Huntress has gained traction in recent years for its managed detection and response capabilities, but many IT managers, SMBs, MSPs, and enterprises find its security awareness training features limited. While the platform delivers robust and engaging training, some organizations may want more granular targeting or customization beyond what’s offered.
If you’re considering Huntress for awareness training—or already using it and wondering if it’s enough—this guide explores alternatives that take a more holistic approach. From phishing simulations and deepfake detection to modern human risk reduction, we’ll help you evaluate which option best fits your organization’s needs.
Why organizations evaluate Huntress alternatives
Known for its managed detection and response capabilities, Huntress monitors networks, assists with incident response, and helps remediate cyber threats on behalf of IT teams.
However, when it comes to security awareness and threat simulation (SAT), the focus is mostly on phishing email simulations and basic awareness modules. This can leave gaps if you need to train against advanced threat scenarios like deepfake video calls, voice-based scams, or SMS phishing.
Here’s why some organizations start exploring other security awareness training platforms.
Lack of deepfake/AI-era training
Most cybersecurity solutions and awareness platforms, including Huntress, still center their training around classic phishing emails: a fake invoice, a password reset link, or a suspicious attachment. While useful, attackers today are far more sophisticated.
For example, in early 2024, U.K.-based engineering group Arup lost $25 million after fraudsters staged a deepfake video conference. A staff member joined what they believed was a legitimate call with the company’s CFO and other colleagues. In reality, the CFO and participants were AI-generated clones, and the employee was tricked into authorizing 15 transfers to multiple bank accounts in Hong Kong.
These new AI-driven threats go beyond “clicking a bad link.” They target human trust in voices, faces, and even live conversations. That’s why many IT leaders need platforms that train employees to spot manipulation in this new AI era, not just emails.
Fortunately, some vendors are starting to address this head-on. Adaptive Security, a next-gen security awareness training and cybersecurity platform, focuses its awareness training on realistic deepfake voice and video scenarios. This training approach helps teams practice what it’s like when an attacker impersonates a CEO on a call or fakes a trusted colleague’s voice.
Cost and contract considerations
Because security budgets aren’t unlimited, IT managers must balance employee training with other investments, including endpoint protection, EDR/XDR (Endpoint Detection and Response/Extended Detection and Response), or broader network security tools.
Huntress’ pricing structure can feel rigid for smaller teams or managed service providers (MSPs) managing multiple client accounts, particularly for long-term contracts. A 50-person firm, for example, may not want to lock itself into long-term licensing when its workforce is likely to grow or shrink.
This is why many organizations look for vendors that offer modular adoption and contract flexibility, including the ability to scale up or down without being penalized.
Scalability for SMBs, MSPs, and enterprises
Every organization’s needs are different. A small startup might only need lightweight simulations for a few dozen employees, while an MSP managing hundreds of client environments needs training that can scale without becoming unmanageable. Huntress offers a standardized model, but some teams find it doesn’t flex easily across both ends of the spectrum.
This compels many IT leaders to evaluate alternatives that can meet them where they are. It could mean starting simple for an SMB, layering in advanced simulations as they grow, or managing multiple tenants for an MSP.
Support and integration gaps
Strong awareness training only works if it fits seamlessly into existing workflows. Some Huntress users mention challenges with integrations, including tying training results back into HR systems, SIEM tools, or broader security dashboards. For MSPs, limited integration can result in extra overhead to track progress across clients.
Today, organizations need platforms that pair strong support with open integrations. They require security software that makes it easy to connect training data with the tools they already use every day, whether that’s Microsoft 365, CrowdStrike, SentinelOne, or Sophos. Others want training platforms that can connect risk metrics directly into XDR, threat detection, and threat hunting workflows to improve overall security posture and reduce human-driven vulnerabilities.
Top Huntress alternatives in 2025 (comparison table)
Huntress competitors deep dive
1. Adaptive Security
Still teaching employees to click on fake invoices when today’s threats involve someone’s voice or face created by AI? Adaptive Security, a next-gen security awareness training and simulations platform, helps you bridge that gap.
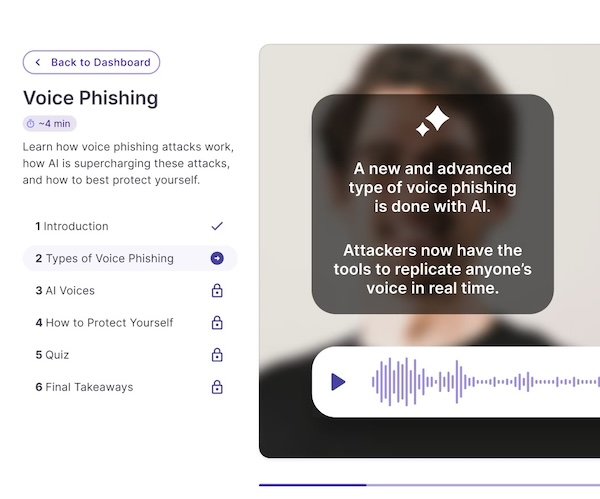
The platform is specifically designed for AI‑powered security awareness training, like deepfake voice and video phishing (vishing), SMS phishing (smishing), and GenAI email attacks.
Backed by OpenAI and a16z, Adaptive combines multichannel, hyper-realistic simulations with real-time risk scoring to help organizations prepare for situations. These include a fake video call from a “CFO” authorizing a transfer or a LinkedIn message that mirrors how a real recruiter sounds.
Adaptive measures your team’s behavior in real time with real-time risk scoring (who clicks, who reports, who hesitates) and gives a live risk score for each person and team. IT managers don’t just see “X% failed a test,” but can see clearly where human risk is concentrated and how it changes over time.
Pros of Adaptive Security:
- Fast, flexible GenAI content studio: Adaptive Security’s built-in AI content creator makes it easy to create custom training modules from scratch. You can also choose from over 100 existing modules and edit them to reflect your company’s brand or policies.
- Global-ready: Supports training in over 38 languages, making it easier for multinational teams to roll out consistent programs.
- Feels real to employees: Simulations leverage deepfakes and AI personas across email, voice, and SMS—making threat training more immersive and relevant.
- Compliance-friendly: Meets SOC 2 Type II, GDPR, and HIPAA standards, making it helpful for regulated industries needing audit-ready proof.
- Scales across org sizes: Works for small IT teams, MSPs handling multiple tenants, and larger enterprises alike.
Cons of Adaptive Security:
- Newer in the market, so it lacks the brand recognition and review volume of older vendors.
- Costs aren’t listed publicly, so you have to reach out to their sales team for custom pricing.
2. KnowBe4
KnowBe4 offers the world’s largest security awareness training library, including interactive modules, videos, games, posters, newsletters, and more. Its scale is one of its strengths: you get thousands of ready-to-use resources, along with benchmarking data from millions of users worldwide.
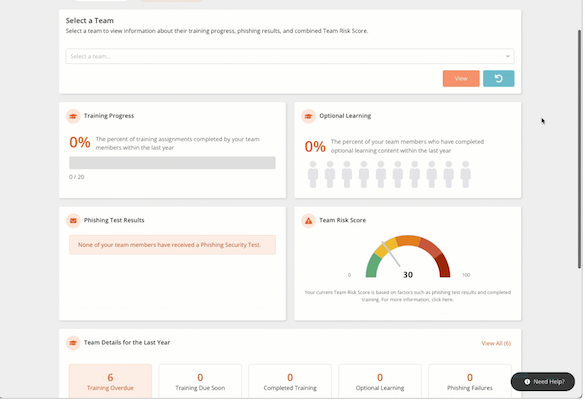
The cloud-based platform also includes gamification elements, quizzes, and automatic reminders to engage employees while training them.
Pros of KnowBe4:
- Largest content library: Thousands of templates, videos, and modules across multiple industries and use cases.
- Market credibility: Well-known, widely adopted, and supported by a vast customer base.
- Compliance coverage: Strong fit for organizations that need to meet ISO, HIPAA, PCI, GDPR, or similar requirements.
- Benchmarking data: Lets you compare employee performance against industry averages.
Cons of KnowBe4:
- While the library is massive, some users say parts of it feel dated, leading to training fatigue.
- Offers less flexibility in creating highly tailored or modern deepfake-style scenarios compared to next-gen vendors.
- It can feel expensive for SMBs, especially if you’re only using a fraction of the library.
3. Proofpoint
Proofpoint Security Awareness Training focuses on reducing human risk by pairing phishing simulations with real-world attack data. The platform filters billions of emails, providing unique visibility into the types of phishing campaigns targeting your employees. That intelligence feeds directly into its training modules, making the content highly relevant.
Alongside phishing tests, Proofpoint offers interactive microlearning modules, role-based training (e.g., finance vs. developers), and reporting dashboards for compliance.
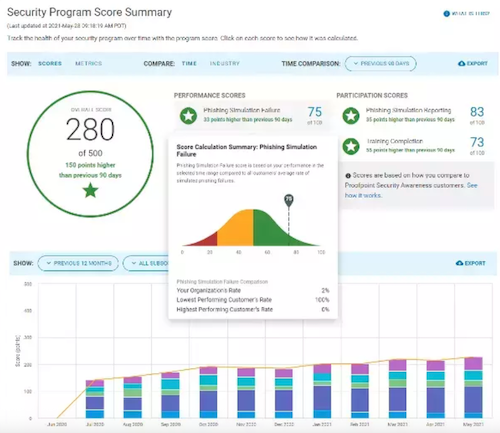
Proofpoint’s biggest differentiator is threat intelligence-driven training. Instead of relying on generic template libraries, it can use real phishing attacks targeting your company or industry to tailor simulations and training.
Pros of Proofpoint:
- Threat intelligence advantage: Uses real attack data from Proofpoint’s email security to drive simulations.
- Role-based training: Content tailored to job function (finance, executives, developers, etc.) rather than one-size-fits-all.
- Enterprise integrations: Works well if you already use Proofpoint for email security, compliance, or threat protection.
Cons of Proofpoint:
- Pricing, features, and complexity are often overkill for SMBs or MSPs.
- While effective, some modules can be dry or compliance-heavy compared to vendors with fresher, more interactive content.
- Building highly tailored or creative scenarios can take more effort than with nimbler vendors.
4. Arctic Wolf
If you're looking for an awareness training platform with a more hands-off, automated approach, Arctic Wolf’s Managed Security Awareness may be worth considering.
The platform offers bite-sized microlearning (about three minutes per session) on cybersecurity trends and threats. The training is delivered via email, with no passwords or extra log-ins required, so it feels like a regular company update. Short modules allow employees to train between tasks, and low effort and steady repetition make it easier to stick with and turn into lasting habits.
Arctic Wolf’s Concierge Security Team manages every part, including scheduling, pushing content, running phishing simulations, and sending reminders—without adding admin work on your IT team.
Pros of Arctic Wolf:
- High user satisfaction: Arctic Wolf earned a 100% willingness-to-recommend score on Gartner Peer Insights, with a near-perfect 4.9/5 overall rating as of 2025.
- Engaging, relevant content: Real users say the microlearning videos are “well-produced” and feel appropriate to modern attack types.
- Managed service means less overhead: The fully managed nature is convenient and a time saver. Your team doesn’t need to build or schedule content or do manual follow-ups.
Cons of Arctic Wolf:
- Less flexibility on content creation due to reliance on Arctic Wolf's prebuilt content flow.
- Bundled as part of their broader SOC offering, which can feel heavy if you only want awareness training.
- Pricing isn’t listed, so budgeting requires talking to the sales team.
5. Cofense
Cofense is a security awareness platform that centers its training on real phishing threats. When emails slip past secure email gateways, employees can flag them with the Cofense Reporter button. The platform then collects, analyzes, and converts relevant reports into phishing simulations that the wider workforce can be tested against.
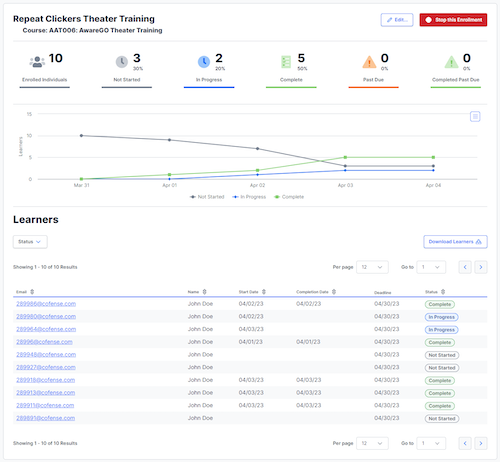
Cofense also draws on a global threat database informed by more than 35 million users, so simulations reflect current attack methods. These include ransomware lures, business email compromise, QR code scams (quishing), and conversational phishing.
Pros of Cofense:
- Real-world relevance: Scenarios reflect actual phishing threats your organization faces, not just generic templates.
- Built-in reporting: One-click reporting boosts engagement and feeds threat intel into your defenses.
- Detailed analytics and dashboards: Offers real-time visibility into user behavior, campaign performance, and risk segmentation.
Cons of Cofense:
- Campaigns require regular upkeep, or employees may grow fatigued by repetition.
- Use cases, features, and pricing are designed for larger organizations, which may feel heavy for small teams or MSPs.
- Exact pricing isn’t available online—you’ll need to contact sales for estimates.
How to choose the right Huntress alternative
Switching from Huntress or weighing your options isn’t just about a list of features. It’s about whether the platform can measurably reduce human risk, fit the stack you already run, and justify the price when you pitch it to leadership. Here’s a practical checklist to guide that decision.
Risk reduction metrics
Look for platforms that go beyond reporting “click rates” on phishing tests. The gold standard is behavioral risk scoring, which means tracking how individuals and teams respond across email, SMS, video, and calls, then showing risk trending down over time.
A great example of this is Adaptive Security’s risk score metric, which maps every user’s response, including who clicked, who reported, and who ignored, into a rolling risk score.
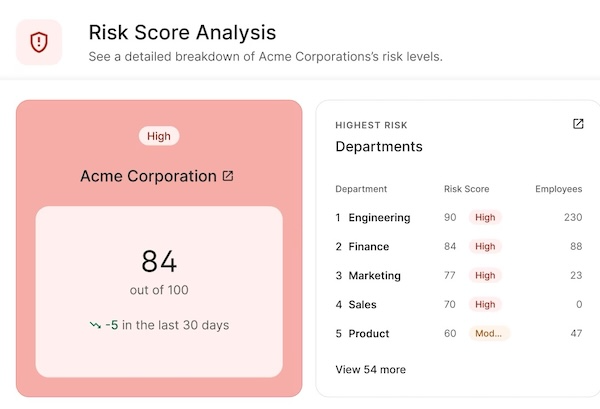
The platform then visualizes that data in clear, audit-ready dashboards, with filters by department, location, or client. This lets IT managers walk into a board meeting and show evidence that high-risk groups are shrinking, low-risk groups are growing, and that training is directly lowering the likelihood of a successful attack.
Integration with SOC + GRC
Training doesn’t happen in a vacuum. The moment an employee clicks a phishing link, your security operations center (SOC) team, security information and event management (SIEM) tool, or governance, risk, and compliance (GRC) system has to respond.
This crew and software stack watches your network, logging suspicious activity, and ensures your company remains compliant with regulations. If your awareness platform doesn’t integrate with those workflows, you’ll be left with CSV exports that no one reads.
Adaptive Security offers open integrations for MSPs that need to feed results into multiple client dashboards. Proofpoint, by contrast, is tightly integrated with its own email security—ideal if you’re committed to its ecosystem—while Cofense channels user-reported phishing directly into SOC playbooks, which supports teams handling day-to-day incident response.
Budget and contract flexibility
Long contracts, rigid seat counts, and annual prepay can make security awareness harder to budget than it should be. Huntress and other SAT vendors often package pricing in ways that don’t scale gracefully for SMBs or MSPs.
Why Adaptive stands out
Most awareness platforms still measure success by click rates. Adaptive takes a different approach, reducing real human risk and preparing teams for the attacks they’re most likely to face right now. That combination makes it one of the strongest modern alternatives to legacy platforms like KnowBe4, Proofpoint, and Huntress.
Outcome-driven case studies
Adaptive trains for the kinds of attacks legacy platforms overlook, including deepfake video calls, voice impersonation, smishing, and other AI-driven threats. It also gives IT teams flexible deployment and measurable risk data.
Mohonk Mountain House, Director of IT, Bron Walis, says this about the platform: “[Adaptive’s] deepfake training capabilities stood out to us, and their work with AI addresses a real threat.”
With automation handling enrollment and reminders, Mohonk hit 100% training completion for the first time, while fail rates dropped to 3% and employees rated the content 4.6 out of 5.
For the Dallas Mavericks, the priority was safeguarding sensitive operations against AI-driven impersonation. CTO Phillip McKibbins described onboarding as “a ‘no pressure’ sale,” with a team that’s “eager to answer any of our questions … and flexible while working through our process.”
Once in place, the Mavericks relied on Adaptive’s personalized deepfake simulations to help employees recognize and respond to sophisticated cyber attacks.
AI/deepfake defense
While phishing emails are still a problem, attackers have shifted to more sophisticated scams, including cloned voices, video calls, SMS, and LinkedIn spear-phishing. Adaptive builds these scenarios directly into training, keeping employees from being blindsided when an attack happens.
Flexible deployment
Every organization trains differently. SMBs want light-touch rollouts, MSPs need multi-tenant management, and enterprises care about integrations with SOC and GRC tools.
Adaptive is designed with that flexibility in mind. It supports modular adoption (e.g., starting with phishing, adding deepfake later), scales pricing up or down as headcount changes, and ties results back to the systems security teams already use.
If you’re evaluating Huntress alternatives, you’re likely looking for a platform that proves ROI, fits your workflows, and prepares employees for today’s AI-driven threats, not just yesterday’s phishing templates.
Adaptive Security checks all the boxes: proving ROI, fitting seamlessly into your workflows, and preparing employees for today’s AI-driven threats. See it in action—book a demo today and discover how Adaptive reduces human risk with customizable, behavior-changing training.




As experts in cybersecurity insights and AI threat analysis, the Adaptive Security Team is sharing its expertise with organizations.
Contents




.avif)





