Most breach and attack simulation tools can indicate how effectively your controls block malware, but few can tell you what happens when the finance lead gets a convincing deepfake call from the company's CEO.
While these tools excel at testing technical controls, they rarely account for the human behaviors that attackers most frequently exploit: phishing clicks, deepfake calls, or misplaced trust in spoofed communications. That gap between technical validation and human behavior is precisely where most breach and attack simulation (BAS) programs fail.
Instead of only simulating how malware moves through networks, modern BAS and security awareness training platforms, like Adaptive Security, simulate how humans respond under real-world social engineering pressure. By modeling human-targeted threats, such as spear-phishing, deepfakes, and voice spoofing, the platform helps organizations validate their systems and their people.
Discover the top five BAS platforms that can help you strengthen your organization's resilience and ward off sophisticated cyber threats.
Technical control validation vs. human risk simulation
Most security teams today have some form of breach and attack simulation running in the background. These tools do what they promise, verifying whether your technical defenses are functioning as intended.
For example, can your endpoint detect malware? Can your firewall block lateral movement? Does your email gateway filter out malicious attachments? While these questions are important, they're also only half the story.
When examining how most real cyberattacks occur, the root cause is often a threat actor exploiting human error and vulnerability, rather than a misconfigured firewall.
Here are some common attack scenarios that organizations face, especially in the modern threat landscape:
- A finance manager gets an email from "the CEO" asking for an urgent payment.
- An HR associate picks up a call from what sounds like the head of IT and shares a password.
- An employee sees a "DocuSign" link and clicks before thinking twice.
According to the Verizon Business 2024 Data Breach Investigations Report, 68% of confirmed cybersecurity breaches involved a "human element," which is defined as non-malicious human errors or people falling for social engineering schemes.

Even if your technical controls are strong, human-triggered events remain a significant risk. And when a breach occurs, the financial stakes are high.
Traditional BAS tools can't really test for that. They can tell you if your endpoint detection and response (EDR) fires when malware runs, but not if your finance lead would wire money to a deepfake voice that sounds like your CEO. That's where new-generation security awareness tools like Adaptive Security help.
Adaptive adds a behavioral layer that sits next to your BAS. It runs human-targeted simulations, such as deepfake phishing audio calls, smishing messages, and realistic executive impersonation emails. These realistic simulations help you determine how your people react in real-time—not in a training environment, but under conditions that mirror actual attack pressure.
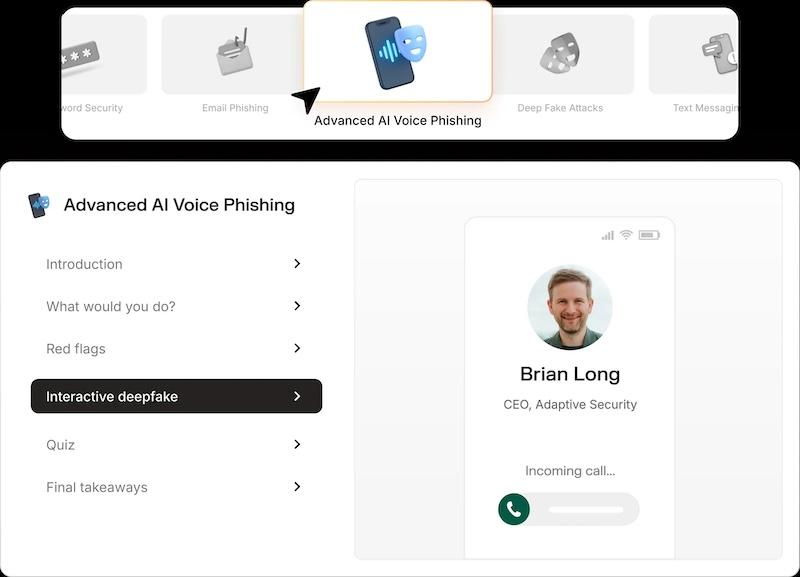
By tracking their responses, Adaptive helps you identify behavioral weak points across teams, roles, and communication channels. You can determine which employees verify before acting, who needs additional coaching, and where your escalation processes break down.
Top 5 breach and attack simulation tools in 2025
Here are five of the most widely used BAS solutions in 2025, compared for what they do best, where they differ, and which gaps they fill.
1. Adaptive Security
Adaptive Security is a next-generation security awareness and BAS platform that simulates human-targeted attacks and drives behavioural change within organizations. Instead of just testing whether your firewalls, endpoints, or email filters can stop attacks, it tests how your people respond when those same attacks target them directly.
Adaptive recreates real-world social engineering scenarios, such as AI-generated voice calls, executive impersonation emails, and fake login pages, to see whether employees recognize and report them or fall for the bait.

Key features and benefits:
- Human-targeted attack simulations mimic real phishing, smishing, voice clone scams, and even deepfake audio to test how employees respond under real-world pressure.
One G2 reviewer shares, "The powerful and efficient simulation feature is particularly impressive, as it creates a jarring and realistic portrayal of potential, effective attacks, which in turn makes my employees more cautious and aware."

- Multi-channel realism covers voice, text, and chat-based lures to simulate modern social engineering.
- AI Content Creator helps build or edit custom training modules in minutes, letting security teams tailor lessons to their company, industry, or department by adding images, quizzes, or custom blocks. Training becomes relevant to each department (finance, HR, tech) and aligned to actual risk.
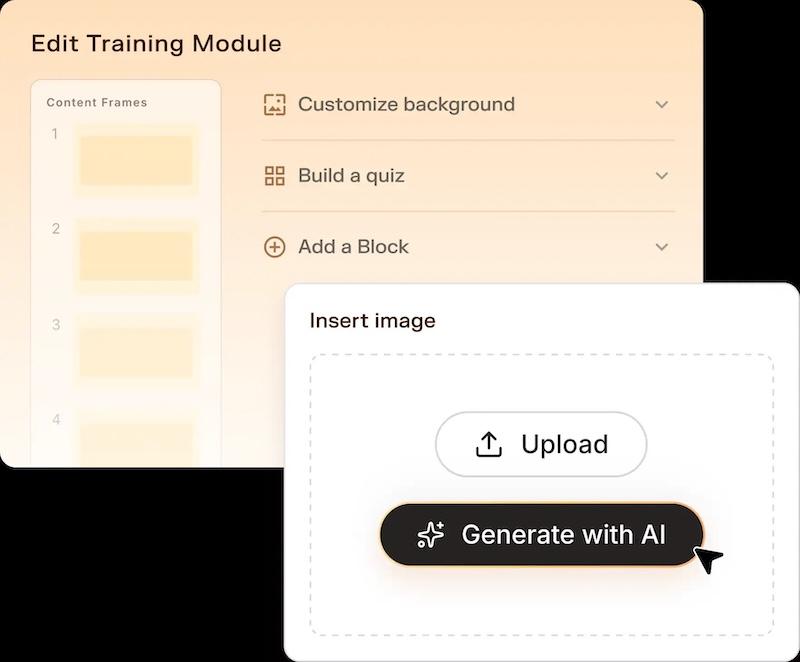
- Smart risk scoring and admin tools assign an employee's risk score based on actions such as phishing clicks, training completion, and job role. It groups people by department, so security leads can see where attention is needed most. The admin tools add access control, bot-click filtering, and clean reporting through an API to keep data accurate and useful.
Limitations:
- It emphasizes human-centric security, but if you skip verifying your firewalls, endpoints, or network segmentation, you'll still have gaps.
2. Cymulate
Cymulate is a mature BAS and exposure-validation platform built for security teams that want to continuously test their technical controls and reduce the risk of real-world breaches. It runs across networks, endpoints, web/email gateways, and cloud environments.
The platform displays results in dashboards, such as the Resilience Overview, which breaks down how effectively your defenses stopped or detected specific, named hacker groups. It also lists the exact attack techniques they used that your tools failed to block, so teams can see where to focus their fixes.

It's best suited for security managers, IT directors, and GRC professionals who need repeatable, data-driven validation of their controls, rather than just one-off penetration tests.
Key features and benefits:
- Full kill-chain coverage simulates phishing emails, lateral movement, web application attacks, and ransomware-style flows to test whether your controls catch them.
- Risk scoring & benchmarking generates a unified risk score (e.g., 0-10 minimal up to 68-100, high risk) based on the latest threat scenarios and control performance.
- Automated and repeatable testing schedules attack simulations daily, weekly, or after major updates. You can choose from ready-made attack types like phishing or ransomware, or build your own using MITRE ATT&CK, a public library of real hacker tactics.
Limitations:
- It excels at validating controls, but less so at modeling human behavior (social engineering, deepfakes) compared with behavioral-layer tools.
- Some users report that advanced simulations or custom templates require more setup or training.
3. AttackIQ
AttackIQ is a BAS platform that helps you determine whether your existing security tools, like EDR, security information and event management (SIEM), firewalls, and email gateways, actually detect and stop real attacks. It tests your existing tools (EDRs, firewalls, SIEMs, cloud configurations) against real attacker behaviors to show where detection or prevention fails in practice.
The company now refers to this capability as Adversarial Exposure Validation (AEV), an evolution of BAS that merges threat intelligence, vulnerability data, and attack-path simulation. In simple terms, it shows how attackers could chain together misconfigurations, vulnerabilities, and weak controls to move through your network.

Key features and benefits:
- Adversary emulation (MITRE ATT&CK) runs simulations based on real threat groups and tactics (credential theft, lateral movement, data exfiltration) to show exactly which tools caught the activity and which didn't.
- Adversarial Exposure Validation (AEV) correlates control validation with vulnerability data and threat intelligence. It identifies how real adversaries would exploit your exact environment and which fixes would make the most significant difference.
- Integrations across the stack works natively with major EDR, SIEM, next-generation firewall (NGFW), and cloud platforms, validating existing investments without disrupting operations.
Limitations:
- It tests systems, not employee behavior. It won't simulate AI phishing, deepfake calls, or other human-targeted attacks.
- Continuous testing generates a high volume of results that require triage and follow-up, so smaller teams may need assistance in managing their output.
4. SafeBreach
SafeBreach has a built-in breach and attack simulation tool called "Validate" that continuously tests how effective your security controls are against real-world attack methods. It's for teams that want to measure how well their existing tools, including EDR, SIEM, firewall, or email gateway, detect, block, or log malicious behavior across the entire kill chain.
Key features and benefits:
- An extensive library of real-world attack methods ("Hacker's Playbook") contains thousands of up-to-date tactics, techniques, and procedures (TTPs) used by known threat actors.
- Automated control validation continuously tests your controls against the latest adversary behaviors to show where detection or prevention breaks down.
- Streamlined remediation workflow means when a test reveals a gap or misconfiguration, the platform automatically surfaces the issue and shares it with the right internal team for fix tracking.
Limitations:
- It doesn't cover human-behavior simulations like phishing or deepfake attacks.
- Teams must map simulations to their unique environment and detection rules.
- Continuous validation generates frequent data; smaller SOCs may need time to operationalize findings efficiently.
5. Pentera
Pentera is an automated security validation platform that continuously tests your organization's defenses across every attack surface, whether it's internal, external, cloud, or identity. Instead of relying on occasional penetration tests, Pentera safely launches controlled attack simulations inside your live environment.
These tests mimic what real attackers do, i.e., exploiting missing patches, misconfigured permissions, leaked passwords, or weak network segmentation. The platform observes which actions succeed, fail, or go undetected, giving teams a realistic picture of what could actually be compromised.

It also focuses on closing the "risk-to-fix" cycle—the time between finding a weakness and proving it's resolved. Pentera automatically assigns ownership for each issue, tracks its remediation status, re-tests the fix, and provides audit-ready proof that the risk is closed.
Key features and benefits:
- Automated, safe attack simulations run non-disruptive tests that imitate real attacker behavior, such as credential theft or privilege escalation, without harming production systems.
- Full-surface validation covers multiple environments through specialized modules, including Pentera Core (internal network), Pentera Surface (external exposure), Pentera Cloud (cloud controls), Credential Exposure (identity and password risks), and RansomwareReady (ransomware containment).
- AI-powered remediation workflows automate the process from detection to resolution, including deduplicating findings, assigning owners, tracking SLAs, and revalidating fixes.
Limitations:
- It focuses on systems and configurations, but it doesn't simulate human behavior attacks, such as phishing or social engineering.
- Several online reviews mention that the reporting could be more customizable, particularly for large-scale enterprise overviews that span multiple environments.
- Smaller organizations might find the full platform more than they need if they lack dedicated security operations resources.
Top 5 breach and attack simulation (BAS) tools in 2025
Key features to look for in a breach and attack simulation tool
Before choosing a BAS platform, it's worth understanding what makes a strong one. Look for these features, so you're not just running one-off tests, but actually improving your organization's resilience:
- Automated attack emulation: Automatically simulate real-world attacker tactics (like ransomware, phishing, or data exfiltration) without requiring constant manual setup.
- Control validation: Ensure that your BAS checks whether your defenses (EDR, SIEM, firewalls, email filters, etc.) actually detect, block, and log attacks as intended.
- Continuous testing: Threats evolve daily. Choose a platform that runs simulations continuously or on a schedule, so you're not relying on outdated, quarterly snapshots of risk.
- Reporting and compliance-ready dashboards: Clear dashboards should show detection/prevention performance, trends over time, and compliance metrics, making it easier to brief stakeholders and auditors.
- AI and threat intelligence enrichment: Advanced BAS tools pull from current threat intelligence feeds or use AI to mirror new adversary behaviors, helping you test against the latest real-world techniques.
- Human behavior simulation: Most real breaches begin with a person clicking the wrong link or trusting the wrong voice. The best BAS platforms now test this layer, not just technology. For example, Adaptive Security simulates deep-fake voice calls, spear-phishing emails, and OSINT-driven attacks to see how employees react under realistic pressure. This helps organizations measure and reduce human-factor risk alongside technical vulnerabilities.
Closing the loop on human and technical threat simulation
Modern security can't rely on a single layer of defense. Validating only your firewalls and endpoint tools gives you a false sense of safety if you don't also test how your people respond when an attacker targets them directly.
The strongest security programs do both. They validate controls to ensure that technology detects an attack, and they validate behavior to determine if employees can recognize and prevent it. Breach and attack simulation tools, such as Cymulate, AttackIQ, SafeBreach, and Pentera, are invaluable for testing technical resilience, but they fall short of the human layer.
Adaptive Security complements traditional BAS by running simulated attacks to test real, human-targeted threats, including phishing, smishing, and deepfake voice calls. Together, these two layers prepare your organization to mitigate system errors and optimize for human judgment.
All in all, the organizations that test both machines and minds are the ones that stay ahead. Your machines are tested daily—your people should be too. Book a demo to see how Adaptive Security closes the gap.
FAQs about breach and attack simulation tools
What is a breach and attack simulation tool?
A BAS tool automatically tests how well your organization's defenses respond to real-world attack techniques. It runs safe simulations, like ransomware, phishing, or lateral movement, to reveal which controls detect or block attacks and where gaps remain.
Instead of waiting for an incident, you gain continuous visibility into how your systems would perform in practice.
Are breach and attack simulation tools only for large enterprises?
Not anymore. While early BAS tools were built for big enterprises, most modern platforms now scale for mid-size organizations, too. Cloud-based setups, agentless deployment, and modular pricing have made BAS accessible even for smaller security teams looking to strengthen detection and response.
How is BAS different from penetration testing or red teaming?
Pen tests and red teams are manual, point-in-time exercises led by experts. BAS platforms automate parts of that process, running repeatable attack simulations daily or weekly. They don't replace pen tests but complement them by continuously validating whether your controls and detections stay effective between manual engagements.
Can BAS tools simulate phishing or social engineering attacks?
Most BAS tools focus on technical controls, like firewalls, endpoints, and cloud configurations. However, new-age tools like Adaptive Security extend into human-risk testing. They simulate phishing, smishing, or deepfake voice scams to see how employees react under realistic pressure, bridging the gap between technical defense and human behavior.
What's the ROI of implementing breach and attack simulation tools?
BAS helps security teams identify and remediate weaknesses before attackers can, often significantly reducing breach risk and incident costs. It also enhances the efficiency of existing security investments, identifying which tools are effective and where adjustments are needed. Over time, continuous validation cuts the cost of surprises and shortens recovery times after real incidents.




As experts in cybersecurity insights and AI threat analysis, the Adaptive Security Team is sharing its expertise with organizations.
Contents










