According to Verizon’s 2024 Data Breach Investigations Report, ransomware and other extortion tactics account for roughly a third of today’s data breaches. The question for most organizations is no longer if ransomware will strike but when.
Attackers have also changed how they operate. Instead of relying on complex coding, many now use ransomware-as-a-service, renting ready-made attack kits online. Paired with AI-assisted payloads that generate realistic emails and cloned voices, these tools make it easier than ever to reach employees directly and slip past even the strongest defenses.
That’s why human behavior has become the new threat surface. A single careless click or approval of a fake request can lock systems, disrupt operations, and damage trust in minutes.
Ransomware training helps close that gap. It gives employees the awareness and confidence to recognize threats before they spread and respond quickly when something feels off.
In this article, you will learn a clear, step-by-step approach to building ransomware readiness across your organization. Whether you lead IT, HR, or security awareness programs, you will find practical ways to turn human behavior from your biggest risk into your strongest defense.
Understanding how ransomware reaches your people
Ransomware is a type of malware that locks or encrypts data and demands payment for its release. It often starts with something deceptively simple that exploits trust, urgency, or distraction.
Recent research shows that 69% of ransomware incidents start with a phishing email. Many attackers don’t break in—they log in, often with the help of an unsuspecting employee. Here are the most common entry points your people need to recognize:
- Phishing emails and attachments: malicious invoices, HR documents, or IT alerts designed to look legitimate
- Drive-by downloads: compromised websites that silently install ransomware when someone clicks a link
- Remote access abuse: stolen or weak passwords that allow hackers to move in through VPNs or RDP
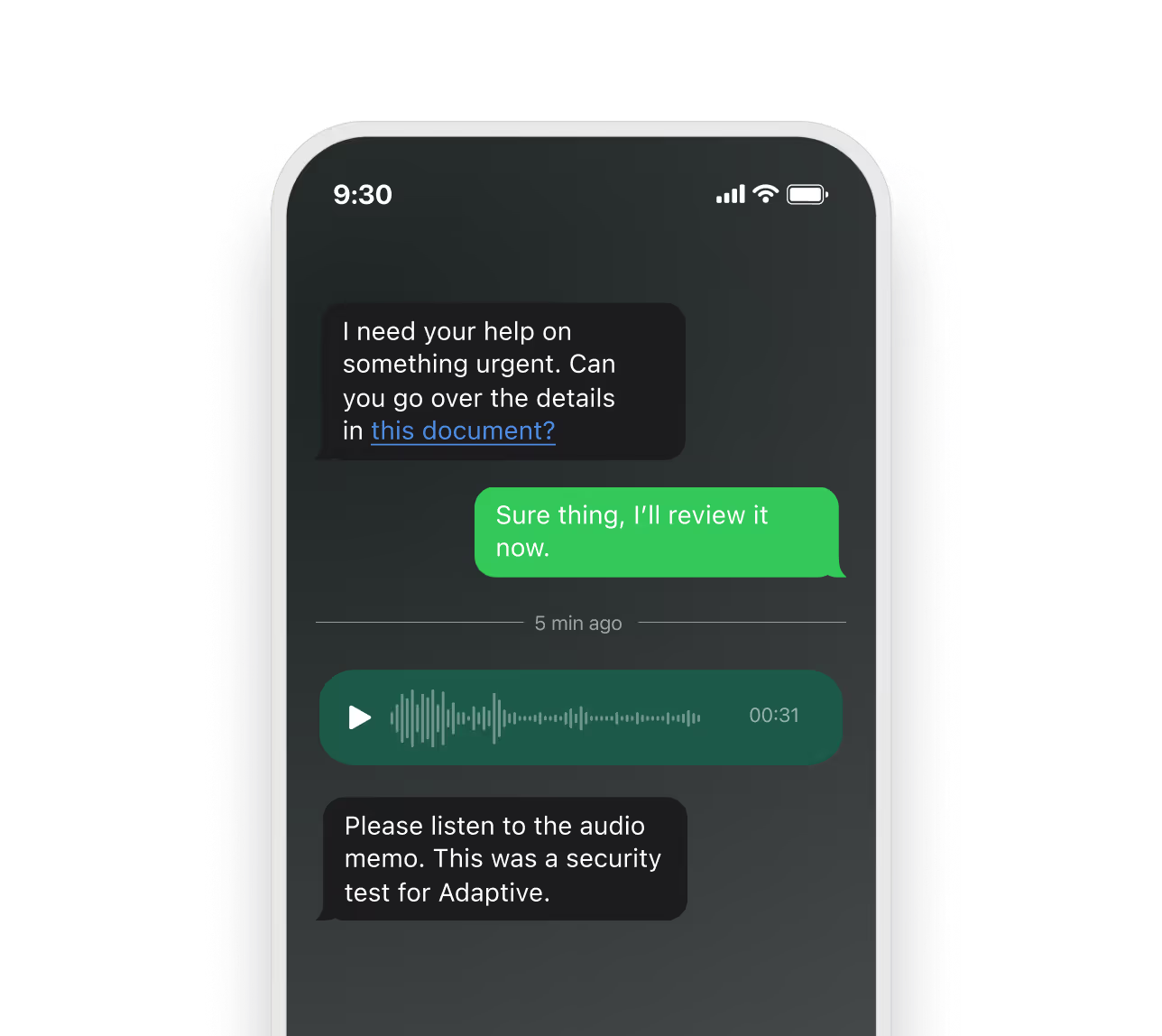
- Deepfakes and voice clones: AI-generated calls that mimic leaders or colleagues to rush approvals
These socially engineered entry points have become more advanced and harder to spot. Attackers now use AI to create voice clones, deepfakes, and realistic chat messages that mimic leaders or colleagues. A message asking for a “quick login reset” or an urgent payment approval can sound completely legitimate when paired with a familiar voice or tone. These tactics exploit trust and team dynamics, making urgency feel natural and requests harder to question.
➜ To help employees recognize these tactics, you can use resources such as this social engineering risk playbook to strengthen awareness and response across teams.
A phased framework for effective ransomware training
Ransomware resilience depends on more than technology. A strong human firewall is often the last line of defense when cybercriminals slip past technical controls. Employees learn best through layers of practice, role-specific training, and ongoing reinforcement.
Here's a phased framework that builds those layers and turns awareness into lasting behavior change.
1. Baseline education
Start with the essentials. Employees must understand what ransomware does, how it spreads, and the kinds of tricks attackers use to gain access. The goal is not to overwhelm but to make concepts easy to grasp and memorable.
A clear baseline might cover:
- How ransomware locks files and demands payment
- Common entry points such as phishing attacks, unsafe downloads, and weak remote access
- Early warning signs like unusual file names, system slowdowns, or suspicious login prompts
The format of this training matters as much as the content. Short videos, interactive modules, and real-world case studies keep people engaged far better than a static slideshow.
For example, showing how a hospital faced downtime after one employee clicked a malicious attachment can drive home why attention to detail matters. Fear-based approaches, on the other hand, often backfire by creating anxiety without building confidence.
2. Simulation-based learning
Once employees understand the basics, they need to experience realistic scenarios. Simulations give them a safe environment to practice spotting red flags and choosing the right response.
Consider running exercises such as:
- A phishing email with a ransomware-laced invoice attachment
- A spoofed IT helpdesk message that urges a quick password reset
- A fake “urgent payment” request from what appears to be an executive account
The power of simulations lies in immediate feedback. When someone clicks on a decoy link, they should see a quick explainer that highlights what they missed and how to handle it next time. This feedback loop turns mistakes into learning opportunities.
Some phishing simulation and cybersecurity awareness training platforms, like Adaptive Security, even generate scenarios with AI to reflect the latest attacker tactics, helping employees practice against threats they are likely to encounter in real life.
3. Role-specific risk training
Not every employee faces the same cyber threats. Finance staff are more likely to be targeted with fraudulent invoices while engineers might see lures that mimic system update requests. Similarly, executives often receive highly tailored spear-phishing or even voice-cloned messages (vishing).
Consider how different roles handle sensitive information and face unique cyber risk profiles.
Use your simulation data to identify which roles show the highest click rates or longest dwell times on suspicious content. Then customize training to address the specific vulnerabilities those teams exhibit.
Adaptive Security's platform can auto-customize content based on role and past behavior, which means your highest-risk employees automatically receive more focused training.
4. Reinforcement and retesting
Training should never be a “check the box” event. Habits fade quickly if they’re not reinforced. To keep ransomware awareness sharp, organizations should deliver refresher content regularly and run drills that mirror evolving attacker tactics.
Effective reinforcement can include:
- Quarterly ransomware-focused simulations with updated lures
- Short refresher videos or quizzes delivered through internal channels
- Policy updates tied to insights from training performance, so employees see the link between their actions and company standards
Repetition builds resilience. Each cycle strengthens recognition skills and reduces response times. The outcome is not just lower click rates but a culture where employees treat ransomware awareness as part of their daily responsibilities, not an occasional exercise.
Measuring the impact of ransomware readiness
Training only delivers value if you can prove it changes behavior. Measuring progress shows whether employees are building the reflexes to stop ransomware before it spreads. It also gives cybersecurity leaders concrete data to share with executives and boards who want to see evidence of reduced risk.
Several metrics can highlight readiness:
- Click rates: How often employees interact with malicious links or attachments during phishing simulations. A steady drop over time indicates stronger awareness.
- Dwell time: The length of time between clicking a lure and reporting it to IT. Shorter dwell times suggest people are catching their mistakes and acting quickly.
- Response latency: How long it takes teams to react once a suspicious email or file is reported. Fast incident response shows collaboration and process maturity.
- Lateral movement performance: How well employees notice and report unusual activity, such as unexpected file access attempts.
Phishing simulation results often serve as the clearest proxy for ransomware readiness. When employees consistently identify lures and report them in time, you gain confidence that they'll apply similar vigilance should they encounter a real attack.
To make this manageable, many teams use dashboards that aggregate performance across drills. Tools like Adaptive provide trend views that show how different departments are progressing, where risks remain, and whether reinforcement is working. This visibility turns training from a box-ticking exercise into a measurable driver of resilience.

What most ransomware training misses
Even with multiple platforms on the market, many ransomware training programs still struggle to keep employees engaged and prepared. The issue often lies in how the content is delivered and maintained.
Common gaps in legacy training platforms include:
- Static material: Many programs rely on long, outdated videos or modules that users describe as “too simplistic or repetitive” for more experienced or technical employees. Attackers evolve fast, but training courses rarely keep pace.
- Limited scenarios: Simulations often stop at entry-level phishing emails and ignore deeper stages like lateral movement or macro-enabled file attacks. Several reviewers noted a lack of “real-world scenarios” and “highly tailored learning paths for specific roles.”
- Missing context: Messages that create urgency or fear are the backbone of real ransomware campaigns, yet simulations rarely mimic that tension. Employees never practice responding to a request that feels “time-sensitive” or “escalating.”
- Customization challenges: Users frequently mention that dashboards feel “clunky to navigate” and "customization takes work.” Without flexible targeting, admins struggle to align content with departmental risks.
- Limited feedback loops: Many employees finish quizzes without seeing “which answers were wrong and what the correct answer is,” leaving gaps in understanding. Others ask for “more variety in the content format,” such as short videos or infographics, to keep learning fresh and engaging.
- Weak integration with broader security initiatives: Training often runs in isolation instead of connecting to information security policies, risk mitigation strategies, or compliance frameworks like ISO 27001 and NIST. It should also align with regulations such as GDPR in Europe and HIPAA in the healthcare industry.
Organizations that address these weaknesses can transform training into something relevant and memorable. When content reflects real cyberattack patterns, offers immediate feedback, and adapts to employees’ roles, it builds confidence instead of fatigue.
Ready to modernize your organization's ransomware training?
The strongest defense against ransomware comes from training that builds habits: clear education, hands-on practice, role-specific lessons, and reinforcement over time. Each phase reduces the chance that a single click or rushed approval will open the door to an attack.
A behavior-first approach matters since attackers focus on people, not just systems. Preparing employees to recognize urgency tricks, spot suspicious files, and act quickly when something feels wrong, transforms the “weakest link” into an active defense layer against cybercrime.
Adaptive’s AI-powered simulation engine generates scenarios that mimic the evolving tactics cybercriminals use. That gives your team experience with realistic threats and provides you with measurable insights on progress.
Take the next step to make ransomware readiness a lasting part of your culture. Book a demo to see how Adaptive builds ransomware resilience from the inside out.
FAQs about ransomware training for employees
How often should I run ransomware simulations?
Run simulations at least quarterly to keep awareness fresh without overwhelming employees. Many organizations increase frequency during periods of higher threat activity or after onboarding new staff. Regular practice ensures teams treat security checks as part of their routine, not a once-a-year event.
Can ransomware training reduce insurance costs?
Yes. Many insurers consider security awareness programs when calculating premiums. Demonstrating consistent ransomware training and measurable results, such as lower phishing click rates, shows reduced organizational risk. That evidence can strengthen your case for better coverage terms and lower costs.
What's the difference between ransomware training and phishing training?
Phishing training focuses on spotting deceptive messages, while ransomware training covers the full attack chain. Employees learn to recognize not only suspicious emails but also scams, malicious attachments, credential theft or phishing attempts, and signs of ransomware spreading across systems. The broader scope prepares teams for real-world escalation.
Do small and mid-sized teams need ransomware-specific training?
Absolutely. Smaller organizations are often prime targets because attackers assume defenses are weaker. Training gives these teams the tools to recognize and stop attacks early, even with limited IT resources. Consistent ransomware-specific practice builds resilience that scales with growth.




As experts in cybersecurity insights and AI threat analysis, the Adaptive Security Team is sharing its expertise with organizations.
Contents




.avif)





