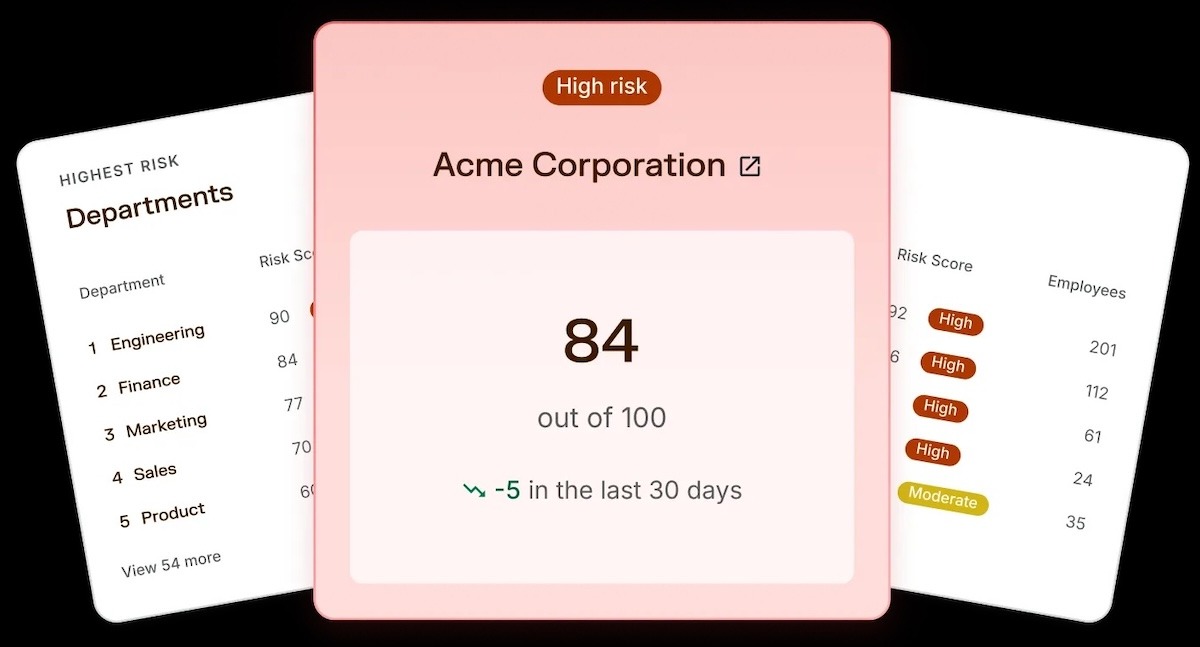
This means you can go from: “We ran 20 trainings this quarter” to “We reduced high-risk users by 40% last quarter and improved phishing resilience by 30%, directly lowering our human-layer breach exposure.”
How Adaptive supports human risk reduction
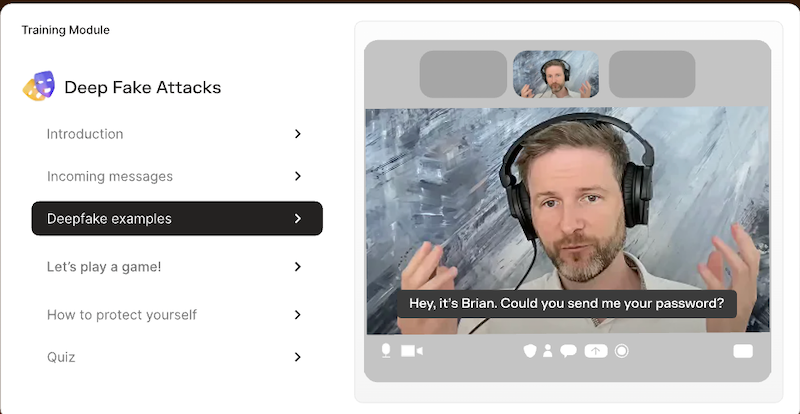
Adaptive ties training directly to behavior, not just theory. When someone fails a phishing simulation, the system immediately displays a focused micro-lesson, ensuring the learning is timely and relevant. Because Adaptive supports simulations across email, voice, SMS, and deepfake facades, your teams can train against the kinds of attacks they’ll actually see.
Adaptive also calculates risk scores and dynamically groups users. This allows you to identify which individuals or teams pose the highest human risk and adjust training accordingly. This lets you focus on where training matters most, rather than wasting effort on low-risk users.
Finally, Adaptive provides dashboards and reporting suitable for CISOs and boards. These tools enable you to track trends over time, whether high-risk behavior is decreasing, reporting is improving, or training interventions are effective. This helps you make better decisions based on real data, not guesses.
Make your people your strongest security control
Human error will always be part of the security equation, but it doesn’t have to be a constant source of stress for you and your team. When you measure how people behave, focus on the riskiest groups, give them training that matches the threats they face, and watch how those habits improve over time, you reduce the number of openings attackers can use.
The payoff is twofold: employees feel more confident handling threats, and leadership gains proof that security awareness is driving real risk reduction. Now is the time to shift from awareness for its own sake to measurable behavior change, and start making your people the strongest part of your defense.
Want to see how this looks in practice? Try Adaptive Security’s demo and explore how behavior-based training works in real scenarios.
FAQs about human risk management
What is human risk in cybersecurity?
Human risk refers to the likelihood that employee behavior, whether through mistakes, negligence, or manipulation, will lead to a security incident. For example, an employee may unknowingly click a phishing link, reuse passwords, ignore security updates, or fall for social engineering.
Is human risk management the same as security awareness training?
No. While security awareness training (SAT) is a key component of building cyber-resilient organizations, helping employees understand common cyber threats and good security practices, human risk management (HRM) goes a step further.
It measures behavior, identifies higher-risk groups, and tailors interventions to reduce those risks. SAT can be part of HRM, but HRM is about continuous monitoring, feedback loops, and improvement, not one-off courses.
What are some common pitfalls of operationalizing human risk management?
A big mistake is managing human risk like a checkbox training program, where the goal is just to show that cybersecurity training was completed. Another pitfall is sending the same generic cybersecurity awareness content to everyone, which doesn’t prepare high-risk groups like finance or executives for the attacks they’re most likely to face.
Some teams also forget to measure results, so they can’t tell if behavior is improving. Worst of all, many human risk management programs end up shaming employees for mistakes instead of giving them safe ways to practice and get better.
What are the best tools to support human risk reduction?
Some of the best human risk management platforms to support human risk mitigation and ward off cyber attacks include:
- Adaptive Security: Risk scoring, behavioral analytics, multi-channel AI-powered simulations, and executive-ready reporting
- KnowBe4: Awareness training and phishing simulations
- Proofpoint Security Awareness: Role-based training content
- Cofense PhishMe: Phishing detection and reporting
- Hoxhunt: Gamified training with personalized challenges




As experts in cybersecurity insights and AI threat analysis, the Adaptive Security Team is sharing its expertise with organizations.
Contents










