A finance director receives a voicemail from her company's CFO, urgently authorizing a last-minute payment to close an overseas deal. The voice was familiar, the tone confident, the context believable. Within minutes, $25 million is gone.
It turns out, the "CFO" was an AI-generated deepfake. On top of that, scammers bypassed every technical control, from secure email gateways to multifactor authentication.
Incidents like this are redefining what a breach looks like. Firewalls, endpoint detection, and network segmentation still matter, but they don't protect against a convincing voice or message that tricks a human into opening the door.
That's where breach and attack simulation (BAS) comes in. Traditionally, BAS tools run simulated attacks across your environment to test whether defenses can detect and stop them. But most BAS solutions focus only on the technical layer. However, a modern, full-spectrum BAS program requires more. While legacy BAS focuses on technical controls, Adaptive extends this concept by validating the human response, the most common point of initial compromise
To stay ahead, security teams need to expand BAS beyond system validation to include human-driven attack scenarios like phishing, vishing (voice phishing), and deepfake impersonation.
This article breaks down how to build a full-spectrum BAS program that tests both your technology and your people, closing security gaps and improving cyber defense readiness.
What is breach and attack simulation (BAS)?
Breach and attack simulation (BAS) is a method for testing whether your defenses can stop real-world attacks. Instead of waiting for an incident, BAS lets you safely run controlled attacks across your organization to see what would happen if a real threat attempted the same thing.
Think of BAS as a constant, automated red team. It mimics what attackers do, from sending phishing emails to moving laterally inside a network, and checks whether your systems catch and contain those moves.
Traditional BAS focuses mostly on your technical defenses:
- Endpoint detection tests whether your security tools (like your antivirus or endpoint detection tool) can recognize and block known malware before it spreads.
- Network controls check if your firewall cybersecurity defense or segmentation rules (the barriers separating parts of your network) can stop attackers from moving from one computer to another.
- Lateral movement examines what happens if one employee's laptop is compromised. Can the attacker reach shared drives, databases, or admin tools, or do your controls contain them?
These simulations reveal how your layered defenses behave together. Your endpoint agent may detect the payload, but your alert never reaches the SOC.
For example, perhaps segmentation rules are effective until a new cloud app circumvents them. BAS helps you catch those silent technical and human-centric security errors early, guiding remediation.
Why BAS matters for a proactive security posture
Despite the fact that the threat environment changes weekly, traditional security testing typically occurs only once or twice a year. A strategy that worked last quarter may not be effective today.
That's why BAS is so valuable: It provides continuous testing and real-time visibility into your organization's security posture.
By running controlled attacks on a schedule, you can:
- See where cyber threats slip and fix those gaps.
- Validate that new patches, configurations, or integrations haven't weakened protection elsewhere.
- Turn vague confidence ("we think it's covered") into proof ("we know this control blocked it").
- Give leadership detailed reports for audit and prioritization of fixes.
The gap in traditional breach and attack simulation approaches
Most BAS programs do an excellent job of testing systems, but they often miss the first part of an attack. Before a payload ever reaches your endpoint or network, it usually passes through a human. That's where traditional breach and attack simulation begins to fall short.
What's missing? Human behavior as a threat surface
Most BAS tools test machines, including endpoint agents, network firewalls, and lateral-movement pathways. However, they overlook that human-centric cyber risk remains one of the most common attack vectors.
One IR report found that social-engineering attacks resulted in data exposure in 60% of cases—a significantly higher rate than overall attacks.
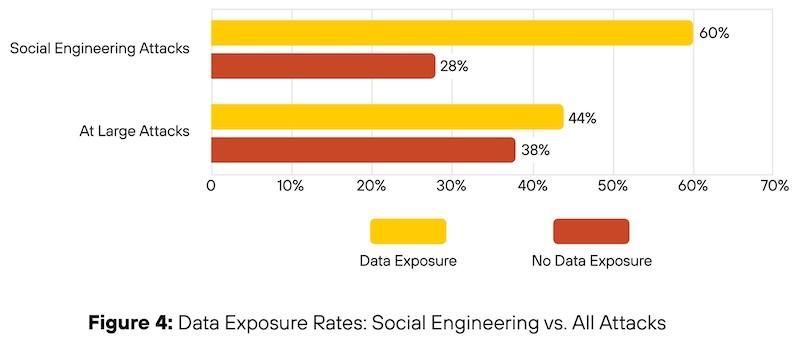
The problem isn't just that employees make mistakes; it's that attackers have become experts at designing situations that make them.
For instance, today's phishing campaigns use personal data from LinkedIn or stolen credential dumps to craft nearly perfect messages. Threat actors follow up with phone calls or Slack messages to "verify" requests, creating social pressure. When a user clicks, the compromise opens a door to your internal systems, where the traditional BAS tools take over.
But if your simulations never test the human-centric security part of that chain, you're only addressing half of the problem. You might confirm your endpoint detection and response (EDR) software blocks a payload, but not that someone would have delivered it into the network in the first place.
Why technical controls aren't enough for modern BAS
Purely technical defenses can't keep up with the evolution of social engineering. AI-driven phishing can create emails that sound exactly like those of your executives, complete with logos and personalized details. Secure email gateways can catch some but not all of these.
In only two years, the Cofense PDR platform identified 1.5 million malicious emails that successfully bypassed customers' Secure Email Gateways (SEGs). That's a 37% increase over 2022 and a 310% jump since 2021. Put another way, one malicious email slips past a SEG every 57 seconds.
A single click or voice confirmation can trigger the entire breach sequence: credential theft, privilege escalation, lateral movement, and ultimately, data exfiltration.
This is why technical validation alone isn't enough. To understand your security posture, BAS needs to include behavioral simulations, such as phishing, vishing, impersonation, and even deepfake-based attack scenarios.
Expanding BAS to include human threat simulation
Every major breach of the past decade, whether it was a corporate wire fraud or a deepfake phishing scam, started with human vulnerabilities. If traditional BAS focuses on how systems react under attack, a full-spectrum BAS framework must also test how people react. Here's how to do that.
Behavioral attack simulations
Modern cyber threats don't need to target firewalls directly. They just need to extract your personal details, which will help them earn your employee's trust. Behavioral simulations, like phishing, vishing, smishing (SMS phishing), and QR-based lures, are missing in most BAS programs.
For example, in one 2023 campaign, attackers used QR codes to bypass URL filters, a method that saw a 248% surge between Q3 and Q4 that year, according to Recorded Future.

Voice and video deepfakes add another layer of complexity. With as little as three seconds of source audio, attackers can now clone a person's voice convincingly enough to authorize wire transfers or share sensitive data.
Testing how employees respond to these cues helps build reflexes. Behavioral attack simulations build resistance and teach employees how to recognize manipulation under pressure.
This is where new-generation security awareness platforms like Adaptive Security help. Instead of using generic phishing templates, Adaptive employs AI to create context-aware phishing simulations that emulate real attackers.
The platform also measures response patterns, including who reports the attempt, how quickly it occurs, and how well your controls and people coordinate. This shows you whether the team is becoming well-versed in tackling evolving threats or not.
Why this layer of BAS is critical
Human error is responsible for over 90% of breaches, especially since the sophistication of attackers has outpaced the vulnerability management and security operations of workspaces.
In one case, Ubiquiti Networks lost $46.7 million in a business email compromise scam after employees received messages that appeared to come from senior executives, requesting urgent overseas transfers. The company later confirmed that no systems were breached, and the attackers succeeded entirely through impersonation and social manipulation.
A full-spectrum BAS program closes that gap. It treats human behavior as both a potential weakness and a line of defense. When employees repeatedly rehearse phishing or vishing scenarios, the correct response becomes muscle memory: to pause and verify first before falling for sophisticated impersonations.
Adaptive Security helps your teams build that muscle memory. For example, a simulation might send a realistic phishing email to a subset of employees. It can be a fake supplier invoice that uses the company's actual vendor naming conventions. When someone clicks the link or downloads the attachment, the platform automatically measures how employees respond.
When paired with integrations into your email gateway, EDR, and SOC tools, Adaptive also helps you assess whether the technical controls and workflows are adequate, providing a comprehensive view of both human and system readiness.
Over time, the data you receive will reveal which attack types your people are most susceptible to, which departments react fastest, and which controls need calibration.
A practical framework for integrated BAS
For a BAS program to reflect real-world threats, it has to test more than just endpoints. A modern attacker moves through your users, cloud identities, and your response playbooks.
In order to build full-spectrum coverage, structure your BAS around four layers of testing. Each layer validates a different part of your defense chain and gives you specific, measurable data you can act on.
1. Network and endpoint testing (traditional BAS)
Start with the foundation, i.e., your technical controls. Run controlled attack simulations that test whether your EDR, intrusion prevention systems (IPS), and network segmentation work as intended.
This layer provides a baseline answer that indicates whether your system is capable of detecting and stopping known attack techniques before they spread.
For example, you might simulate ransomware delivery on a standard workstation, measure how your EDR responds, then test whether lateral movement to another host is blocked. Tools like Picus, AttackIQ, or SafeBreach specialize in this layer.
2. Email and identity security validation
The next layer shifts focus from endpoints to the human-system interface where real breaches start. This includes your secure email gateway, cloud email provider (such as Microsoft 365 or Google Workspace). It also includes identity systems, such as SSO, MFA, and directory services (e.g., Okta, Azure AD, Ping Identity).
In CrowdStrike's 2023 Threat Hunting Report, 80% of intrusions began with compromised credentials. That means your email and identity tests will often reveal the weak link before anything hits the endpoint.
Test this layer by running simulations that mimic credential theft, MFA fatigue attacks, or phishing emails targeting key staff. Then check if your secure email gateway (SEG), identity provider, and SIEM detect these signals and how your incident response team acts.
In short this layer answers whether your identity and access controls are strong enough to contain an attacker who tricks a user.
3. Human behavior simulation (Adaptive's specialty)
This layer tests the part most BAS programs ignore: your people. It's also where modern, AI-powered security awareness platforms like Adaptive Security shine.
Adaptive creates AI simulations of real-world phishing, vishing, smishing, and even deepfake-based impersonation attempts to see how your employees react under pressure.
For instance, you can run a deepfake voice simulation posing as a senior executive requesting a payment approval, or a phishing campaign timed around payroll. Adaptive will track who opens, clicks, reports, or escalates, validating how users react when they think the threat might be real, and then create a behavior-based risk score for each user or department. This transforms training from a compliance exercise to a measurable, validated risk-control practice.
If the results show that finance teams hesitate less before verifying voice requests, or that marketing clicks faster on social lures, you'll have concrete data to fix gaps that attackers would exploit in real life.
4. Organizational readiness and policy response drills
This final layer tests how your company responds when something slips past both people and controls. Think of it as a controlled crisis rehearsal, where you simulate a breach from end to end to see how quickly teams detect, escalate, communicate, and recover.
In a common scenario, a simulated phishing attack compromises an employee's credentials, and an attacker (played by the BAS tool or red team) uses them to access sensitive files. The goal isn't to assign blame, but to observe how your organization responds under pressure.
Here's what that looks like in practice:
- Incident detection: Your SOC receives the alert. Do analysts recognize it as a real incident or dismiss it as noise?
- Internal escalation: How long does it take for security to inform IT, legal, and communications? Do they have a clear process, or scramble on Slack threads?
- Decision-making: Does leadership have the context to make quick calls, like isolating accounts or notifying partners, or do they wait for more precise information?
- External communication: If data was exposed, who contacts regulators or customers, and what do they say?
- Recovery: How fast are systems restored, passwords reset, and gaps patched?
These drills uncover operational friction like outdated contact lists, approval bottlenecks, or conflicting instructions between teams, which you can't see on dashboards.
Afterward, a short "hot wash" (debrief) can help document what worked and what didn't. You'll walk away knowing exactly which steps of your incident response plan held up and which still need work.
Implementing behavioral simulations in your BAS program
Once you understand why behavioral testing matters, the next step is learning how to put it into practice. These simulations work best when they're structured and reflect real risks your teams face every day. Here are some ways to incorporate them into your BAS program.
Run role-based simulations
Attackers don't send the same email to everyone in your company, and neither should your simulations. Role-based simulations are tailored to test the specific decisions, context, and pressures that employees face in their respective jobs.
For example, a finance simulation might use an email from a familiar vendor asking to "update payment details." This will test whether your team verifies the request through official channels or just updates the record.
For IT, a simulation could mimic a helpdesk ticket asking them to "reset a compromised admin account," prompting a credential-harvesting scenario. For executives and executive assistants, you might simulate a travel-related spear-phishing attempt (e.g., an urgent itinerary change or document signature request).
When you run simulations this way, you could start seeing patterns like:
- Finance clicks less often but rarely reports suspicious emails.
- IT spots scams quickly, but sometimes tests links in unsafe ways.
- Executives often don't click on suspicious messages, but instead forward them to others, thereby spreading the risk internally.
That data tells you where to focus both training and technical controls.
Tools like Adaptive Security make it easy to tailor simulations for different teams. You can either pick or create templates for departments (i.e., finance, HR, or IT) and adjust the tone so that the messages feel natural to each group. Then track how your team responds.
Include details such as who clicks, who reports, and how quickly they take action. Over time, you'll identify patterns, like which teams face the trickiest attacks or require more hands-on training, so you can focus your security efforts where they'll make the most difference.
Test across channels
Attackers don't just use email anymore; they reach people wherever they're most distracted. This can be a text that looks like a delivery update, a WhatsApp message from "IT Support," a QR code on a flyer, or even a quick phone call pretending to be a manager in a hurry.
To prepare for these threats, run simulations through different channels. Send a fake text asking employees to "verify" their credentials. Try a voice simulation where someone calls about an urgent account reset. Or place a QR code in a common area that leads to a mock phishing page. You'll quickly see where your defenses thin out.
Many companies find that while employees are cautious with email, they're far more trusting of text or phone, which is precisely where attackers are now focusing.
Use realistic, AI-era scenarios
Once you've covered basic phishing tests, you need to ensure that your simulations reflect the types of approaches attackers are using now by introducing scenarios that reflect modern and contextual attacks.
For example, send a phishing email that appears to be from your CEO, written in their usual tone and referencing a real project. Then follow it up with a short, urgent voice message using an AI-generated voice that sounds similar. Or create a multi-stage test with a fake LinkedIn message that leads to an email, followed by a phone call requesting immediate action.
Adaptive Security helps here by letting you design and deliver these advanced scenarios without needing to code or manually manage each one.

Its AI-powered scenario engine can adjust difficulty, tone, and context based on each user's role and past behavior, so executives, finance, and IT each get the kinds of threats they're most likely to face.
Rethinking breach readiness in 2025 and beyond
Most breaches begin with a person, not a system. If you're testing controls without testing human behavior, you're getting an incomplete picture of your organization's security. Today, readiness means understanding how your people, processes, and technology react together under realistic pressure.
A complete BAS program needs to test every layer—from endpoints and email gateways to employees and executive decision-making—so you know exactly how a real attack would play out, and where your next improvement should be.
Adaptive Security is built around that idea. This new-age security awareness platform extends breach and attack simulation beyond systems to people. It runs realistic phishing, voice, and impersonation drills, revealing how attacks unfold under real-world conditions.
Ready to put your team to the test? Request a demo of Adaptive Security and see how real-world attack simulations turn training into proven resilience.
FAQs about breach and attack simulation
What's the difference between breach and attack simulation and red teaming?
Red teaming is a manual exercise run by ethical hackers to test how well your organization can detect and respond to a live attack. Breach and attack simulation (BAS) is automated and runs smaller, repeatable tests every day or week.
Think of red teaming as a full-scale fire drill and BAS as the smoke detector you test regularly to make sure it still works.
How often should you run breach and attack simulations?
Run them continuously or at least monthly to tighten security controls and keep up with emerging threats. Security environments change quickly, with new software, permissions, and integrations opening fresh gaps.
Continuous BAS ensures every change is tested automatically, so you're not relying on one annual audit to catch problems.
What are the top benefits of a holistic breach and attack simulation program?
A complete BAS program provides continuous validation for both your systems and people. It identifies where technical controls fail, where human errors occur, and how long it takes your team to detect and respond.
Over time, this helps you see where cyberattacks would succeed today and fix those weak spots before they cause real damage.
Can you simulate AI-based threats like deepfakes?
Yes. Modern attack simulation tools and BAS platforms, like Adaptive Security, can simulate AI-generated voice calls, deepfake videos, and highly personalized phishing campaigns.
These scenarios help employees recognize manipulation cues, including tone, urgency, or trust triggers, that traditional awareness training often misses.




As experts in cybersecurity insights and AI threat analysis, the Adaptive Security Team is sharing its expertise with organizations.
Contents










