Phishing powered by AI.
Adaptive delivers realistic, multichannel phishing simulations across voice, SMS, and email.
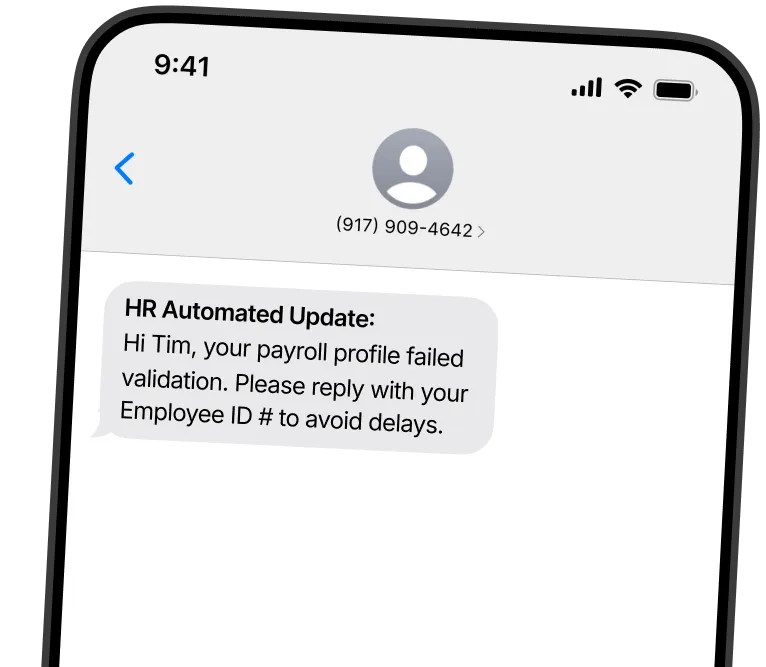



Mirror real-world attacks with simulated BEC, vendor impersonation, malicious attachments, and more.
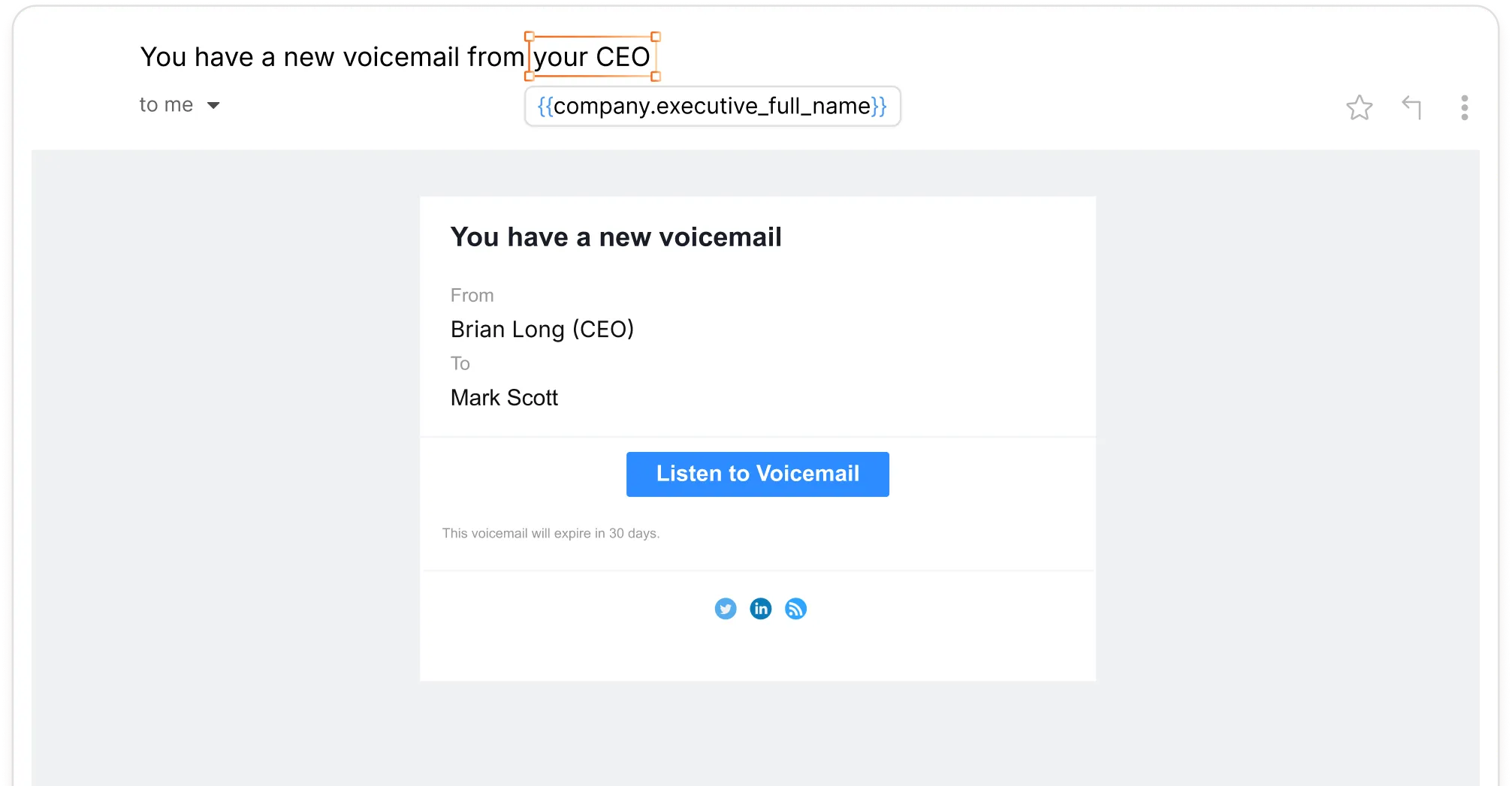
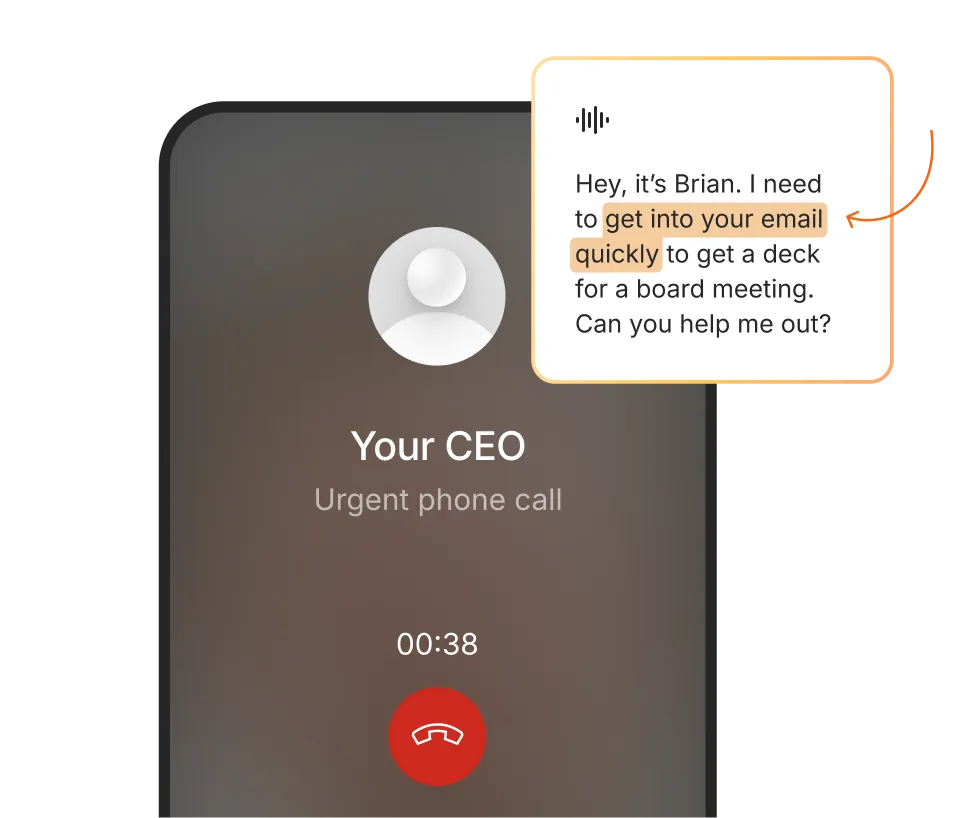
AI-generated voice calls and voicemails use custom personas to create highly convincing vishing scenarios.

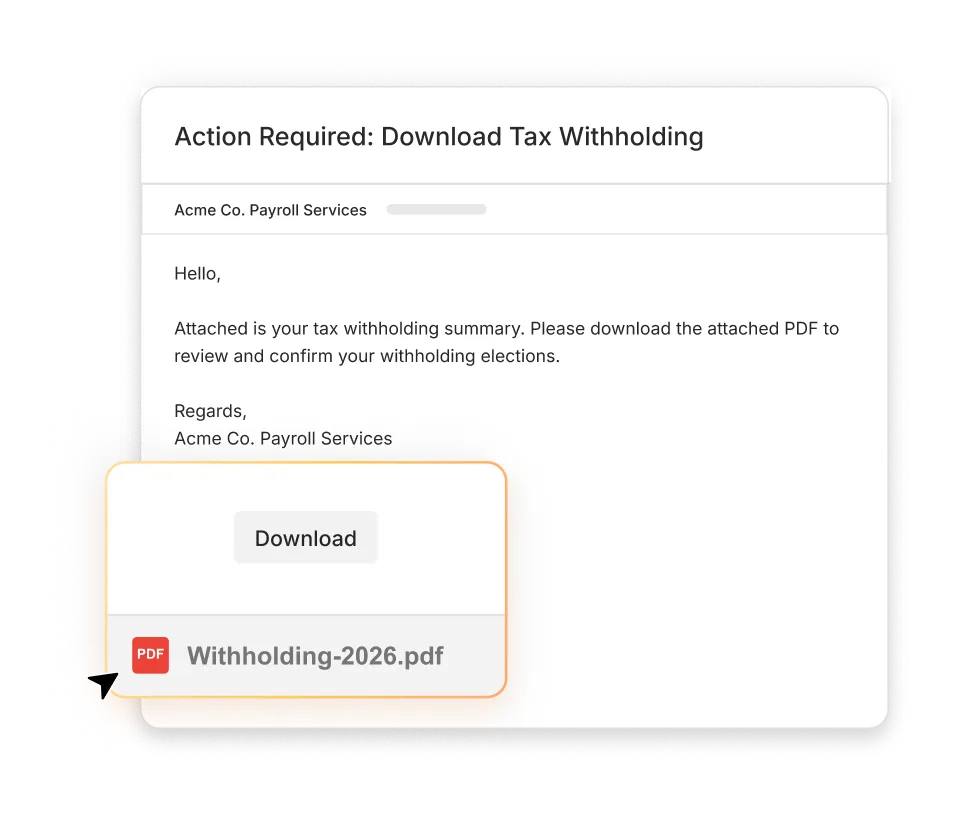
Simulations move across various communication mediums with BEC and vendor impersonation scenarios.

Every part of each simulation from copy to the spoof page and fail screen can be edited and branded your way.

AI and open-source intelligence generate targeted spearphishing emails shaped by your public signals and data.

AI voice personas modeled on your executives deliver convincing calls, voicemails, and callback requests.

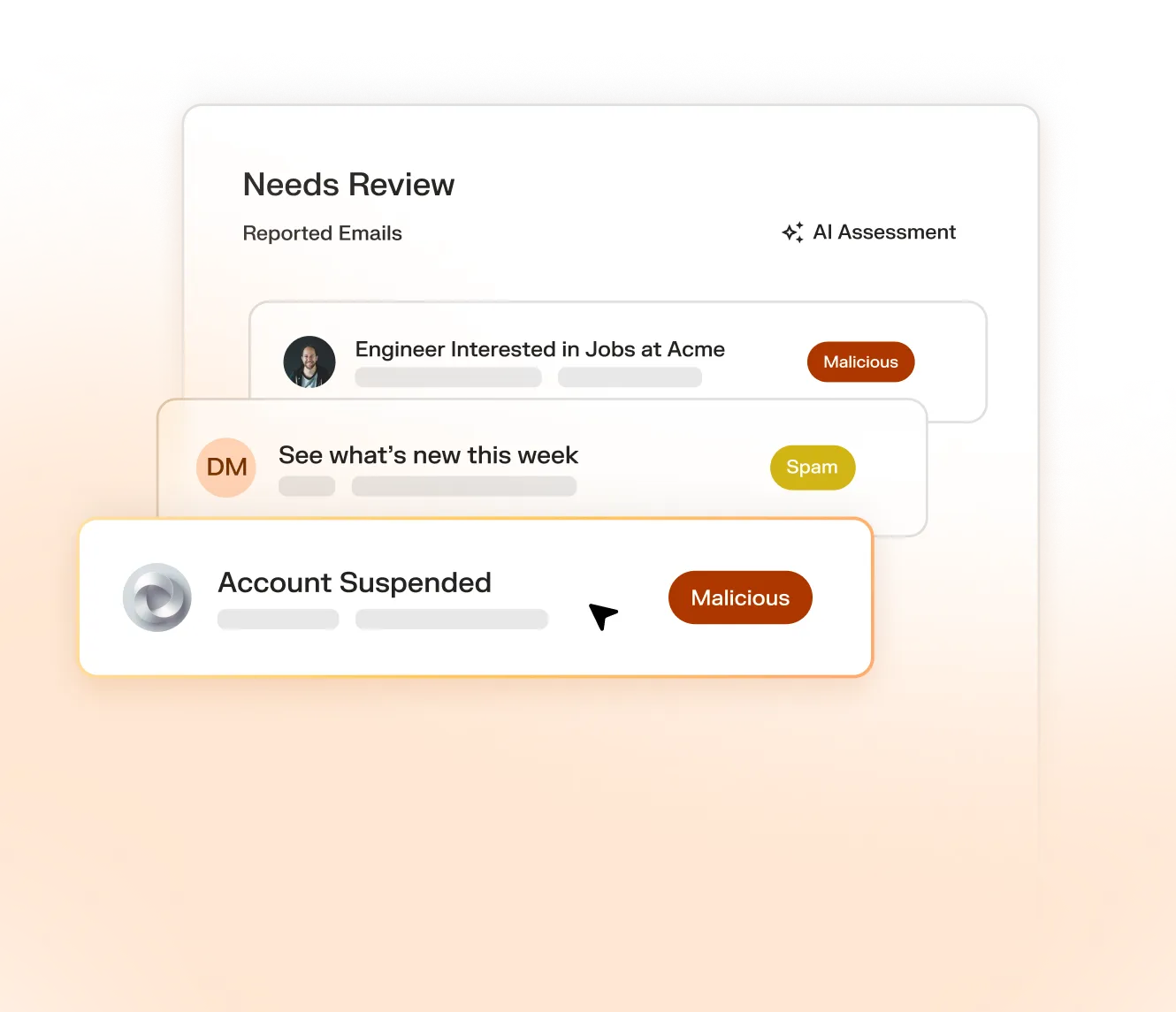
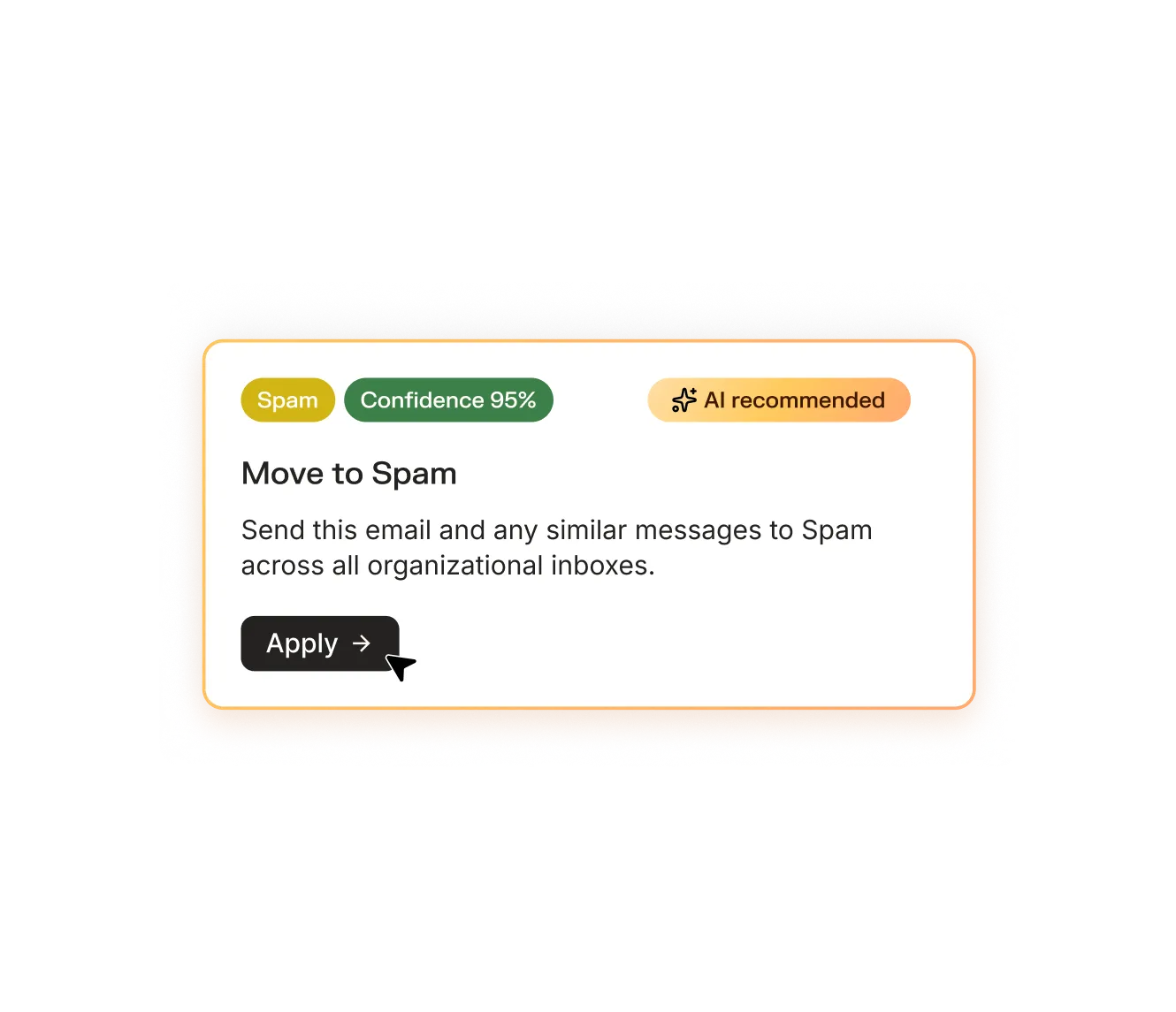
AI-powered phish reporting, triage, and inbox remediation.

Loved by users.
The security awareness platform built for tomorrow’s threats.
Your questions, answered.
A phishing simulation is a controlled test that mimics real-world phishing attacks to evaluate how employees respond. It helps identify risky behaviors, like clicking malicious links or sharing credentials, and turns those moments into training opportunities that improve security awareness over time. Many organizations use phishing simulation platforms like Adaptive Security to run these simulations and provide employees with ongoing training.
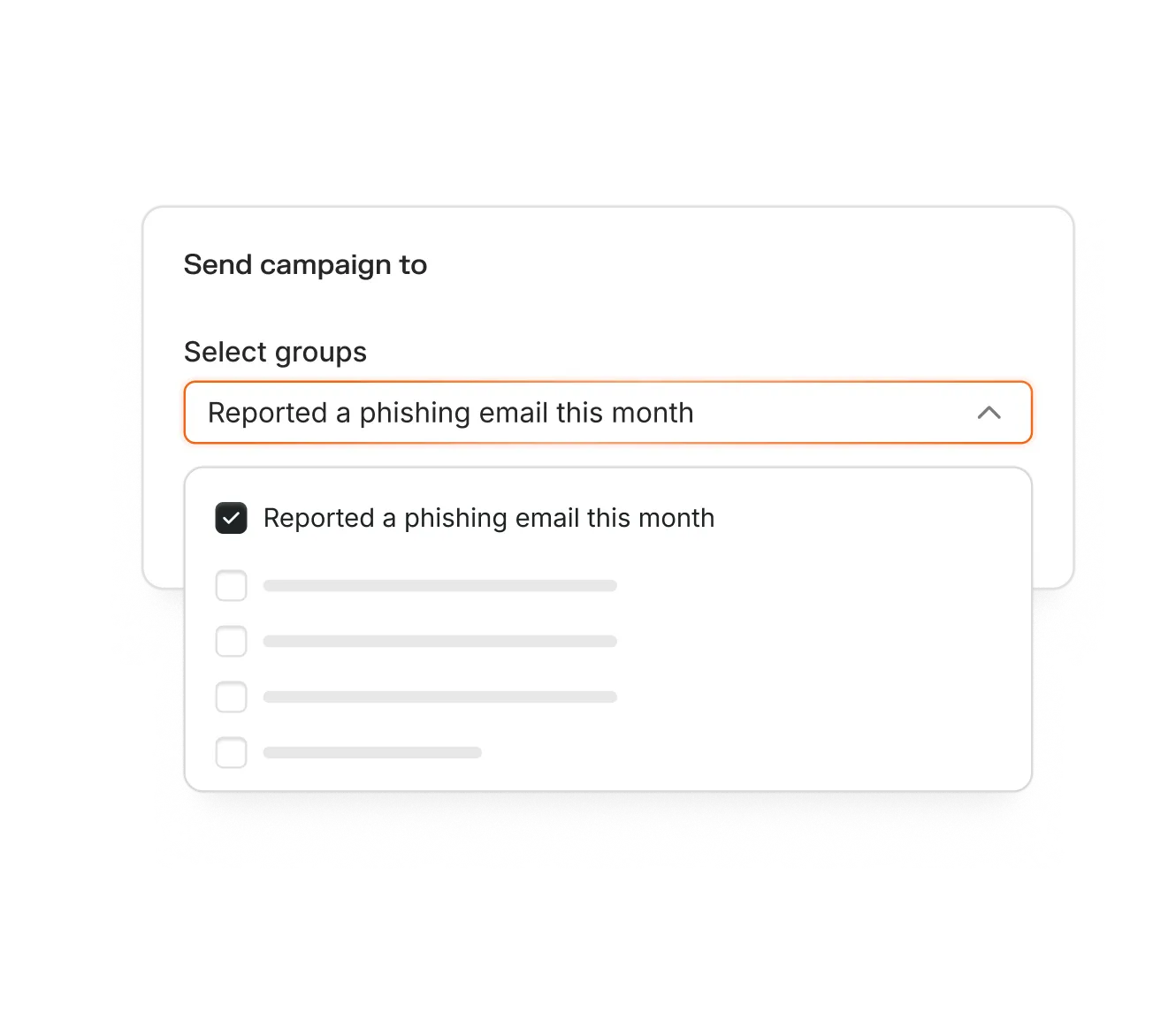
Run phishing simulations at least monthly to build pattern recognition and reduce click rates over time. Increase frequency during onboarding, after incidents, or when rolling out new threat scenarios like AI-generated voice or SMS attacks. Remember, consistent testing drives long-term behavior change.
Yes, advanced phishing simulations on platforms like Adaptive Security now include deepfakes, vishing (voice phishing), and smishing (SMS phishing). These modern formats mirror real-world attack vectors and help employees build resilience against sophisticated, multi-channel threats.
Yes, AI can dramatically improve the accuracy of phishing simulations by generating realistic, personalized attack scenarios using data from public profiles, breached credentials, or typical communication patterns. These AI-powered simulations better mimic real threats, helping teams identify and reduce human risk more effectively.