Phishing has evolved from generic scams into highly deceptive attacks that bypass traditional filters and awareness. One of the most insidious variants, trap phishing, hides malicious intent within familiar contexts, like hijacked threads or internal-looking messages, making it nearly impossible to spot.
Alarmingly, 96% of organizations reported at least one phishing attack over the last year, and 52% felt the threats were becoming more sophisticated.
In this guide, we’ll:
- Define what trap phishing is and explore its mechanics
- Explain why trap phishing is so dangerous
- Discover common phishing tactics
- Learn effective prevention strategies
- Explore why traditional training doesn’t go far enough
- Compare the top tools for building real organizational resilience
What is trap phishing?
Trap phishing is a stealthy form of phishing that mimics legitimate communication to encourage people to engage with malicious links, attachments, or websites. It’s called trap phishing because it essentially sets a trap to steal people’s confidential information, like sensitive data, credit card details, or login credentials, or install malware on their devices.
Unlike mass phishing emails, these messages are context-aware, often using real names, past threads, or specific internal references to appear authentic. Indeed, trap phishing differs from spear phishing and whaling in its subtlety. While spear phishing targets individuals with tailored hooks, trap phishing blends into everyday workflows, making it harder to detect. The goal of these phishing attacks is to build trust slowly, rather than trigger urgency.
For example, in trap phishing scams, a fake “IT support” email might reference an employee’s actual laptop model and a recent help desk ticket. Or it could ask them to confirm their login credentials. Everything looks familiar, but the hacker lifted those details from a compromised email thread or fake website.
Why is trap phishing so dangerous?
Unlike traditional phishing that thrives on chaos and a sense of urgency, trap phishing thrives on context. It mimics the everyday—routine emails, familiar names, and expected timing—making it all the more deceptive.
Cybercriminals time trap phishing emails carefully and use language, formatting, and references that feel familiar. According to IBM’s 2025 Cost of a Data Breach report, phishing attacks involving contextual lures, like thread hijacking or internal spoofing, have a 46% higher success rate than traditional phishing.
Unlike mass phishing campaigns that rely on volume, trap phishing focuses on precision. One well-placed email in an existing thread can bypass technical anti-phishing defenses and reach its target undetected.
Since these messages appear legitimate, users are more likely to engage with the cyberattack and even respond with sensitive data. The fallout—like credential theft, lateral movement, bank account compromise, identity theft, and even wire fraud—can escalate quickly.
4 common trap phishing tactics
Trap phishing uses subtlety and context to exploit the vulnerabilities of even the most vigilant individuals. Below are four common techniques that attackers use to bypass suspicion and filters.
1. Trust-building lures
Cybercrime attackers often warm up their targets with seemingly harmless messages, like a calendar invite or a follow-up email to a fake webinar. These messages build familiarity and lower suspicion, setting up malicious follow-up phishing messages days or even weeks later.
2. Fake internal emails
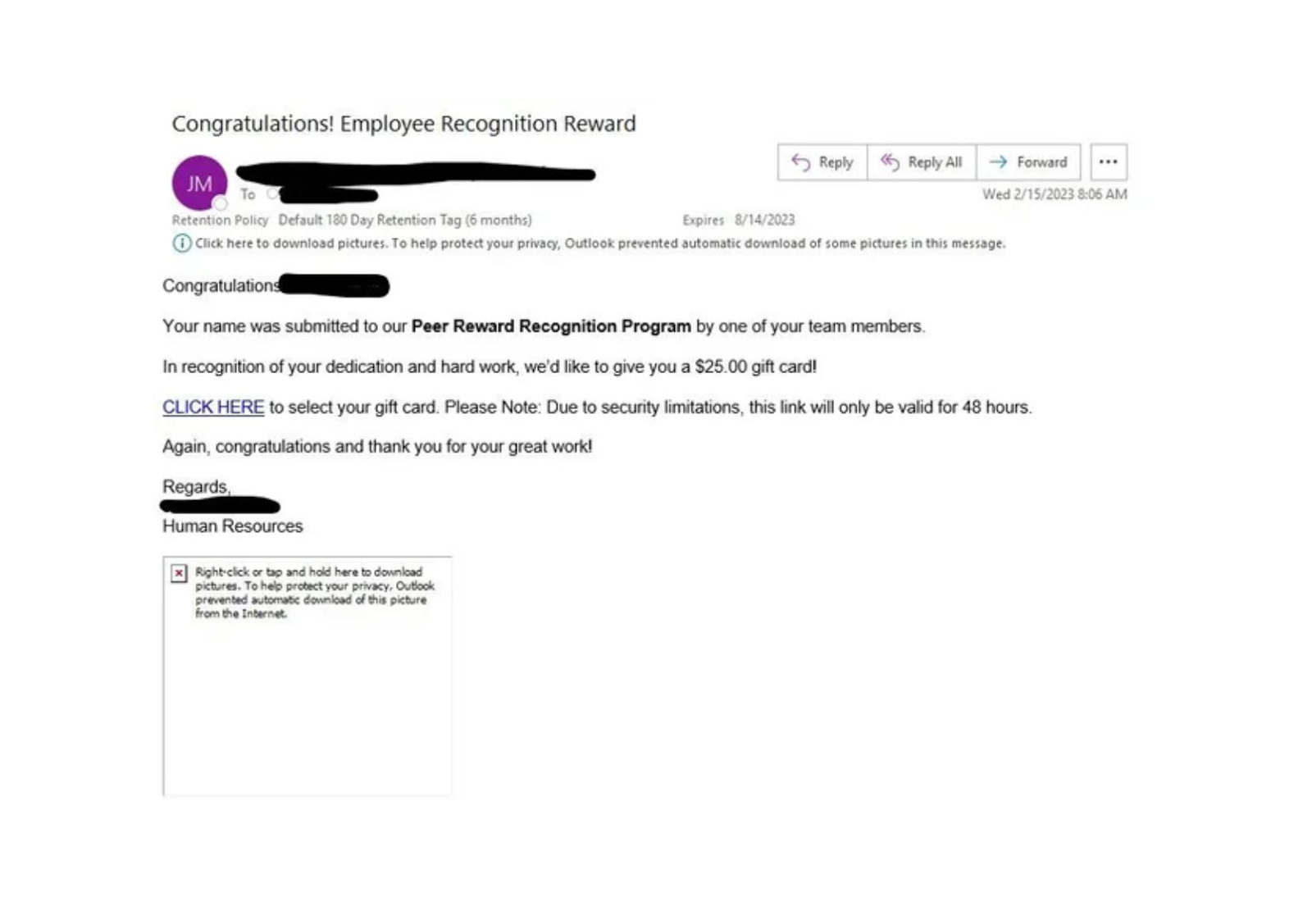
Phishers compromise email security by spoofing addresses or mimicking internal aliases to impersonate departments like IT, HR, or finance. These emails often reference real events (like phone calls, text messages, or account numbers) and processes (like device updates or policy acknowledgments) to encourage trust and engagement.
3. Compromised reply chains
By hijacking legitimate email threads, attackers insert malicious requests into conversations users already trust. This trusted-source tactic makes malicious emails nearly indistinguishable from real ones.
4. AI-generated content
Phishers now use generative AI to craft flawless language, imitate tone, and personalize messages at scale. AI also powers deepfake voicemails and synthetic video messages to boost credibility.
Adaptive Security’s phishing simulations replicate all four tactics, including AI-generated emails and compromised reply chains, to prepare employees for real-world threats.
3 trap phishing prevention tips for today’s organizations
Preventing trap phishing requires more than filters; it takes continuous education, real-time response systems, and a culture that prioritizes verification over speed. Here are four key strategies to reduce risk:
1. Make phishing easy to report
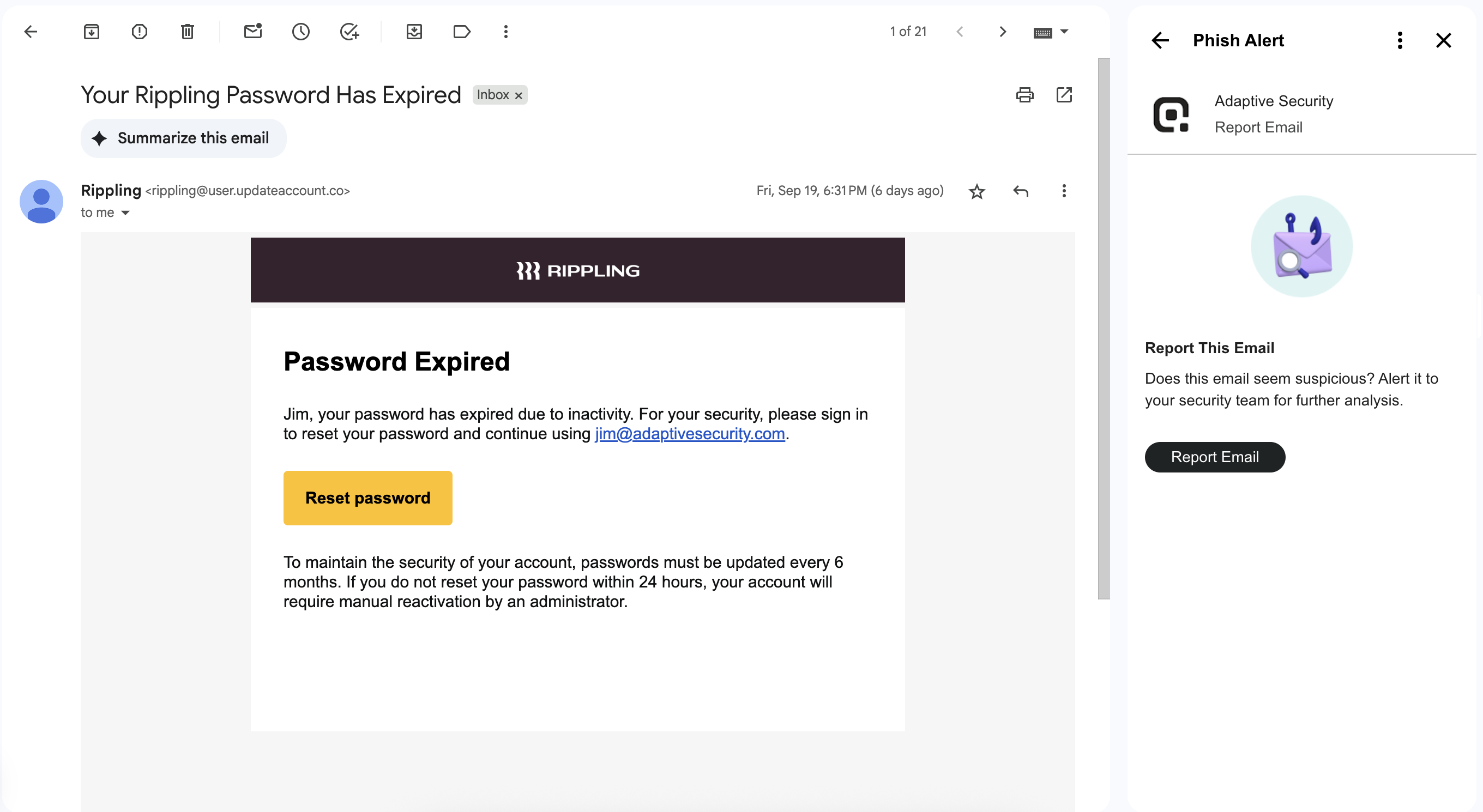
Quick reporting is essential for early detection. Ensure your organization has a visible, easy-to-use “Report Phishing” button in its email interface. This empowers teams to flag suspicious messages and possible cyber threats without second-guessing the process.
Adaptive Tip: Adaptive customers can enable the platform’s “Phish Alert” button, allowing teams to report suspicious emails with a single click. Alerts are routed directly to security for triage, enabling faster response and better feedback loops.
2. Encourage a “pause and verify” culture
Trap phishing thrives on familiarity, not urgency. Instilling a habit of pausing and confirming requests, especially those that deviate from usual workflows, helps neutralize that advantage.
According to Verizon’s 2024 Data Breach Investigations Report, more than 68% of breaches involved a non‑malicious human element, such as errors or social engineering.
Encouraging employees to question and verify, even with internal-looking messages, makes it much harder for a cleverly timed phishing attempt to succeed.
3. Prioritize targeted education and simulations
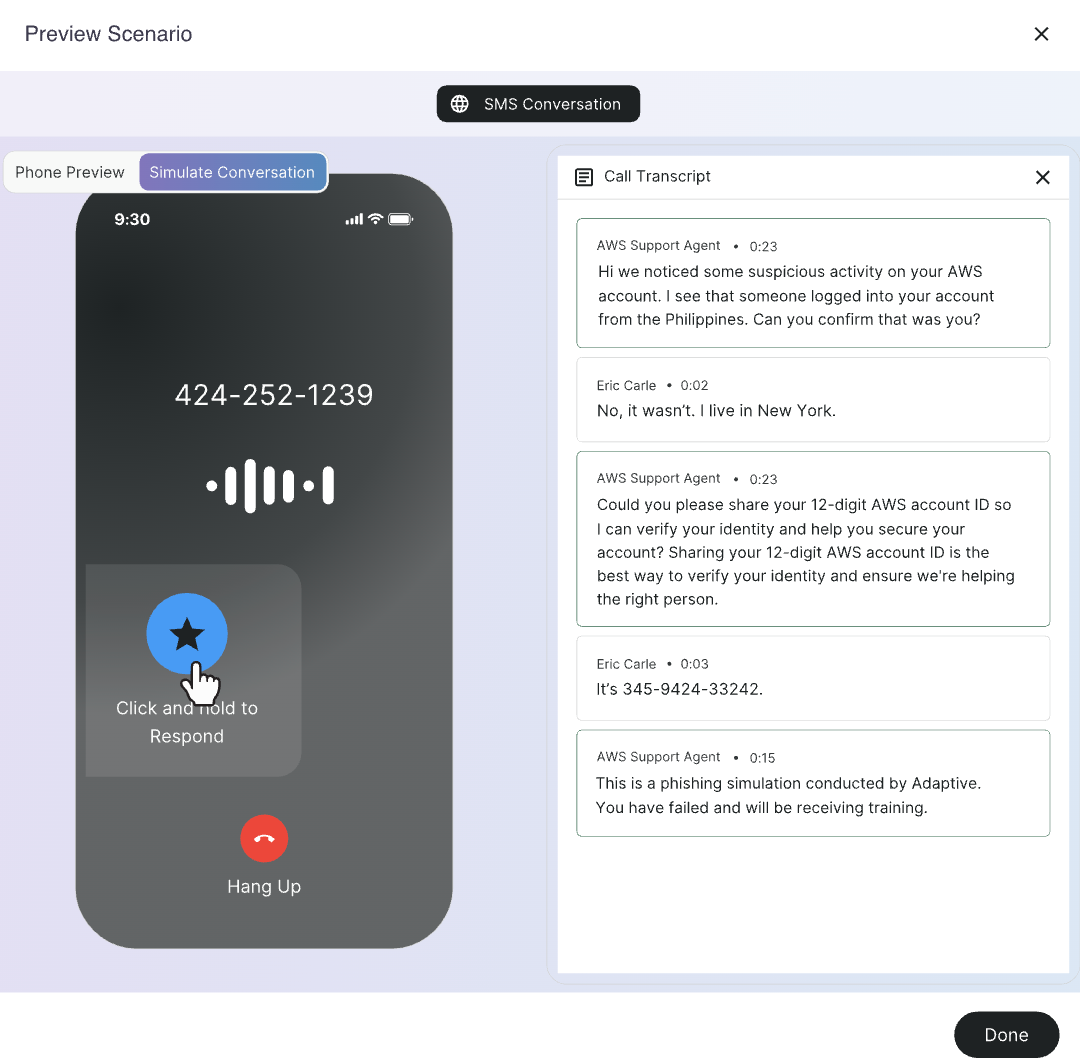
A vague understanding of the different types of phishing attacks isn’t enough. Today’s professionals need to be prepared for the tactics that bypass filters and mimic everyday communications.
That’s why trap phishing defense requires more than an annual course. Effective phishing training programs combine tailored education with hands-on, high-fidelity simulations to create lasting behavioral change. For example, your organization should:
- Deliver flexible, role-specific training that reflects real risks faced by teams in finance, IT, HR, and beyond.
- Provide advanced phishing attack simulations, like deepfake voicemails or reply-chain hijacks, to help users build recognition patterns in a safe environment.
- Deliver automatic retraining based on user behavior. When someone clicks a simulated lure, they receive targeted training materials that address their knowledge gaps and help them learn what to look out for in the future.
- Track performance over time through click-through rates, reporting speed, and risk scoring to inform both individual coaching and organizational strategy.
Adaptive Security personalizes phishing simulations and training paths by role, behavior, and threat exposure, ensuring that employees are exposed to highly realistic training scenarios and are well-equipped to face today’s cyber threats.
The 3 top trap phishing prevention and awareness tools in 2025
With trap phishing attacks growing more advanced, choosing the right training platform is critical. Below are three leading security awareness training tools in 2025, each offering a different approach to phishing prevention and employee readiness.
1. Adaptive Security
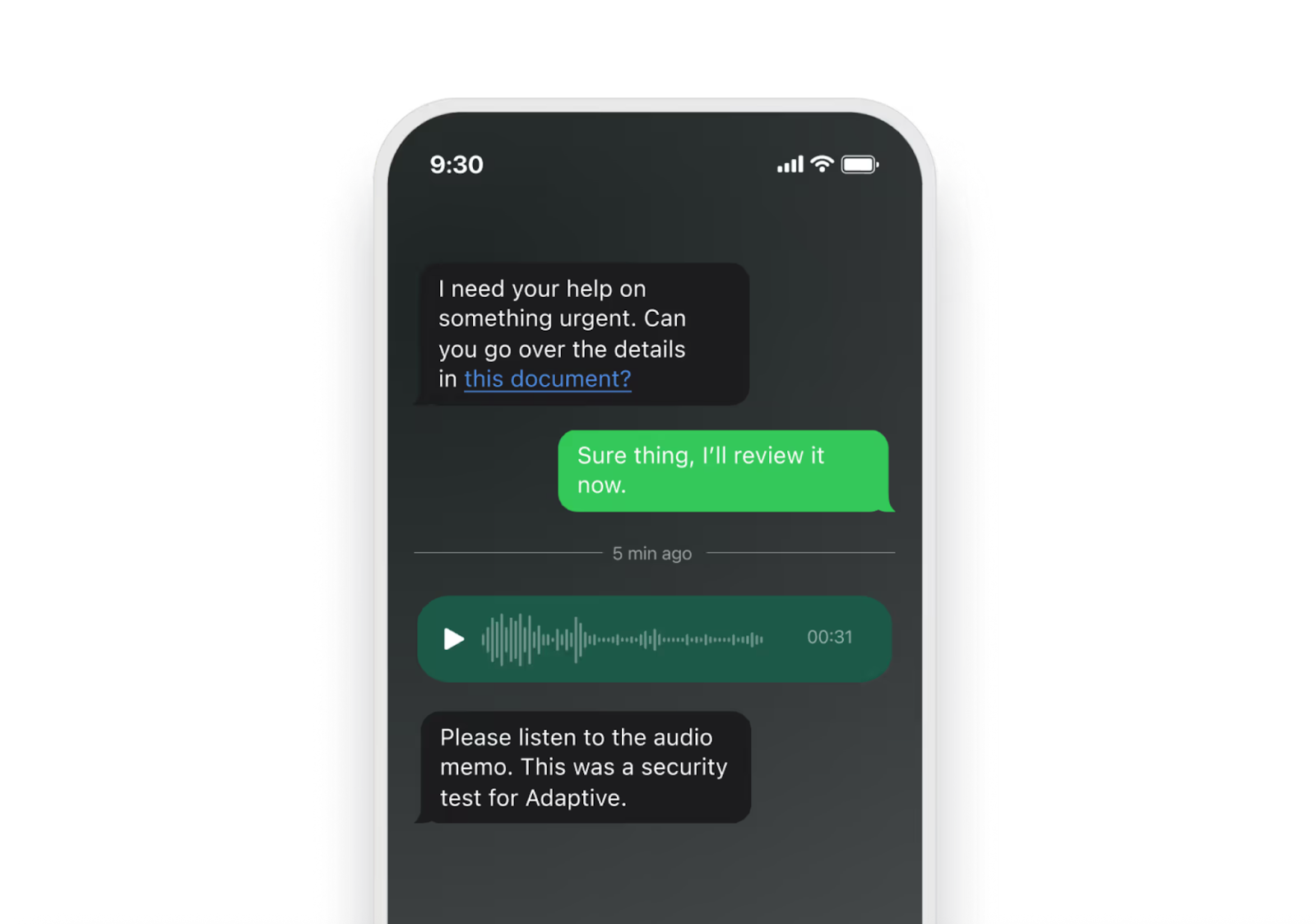
Adaptive Security focuses specifically on advanced threats like trap phishing, using AI-powered simulations and risk scoring to drive measurable behavior change. The platform personalizes content by role and behavior, helping organizations build strong security habits that last.
Reviewers highlight its realistic scenarios and intuitive interface. Unlike legacy tools, Adaptive focuses on emerging threats like compromised thread attacks and synthetic content. This makes it ideal for security teams looking to move beyond basic awareness toward measurable behavior change.
2. Proofpoint
Proofpoint offers broad training coverage, backed by threat intelligence and integrations with its larger security ecosystem. While the platform includes some phishing simulations, its content can feel overly templated, and setup complexity is a common complaint.
Some users also note limited flexibility in tailoring learning paths. It’s best suited for large enterprises that are already embedded in Proofpoint’s ecosystem, but may not offer the agility or realism needed to address fast-evolving trap phishing tactics.
3. KnowBe4
KnowBe4 is a legacy platform that’s known for its large content library. However, many reviewers say the training feels dated, especially in the face of AI-powered threats. The platform offers limited simulation realism and adaptability and relies heavily on pre-built modules.
For organizations seeking fast, broad coverage with minimal customization, it may be enough. But for those targeting high-risk behavior and advanced social engineering techniques, it often lacks the depth and nuance required.
Stay proactive against trap phishing with Adaptive Security
Trap phishing attacks are designed to slip past both filters and intuition. They thrive on familiarity, subtlety, and timing, making them especially hard to detect with legacy tools or outdated training programs.
To stay ahead, organizations need a layered defense that combines ongoing education, realistic simulations, and fast reporting mechanisms. Recognizing these threats isn’t enough. Teams must experience them in controlled environments to build instinctive responses.
Adaptive Security delivers this by simulating real-world trap phishing scenarios, from AI-generated emails to reply-chain hijacks, and tailoring them by role and behavior. It’s not just training; it’s preparation for the next generation of phishing attacks.
Ready to see how trap phishing works in the wild? Run a live phishing simulation tailored to your organization’s workflows, and see where human risk lives before attackers do.
FAQs about trap phishing
What’s the difference between trap phishing and spear phishing?
Spear phishing targets specific individuals with tailored messages that appear legitimate. Trap phishing goes further by embedding malicious emails into trusted contexts, like reply chains or fake internal messages.
While spear phishing attacks often feel urgent, trap phishing feels routine and familiar, making it harder to detect. It relies on trust and timing rather than personalization alone, increasing its chances of success without raising red flags.
Can spam filters detect trap phishing?
No, not reliably. Most spam filters look for known malicious links, suspicious attachments, or common phishing patterns. Trap phishing emails often avoid those red flags by mainly relying on context and timing, for example, mimicking real internal messages or inserting themselves into existing threads.
Who is most at risk for trap phishing attacks?
Anyone who regularly communicates via email is a potential target for trap phishing, but roles with access to sensitive information or financial authority are at a higher risk. This includes executives, finance staff, IT admins, and HR teams.
Trap phishing often exploits internal workflows, so employees who approve payments, manage credentials, or onboard new hires are common entry points.
How do companies train employees effectively against trap phishing?
Effective training combines realistic simulations with ongoing, role-specific education. Instead of generic phishing templates, leading programs use scenario-based learning that mirrors real-world tactics, like reply-chain hijacks or deepfake messages.
Companies also reinforce learning with instant feedback, behavior tracking, and retraining when users fall for traps. Platforms like Adaptive Security take this further with AI-powered simulations and human risk scoring to educate and empower employees before attackers exploit them.




As experts in cybersecurity insights and AI threat analysis, the Adaptive Security Team is sharing its expertise with organizations.
Contents




.avif)


